SM9 private key generation and use method and system
A private key and generator technology, applied in the field of information security, can solve problems such as inability to obtain encrypted data, inability to decrypt plaintext data, leakage, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
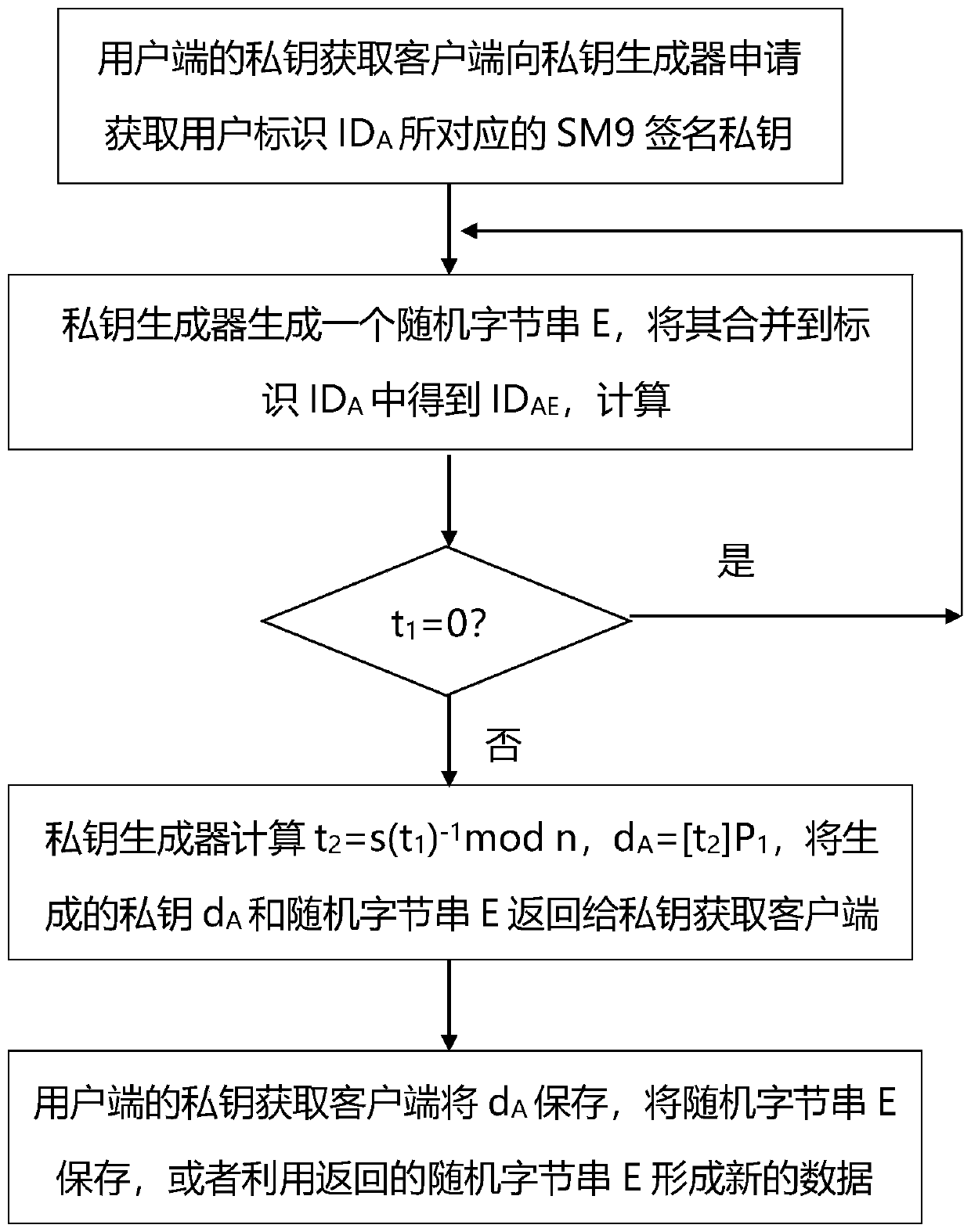
[0050] In this example, if figure 1 As shown, when the private key of the client is obtained, the client applies to the private key generator to obtain the user ID A When the corresponding SM9 signs the private key, the private key generator generates a random byte string E and merges it into the identification ID A Get the ID from AE ; calculate t 1 =(H 1 (ID AE ||hid, n)+s)mod n, where n is the group G in the SM9 algorithm 1 , G 2 , G T order, hid is the private key generation function identifier represented by one byte (see SM9 specification); if t 1 =0, then regenerate random byte string E and merge it into ID A ID AE , calculate t 1 =(H 1 (ID AE ||hid, n)+s) mod n, until t 1 ≠0, where s is the master private key or master key; if t 1 ≠0, calculate t 2 =s(t 1 ) -1 mod n,d A =[t 2 ]P 1 , where P 1 It is group G in SM9 1 The generator; the private key generator will generate the signature private key d A and the random byte string E (or the identificat...
Embodiment 2
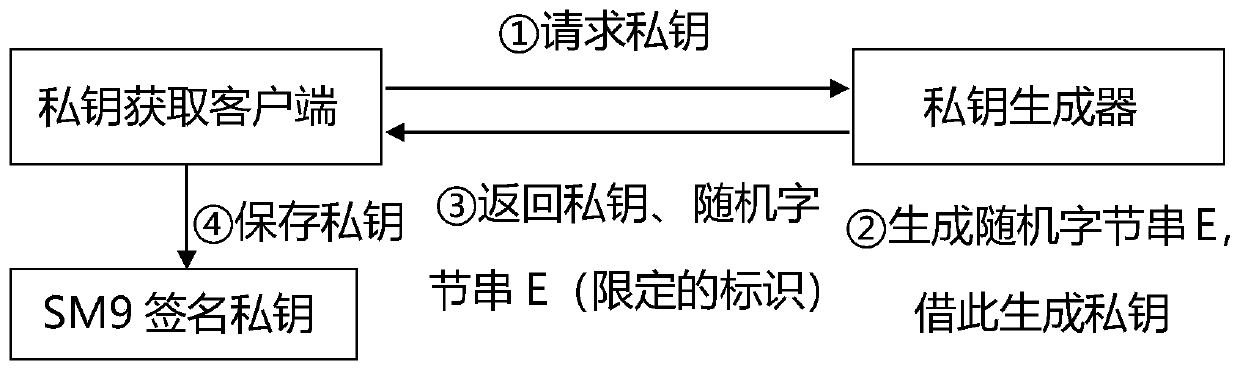
[0062] This embodiment is an SM9 private key generation system based on the SM9 signature private key generation method of the present invention, as figure 2 As shown, the private key generation system includes a server-side private key generator and a user-side private key acquisition client; when the user-side private key acquisition client requests the private key generator to obtain a user ID A During the corresponding SM9 signature private key, the private key generator generates the user identification ID by the SM9 signature private key generation method of the present invention A The corresponding SM9 signature private key is saved by the private key acquisition client.
Embodiment 3
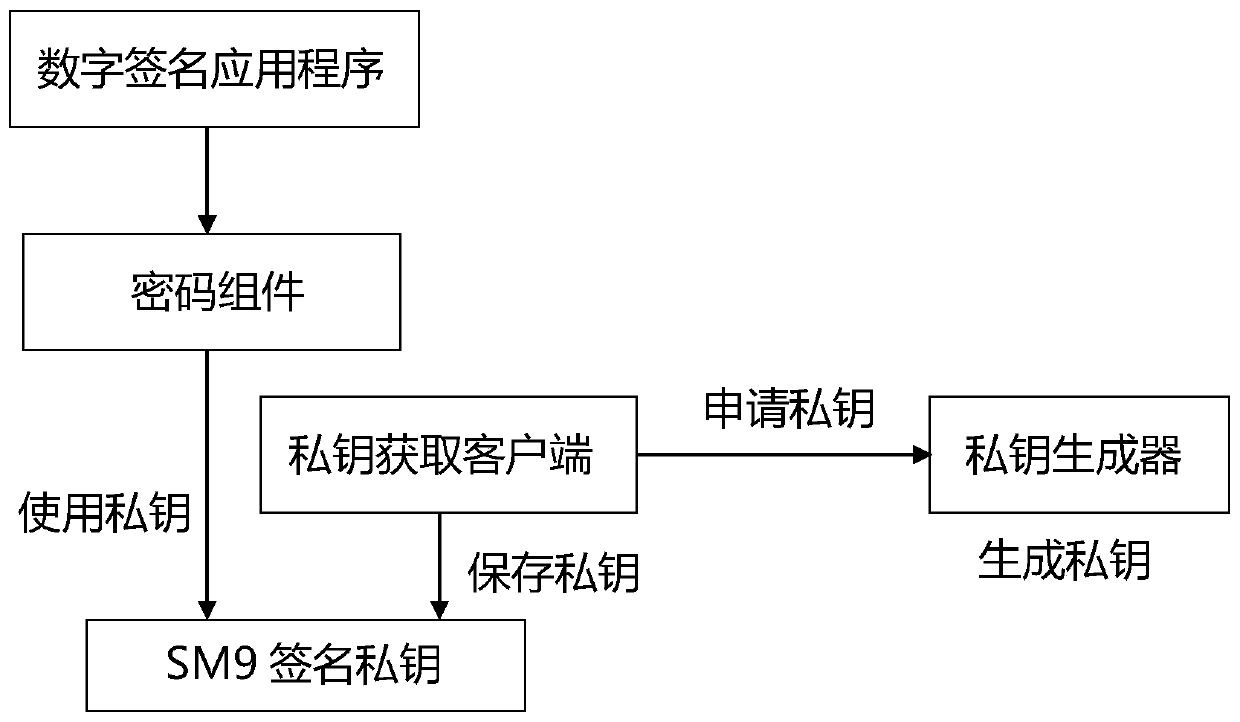
[0065] This embodiment is to use the SM9 signature private key generated by the aforementioned SM9 signature private key generation method to digitally sign the application of the message, specifically:
[0066] When digitally signing a message, the cryptographic component (of the signer) uses the SM9 signature private key d generated by the SM9 signature private key generation method described A digitally sign the message;
[0067] When verifying the digital signature of the message, the cryptographic component (of the verifier) uses the identification ID that incorporates (or contains) the random byte string E AE (by ID AE as the public key) to verify the digital signature of the message.
[0068] In order to make the cryptographic component for signature verification obtain the identification ID that combines the random byte string E required for signature verification AE , the cryptographic component uses the SM9 signature private key d A The signed data (SignedData)...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com