Malicious domain name detection method based on knowledge graph
A technology of knowledge graph and domain name detection, which is applied in the field of network security, can solve the problem that the static blacklist strategy cannot be flexibly expanded, and achieve the effect of rich dimensions, complete information, and improved accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
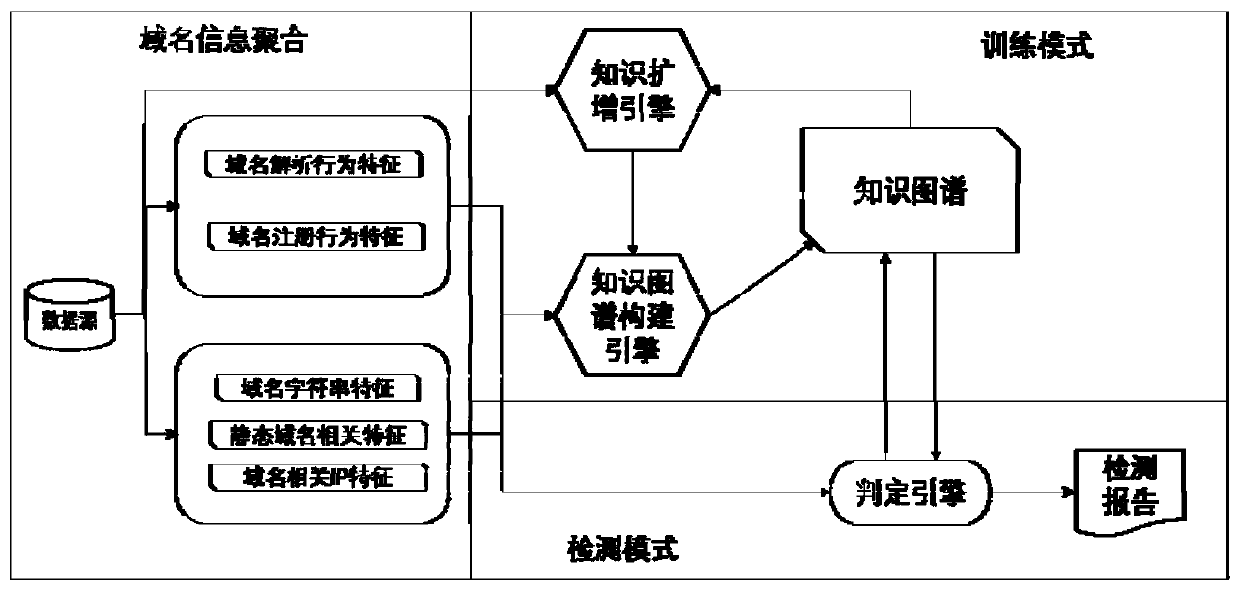
[0034] The present invention provides a malicious domain name detection method based on knowledge graph, such as figure 1 shown, including the following steps:
[0035] S1. According to the characteristics of the domain name information, extract the key features that can be used to construct the domain name reputation knowledge map;
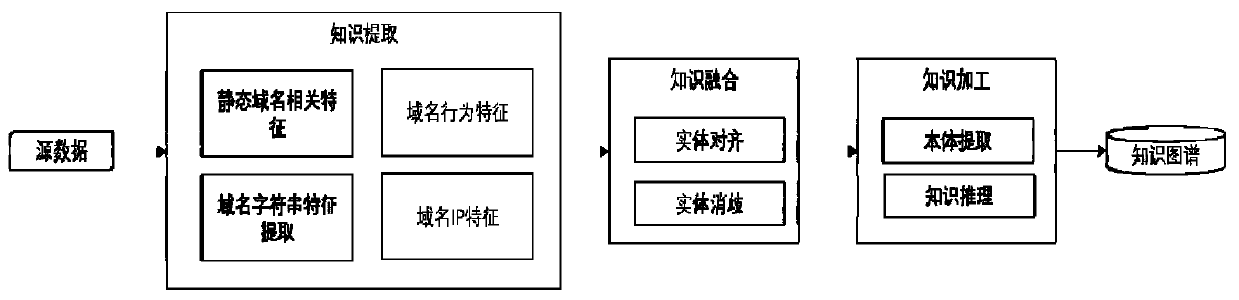
[0036] S2. Aggregation of domain name information: use the obtained existing data to maximize the integration of information contained in the domain name, and provide data sources for the creation of knowledge graphs; data through the knowledge graph construction engine, amplify domain name knowledge from the perspective of data mining; knowledge The map construction engine uses the obtained domain name data to construct a domain name reputation knowledge map;
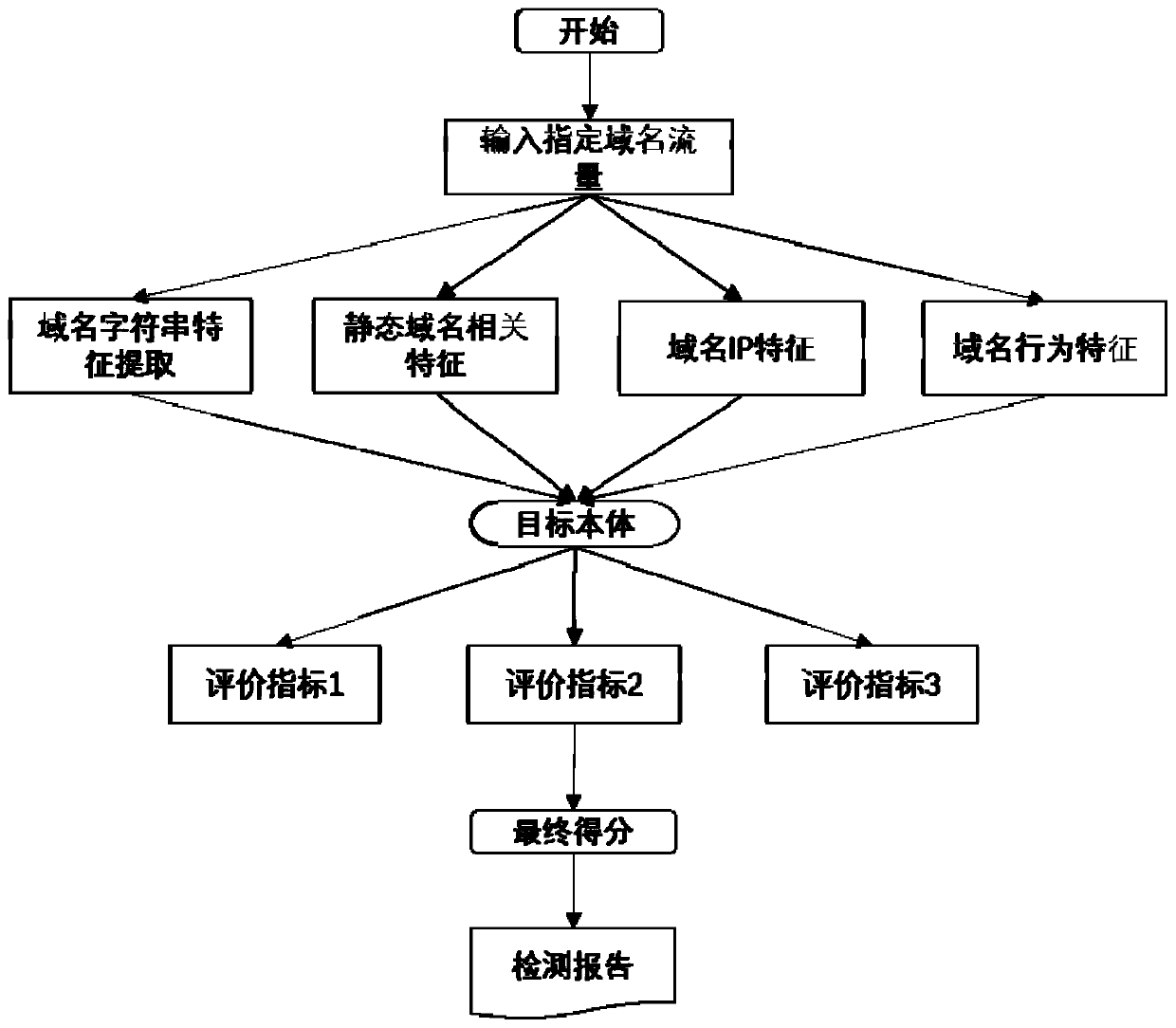
[0037] S3. For a given specific domain name, use the fusion of multi-source information and multiple methods to determine the model to give a prediction result, and at the same time feed...
Embodiment 2
[0061] This embodiment provides a method for detecting malicious domain names based on knowledge graphs. The operation of this system requires the support of domain name data. First, the source of the data is given. Domain name data is obtained from the four aspects in Table 1. Possible data sources include regional Internet registries, major Internet service providers, domain name registrars, domain name popularity evaluation websites, and open lists of malicious domain names. The regional Internet registry provides the system with the necessary domain name and IP static data information; the major Internet service providers provide the system with historical and real-time domain name resolution records, and support the analysis of domain name resolution behavior; the domain name registrar provides the system with new domain name registration Data to support the analysis of domain name registration behavior; the domain name popularity evaluation website provides positive sampl...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com