A defense and network security device against distributed attacks based on big data
A network security and distributed technology, which is applied in the field of defense and network security devices, can solve the problems of effective defense and counter attack, and achieve the effect of preventing DDoS attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
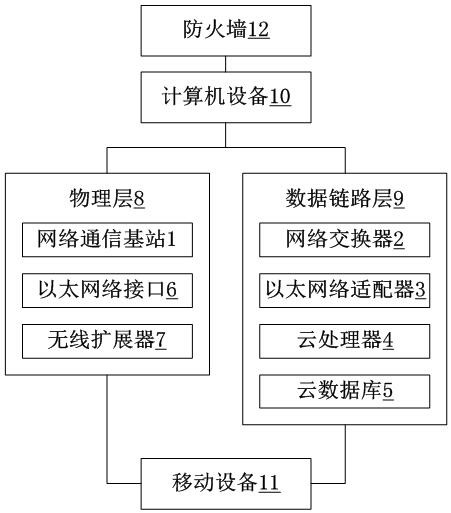
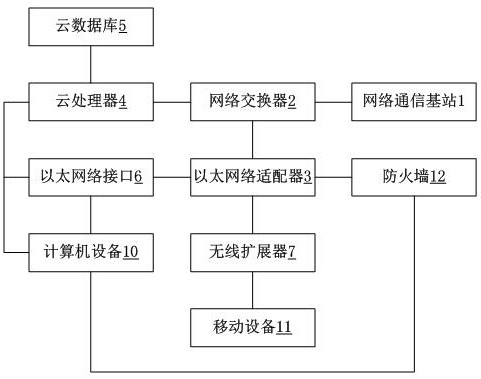
[0023] The reference picture is Figure 1-2 . A defense and network security device against distributed attacks based on big data, used for defense against distributed attacks on the Internet, including network communication base station 1, network switch 2, Ethernet adapter 3, cloud processor 4, cloud Database 5, Ethernet interface 6, wireless extender 7, described network communication base station 1, Ethernet interface 6 and wireless extender 7 are included in physical layer 8, described network switch 2, Ethernet adapter 3, cloud processor 4 and the cloud database 5 are included in the data link layer 9, the Ethernet interface is used to connect the wired network of the computer equipment 10, and the wireless extender 7 is used to search for mobile equipment 11 in the area in a wireless transmission mode, The mobile device 11 accesses the network communication base station 1 at the same time, and the cloud processor 4 searches for the mobile devices 11 in the area obtaine...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com