SDN-based source address authentication method
An authentication method and source address technology, applied in the computer field, can solve problems such as lack of global control, poor computing power, and IP address masquerade attacks, and achieve the effect of improving communication security and performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0031] The technical solution of the present invention will be described in further detail below in conjunction with the accompanying drawings.
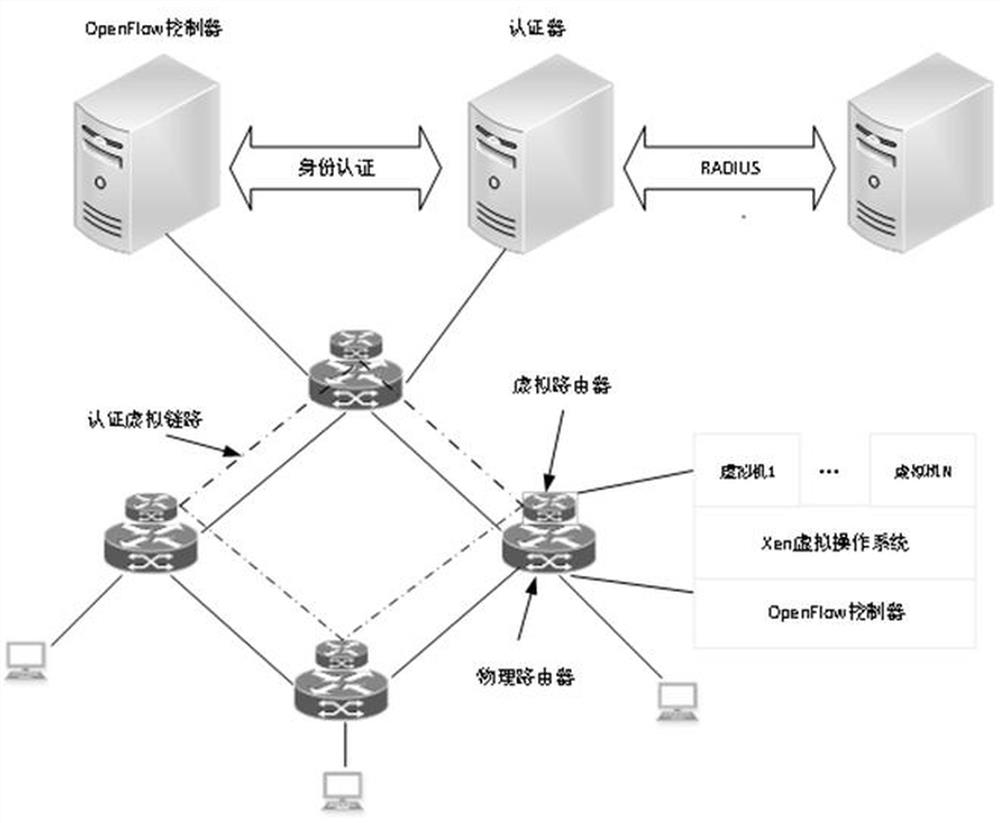
[0032] As attached to the manual figure 1 , as shown in the system architecture diagram based on the SDN source address authentication method of the present invention, the system architecture based on the SDN source address authentication method of the present invention is mainly divided into four parts: OpenFlow controller, certificate authenticator, RADIUS server and SDN network.
[0033] The OpenFlow controller adopts FloodlightV1.2, an open source controller developed by BigSwitch Company, and host access management applications and topology management modules are mainly deployed on the controller. The host access management application program is an upper-layer application that communicates with the controller through the northbound interface. It mainly manages the authority of the terminal to access network resources, and manag...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com