Method for verifying legality of software use right
A technology of right to use and legality, applied in the fields of instruments, computing, electrical digital data processing, etc., can solve the problems of heavy losses of the licensor, illegal use of software, illegal authorized use of software, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] The technical solutions of the present invention will be further described below in conjunction with the accompanying drawings and through specific implementation methods.
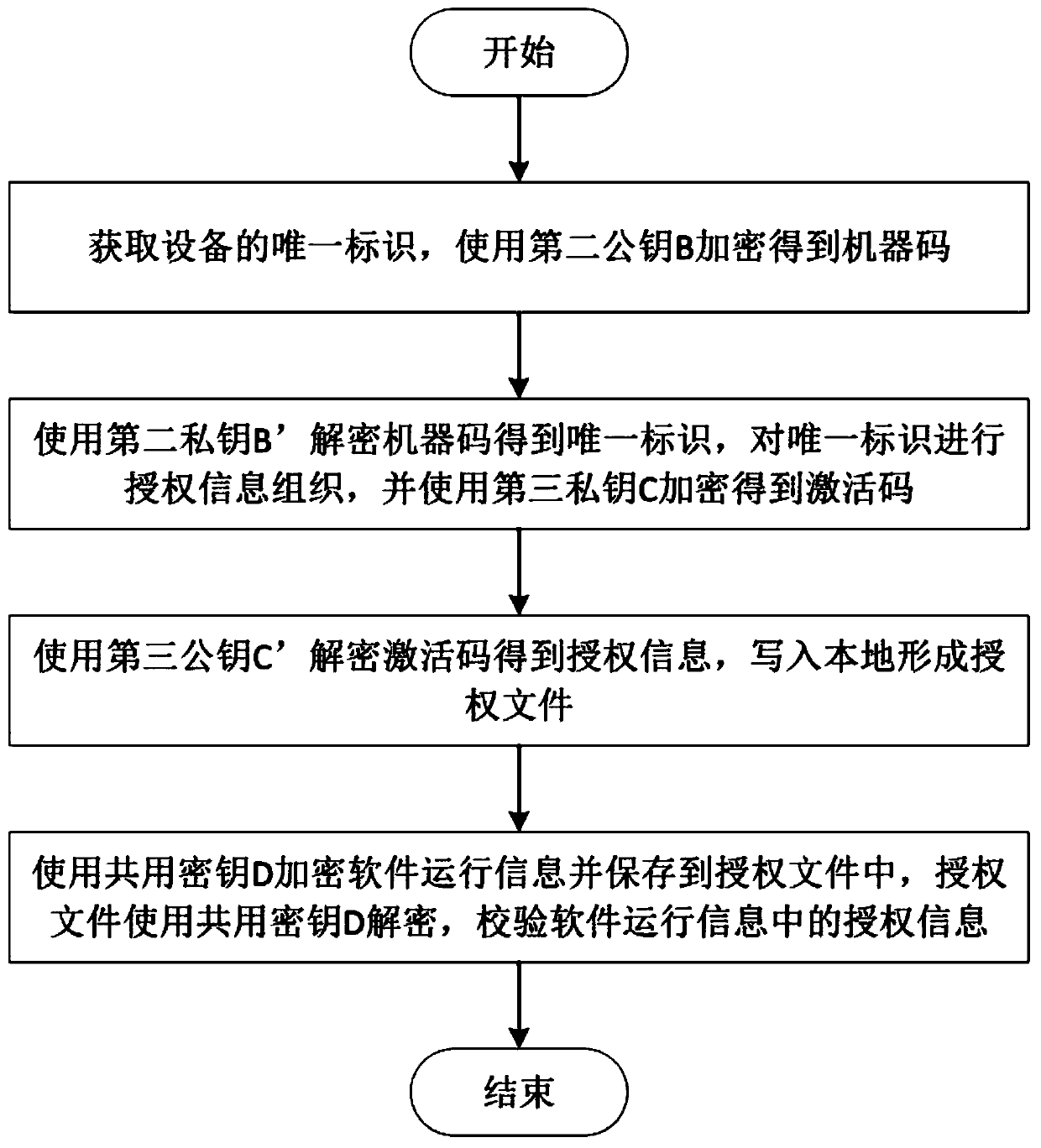
[0030] A method for verifying the validity of the right to use software in this embodiment, such as figure 1 As shown, the specific steps are as follows:
[0031] Step A: Obtain the unique identifier of the device, and encrypt the unique identifier of the device to generate machine code ciphertext;
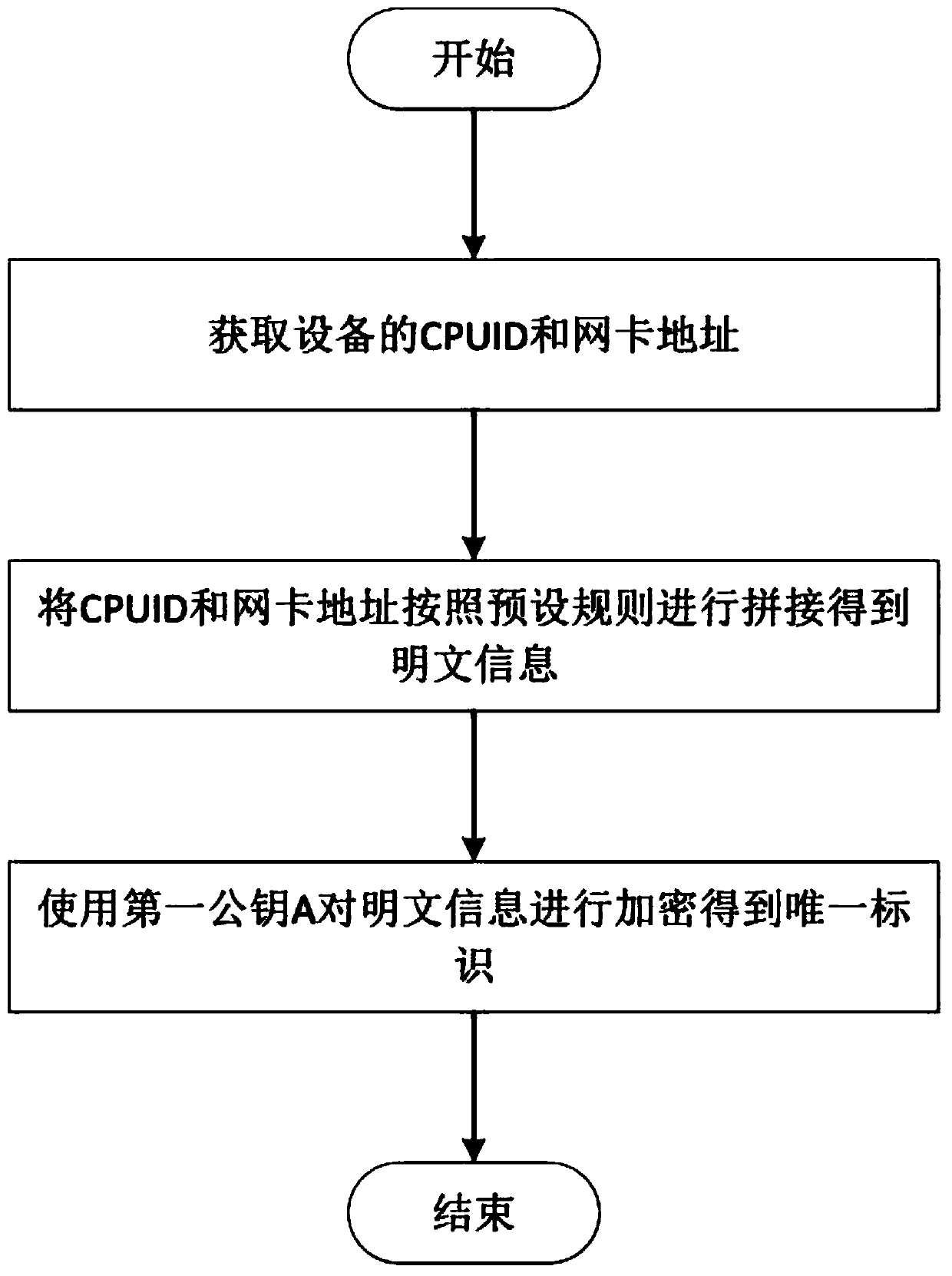
[0032] Such as figure 2 As shown, including the specific steps to generate the unique identifier of the device:
[0033] Step a1: Obtain the CPUID and network card address of the device;
[0034] Step a2: Concatenate the CPUID and network card address obtained in step a1 to obtain plaintext information;
[0035] Step a3: Generate the first public key A and the first private key A', and use the first public key A to encrypt the plaintext information to form ciphertext, which is the unique identifier...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com