Network security decision-making method and device for game attack and defense graph and storage medium
A technology of network security and decision-making method, applied in the field of network security decision-making method of device and storage medium, game attack and defense graph, can solve the problem of large error in security strategy, inability to effectively distinguish the real hazard status of vulnerable points, and inability to reflect the complexity and complexity of vulnerable points. Diversity and other issues to achieve the effect of network management
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
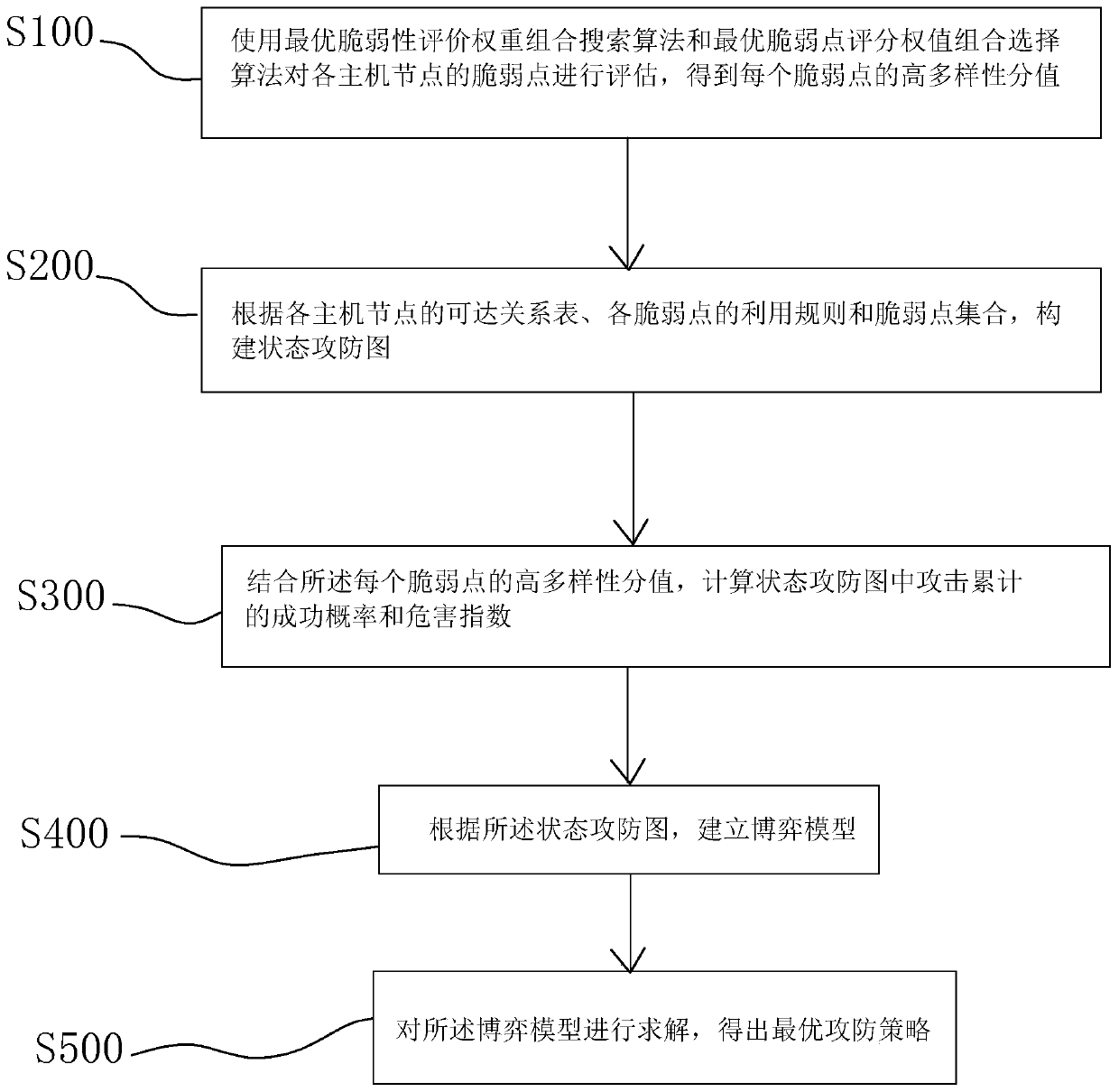
[0032] The present invention provides a network security decision-making method, device and storage medium of a game attack-defense graph, which can perform more reliable high-diversity evaluation on vulnerable points of the network, and establish a game attack-defense graph for vulnerable points with high-diversity characteristics , and finally get the optimal defense strategy of network security.
[0033] The embodiments of the present invention will be further described below in conjunction with the accompanying drawings.
[0034] refer to figure 1 , an embodiment of the present invention provides a network security decision-making method of a game attack-defense graph, comprising the following steps:
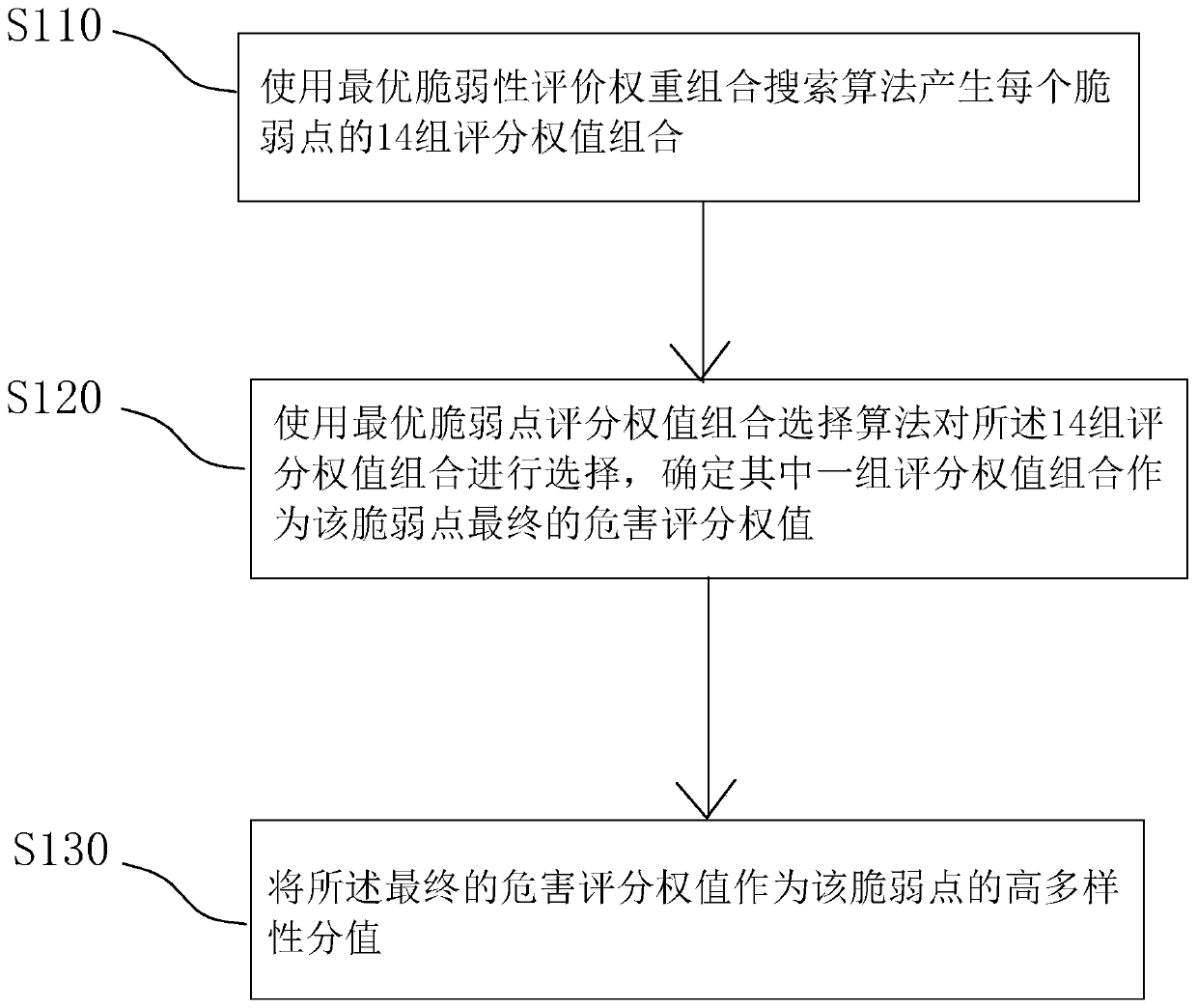
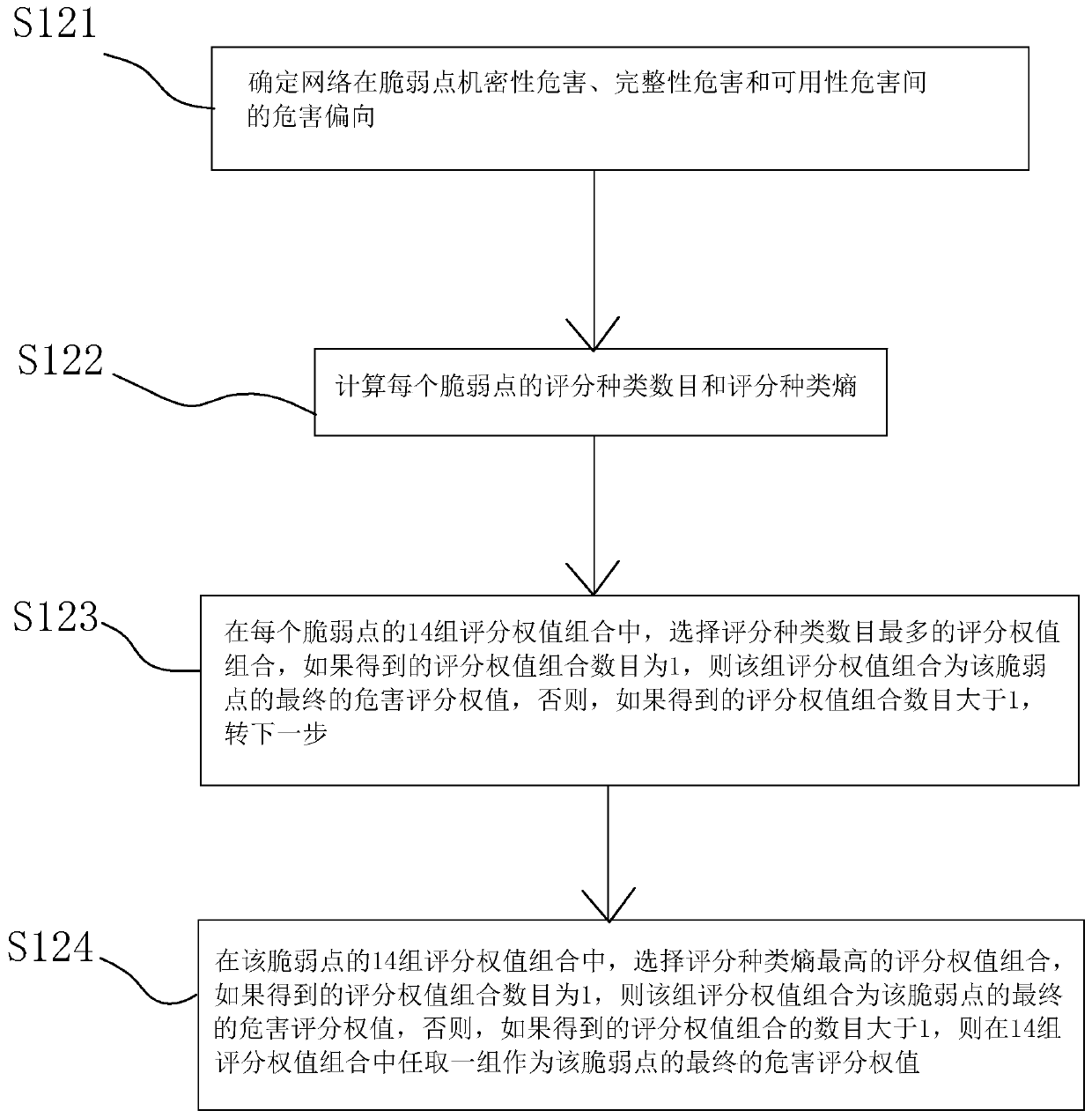
[0035] Step S100: Evaluate the vulnerability points of each host node by using the optimal vulnerability evaluation weight combination search algorithm and the optimal vulnerability point scoring weight combination selection algorithm to obtain a high diversity score for ea...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com