Malicious encrypted traffic detection method based on logistic regression enhancement model
A logistic regression and flow detection technology, applied in digital transmission systems, electrical components, transmission systems, etc., can solve problems such as difficult to improve recall rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
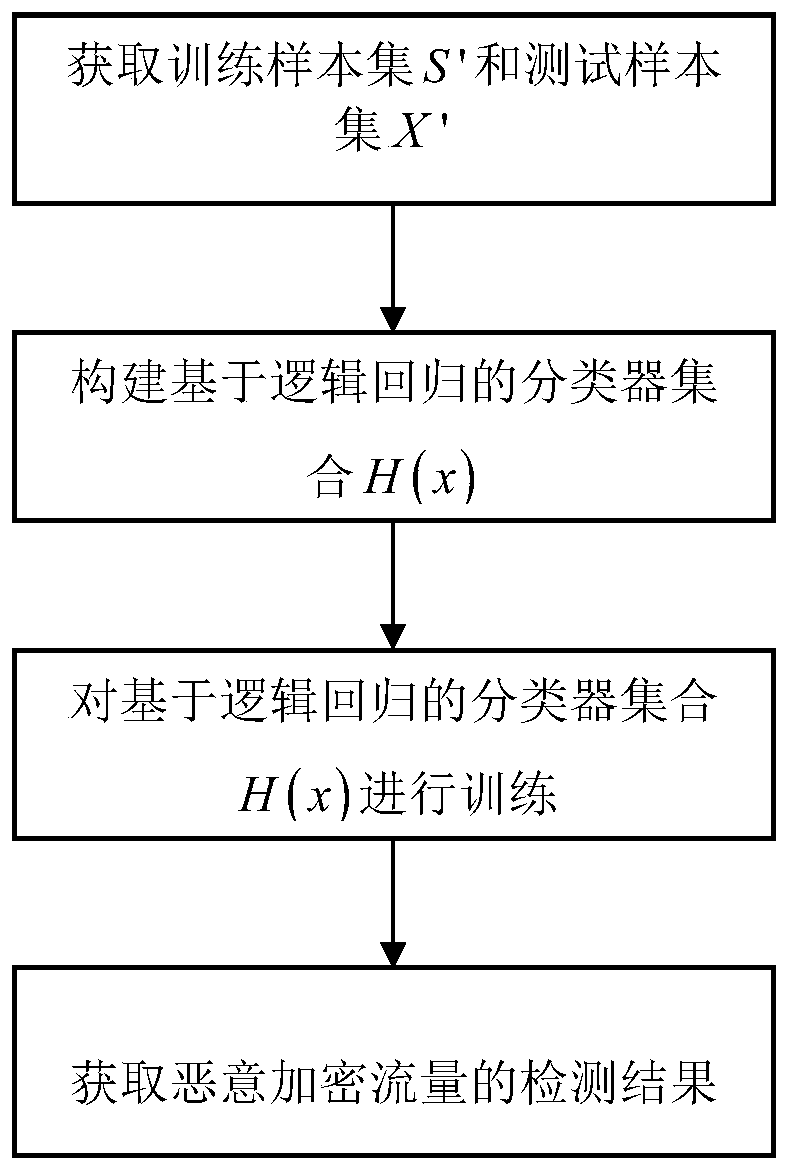
[0046] refer to figure 1 , the present invention comprises the following steps:
[0047] Step 1) Obtain training sample set S' and test sample set X':
[0048] Step 1a) Obtain training sample set S':
[0049] Step 1a1) Build a windows7 sandbox environment in the host, and close the system security settings, use the threading library and os library in python to write a program, automatically run a virus program for 5 minutes, update the sandbox environment and automatically run the next virus program after completion , repeat this process until all virus programs are completed. The virus program is provided by an authoritative virus detection agency. Use the monitoring method sniff() in the scapy library at the network traffic exit in the sandbox environment to monitor the exit network card and collect traffic generated by malicious code activities. As malicious traffic, build a local area network, use the monitoring method sniff() to capture the normal Internet traffic of us...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com