Gathering indicators of compromise for security threat detection
An indicator and security technology, applied in the transmission system, electrical components, etc., can solve the problems of stealing sensitive data, destroying computer operations, etc., and achieve the effects of reducing damage, effective identification, and robust threat detection
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
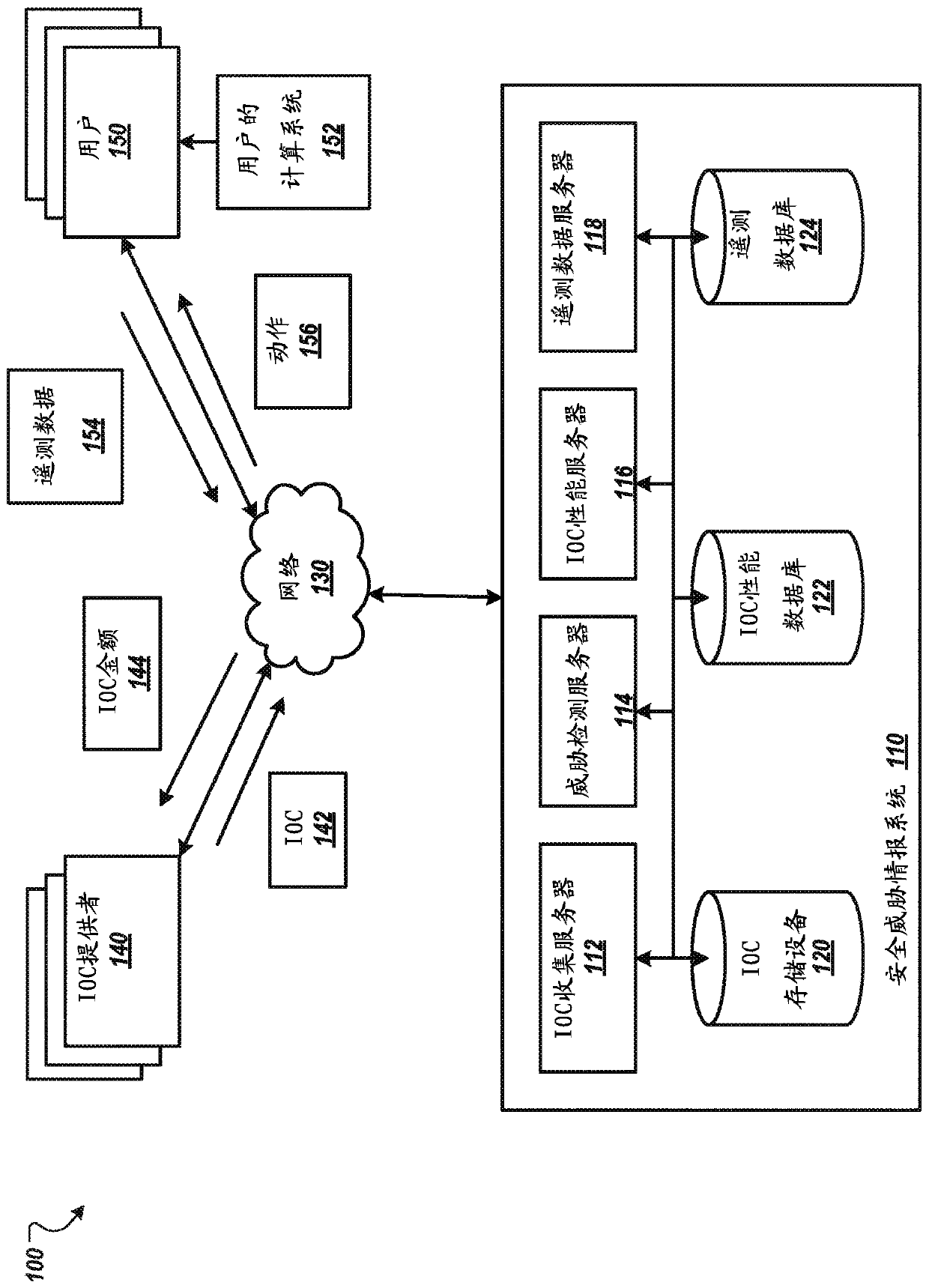
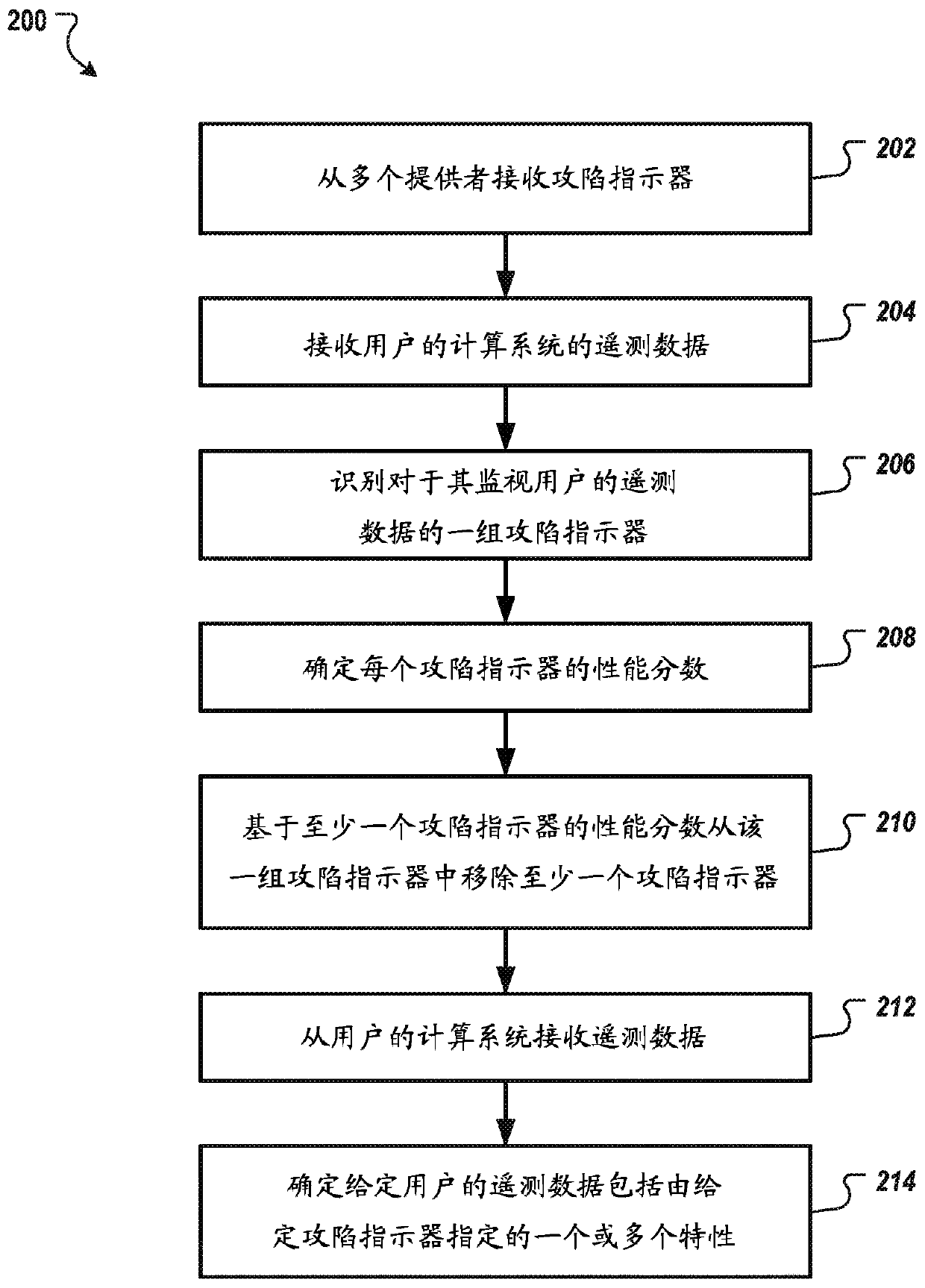
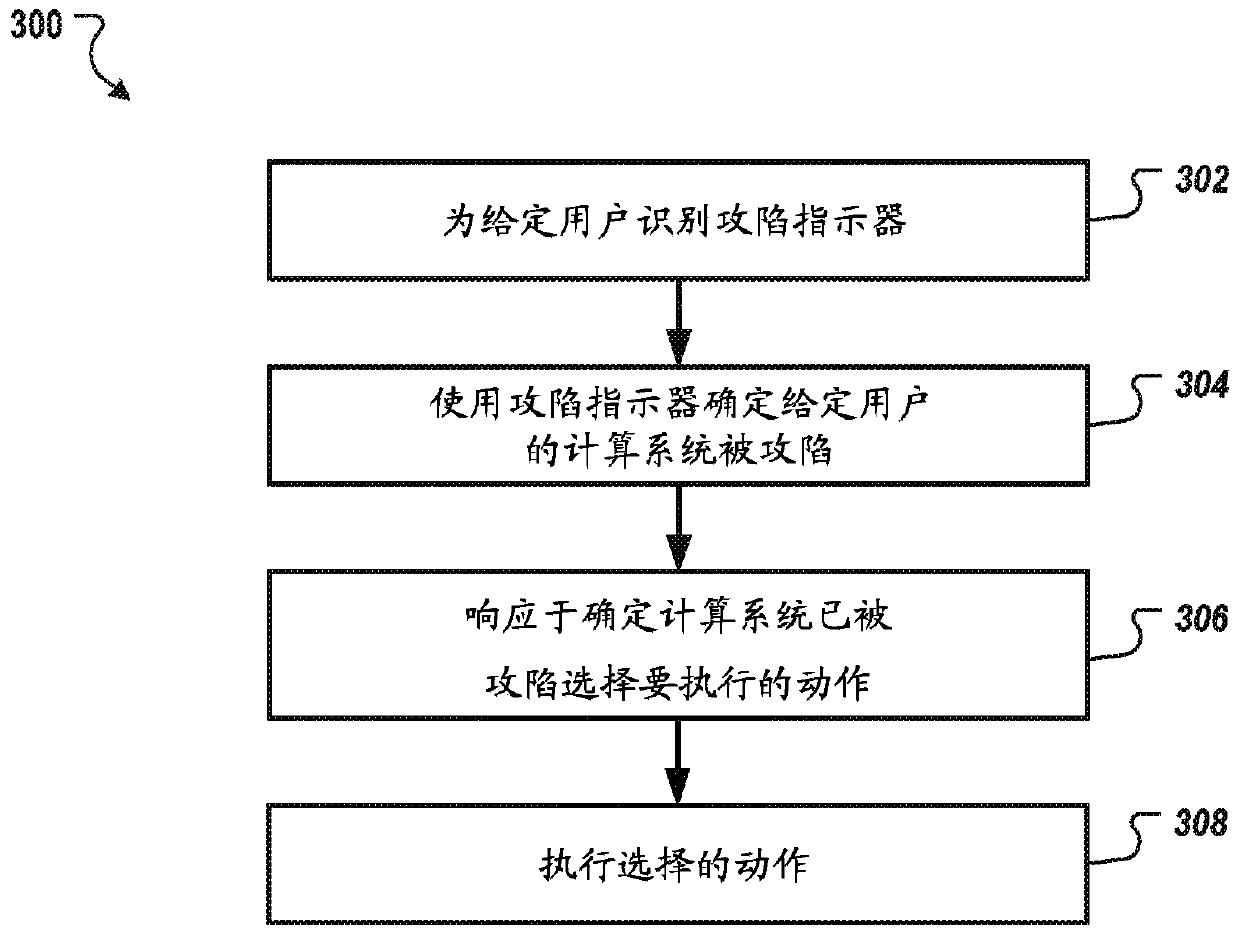
[0020] In general, this disclosure describes systems, methods, devices, and other techniques for collecting indicators of compromise ("IOCs") and using the IOCs to identify computing systems that have been compromised, eg, by malware or hacking. The system can enable users such as researchers, incident responders, information technology professionals, and others to upload and share IOCs that can be used to identify compromised computing systems. An IOC may specify one or more characteristics of a computer security threat. For example, a user may reverse engineer a new botnet and generate an IOC specifying characteristics of the new botnet.
[0021] The system can evaluate the performance of IOCs and filter out low performing IOCs or block providers of low performing IOCs. Thus, the system enables rapid assessment of multiple different IOCs. Furthermore, the most effective IOCs relative to other IOCs emerge based on their performance. This aids the technical field of securit...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap