Image encryption method, device and equipment and readable storage medium
An encryption method and image technology, which are applied to secure communication devices, secure communication through chaotic signals, and key distribution, can solve the problem that the real-time requirements of image encryption cannot be met, the computing performance and storage resources are incomparable, and the secret key occupies a large storage space. And other issues
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
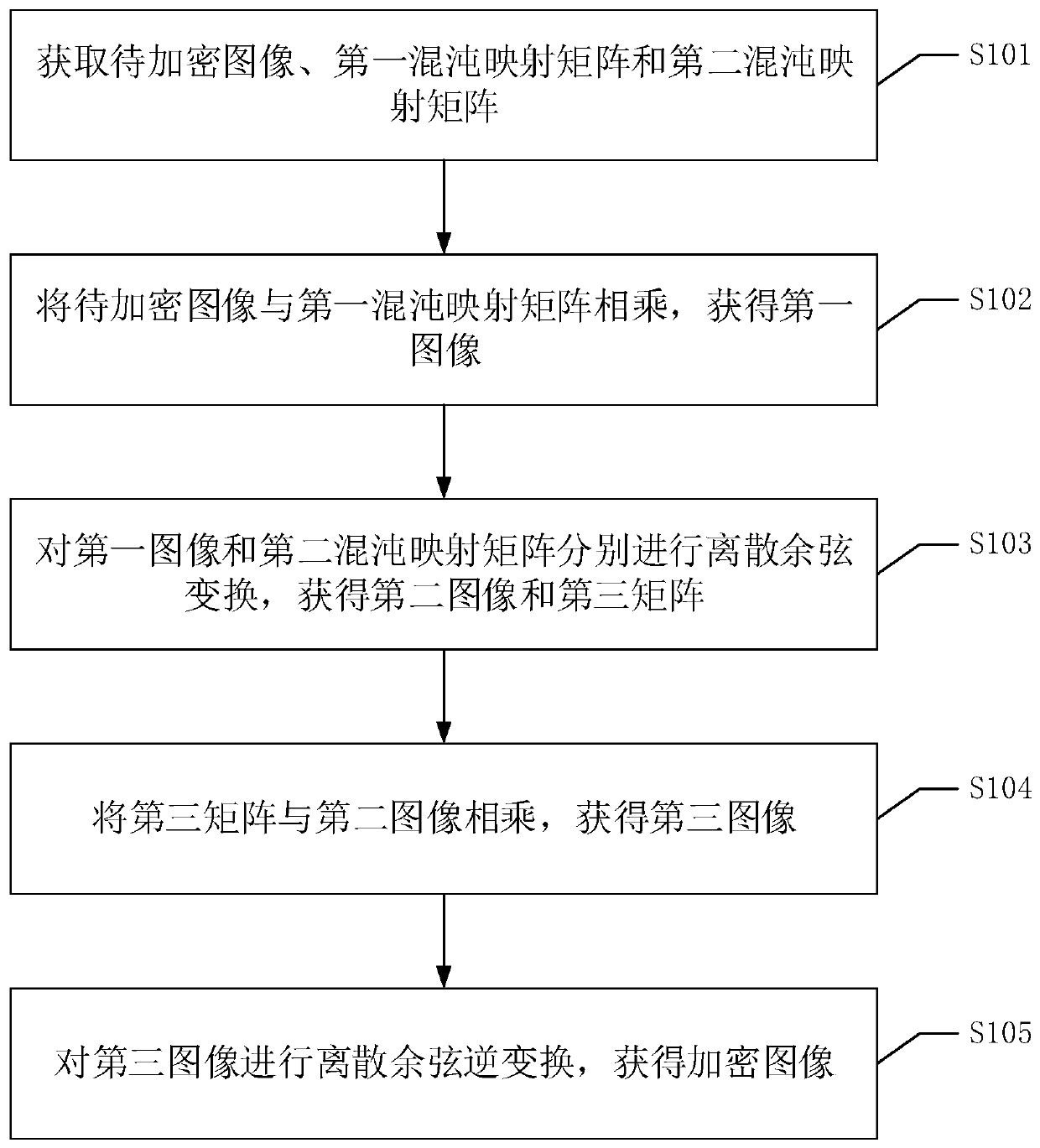
[0062] Please refer to figure 1 , figure 1 It is an implementation flowchart of an image encryption method in an embodiment of the present invention, and the method includes the following steps:
[0063] S101. Acquire an image to be encrypted, a first chaotic mapping matrix, and a second chaotic mapping matrix.
[0064] Wherein, the image to be encrypted may be any image that needs to be encrypted. For example, it could be a photo of the ID to be transferred.
[0065] The image to be encrypted can be directly captured by an image acquisition device such as a camera, or the image to be encrypted can be obtained by communicating and interacting with other devices and receiving images sent by other devices; it can also directly read pre-stored images from readable storage media. The image to be encrypted.
[0066] Wherein, the first chaotic mapping matrix and the second chaotic mapping matrix may be the same or different. The chaotic mapping matrix can be obtained by using t...
Embodiment 2
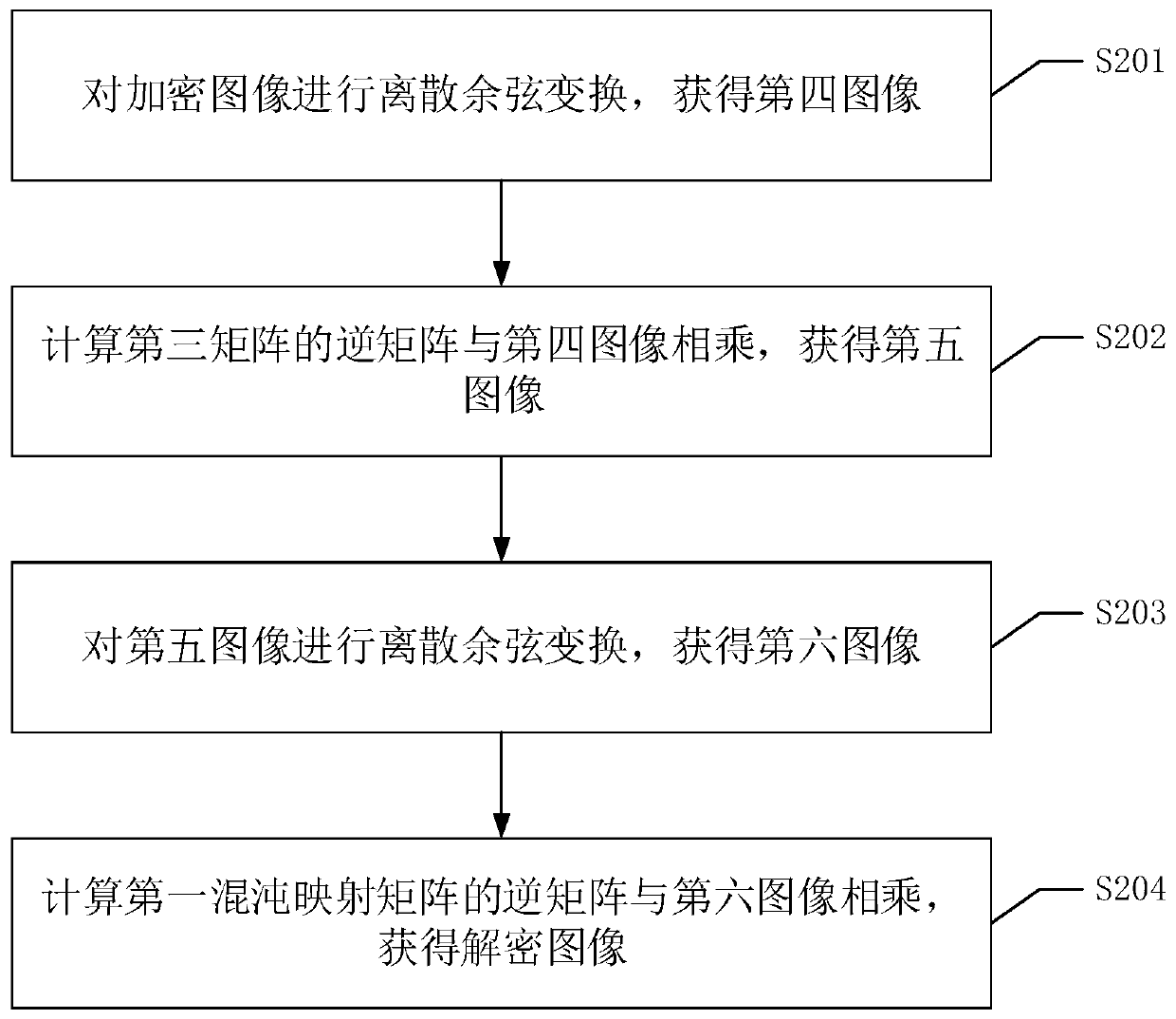
[0086] After the image is encrypted, the encrypted image needs to be decrypted when the image needs to be viewed. If both the decryption process and the encryption process are implemented on the same device, please refer to figure 2 The decryption process shown, figure 2 It is an implementation flowchart of an image decryption method in an embodiment of the present invention, and the method includes the following steps:
[0087] S201. Perform discrete cosine transform on the encrypted image to obtain a fourth image.
[0088] If the image decryption process and the image encryption process are implemented on the same device, the matrix obtained during the encryption process can be directly used for decryption during the decryption process.
[0089] First, a discrete cosine transform is performed on the encrypted image, and at this time a fourth image can be obtained.
[0090] S202. Calculate an inverse matrix of the third matrix and multiply it with the fourth image to obt...
Embodiment 3
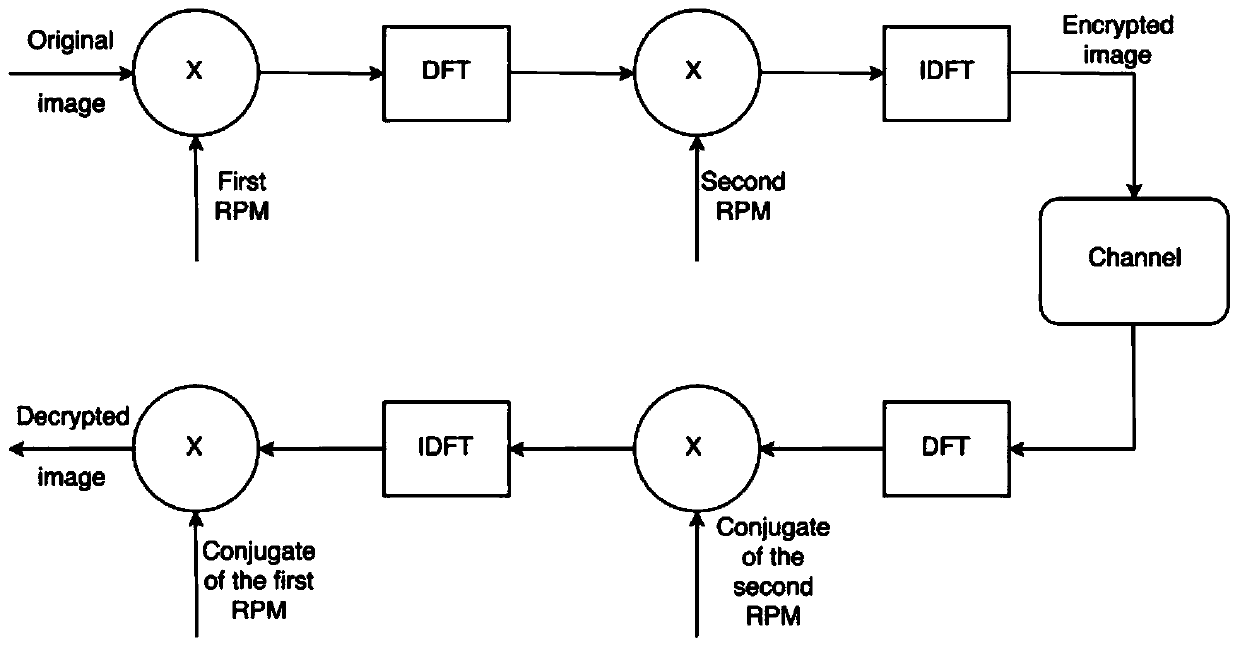
[0096] Considering that the image is encrypted, it is often encrypted when the image needs to be transmitted to ensure the security of the image. In order for the receiver to decrypt the encrypted image, the decryption key and the encrypted image can also be sent to the receiver. That is, on the basis of the above method embodiments, after the image encryption is completed, the following steps can also be performed:
[0097] Step 1, using the first random parameter group and the second random parameter group as keys;
[0098] Step 2, transmit the key and the encrypted image to the receiving end.
[0099]It should be noted that, in this embodiment, in order to reduce data transmission, the first random parameter group and the second random parameter group are directly used as keys. It can be known from the above second embodiment that the first chaotic mapping matrix and the second chaotic mapping matrix may also be used as keys. Of course, the matrix required in the decrypt...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com