Bluetooth communication authentication request, receiving and communication method, mobile terminal, device terminal
A technology of Bluetooth communication and authentication request, which is applied to the device side, receiving and communication methods, Bluetooth communication authentication request, and mobile terminal fields. Effects of safety, speed improvement, and computing efficiency improvement
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
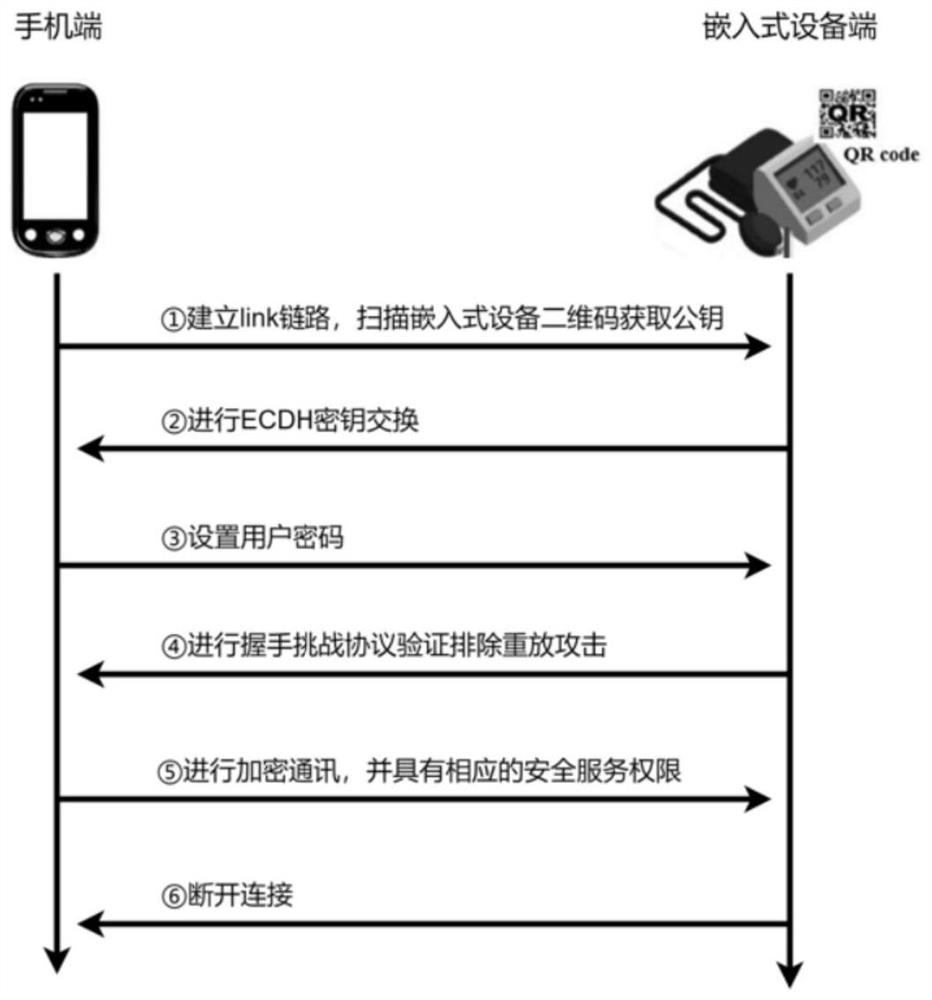
[0095] Such as Figure 4 As shown, this embodiment discloses a bluetooth communication method, including the authentication request of the mobile terminal (smart phone is selected in this embodiment), the authentication reception of the device terminal and the data communication between the two.
[0096] The concrete steps of this embodiment are as follows:
[0097] Step 1. Establish a link, and the mobile phone scans the QR code on the device to obtain the public key. The two-dimensional code here contains the second public key information on the device side, which can be directly obtained by scanning the two-dimensional code on the Bluetooth device side through the mobile phone camera (ie, image collector).
[0098] Step 2. Perform ECDH key exchange:
[0099] Step 2.1, the exchange here includes two parts:
[0100] 1. The key on the mobile phone (including public key and private key), and the private key is embedded into the app on the mobile phone by writing code, and st...
Embodiment 2
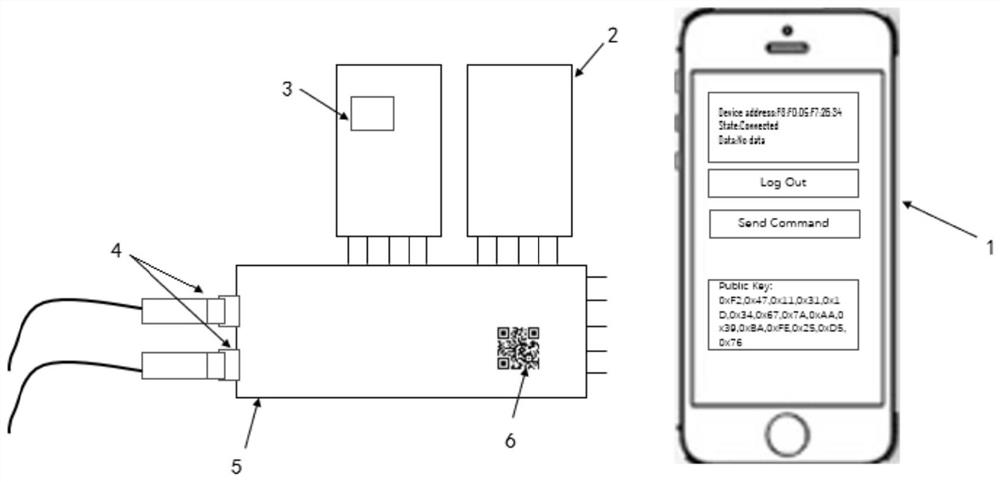
[0137] Such as figure 2 As shown, this embodiment is an example of an overall communication system composed of a mobile terminal and a device terminal. The mobile terminal is a smart phone in this embodiment, including a first application layer and a first link layer:
[0138] The first application layer specifically includes an interaction unit and a logic calculation unit;
[0139] The interactive unit includes an image collector, which in this embodiment is a self-contained camera of the mobile phone; and also includes a user operation graphic interface, which is an APP operation interface of a mobile phone in this embodiment, and the image collector is used to obtain a device-side public key; The user operates the graphical interface to obtain the user password;
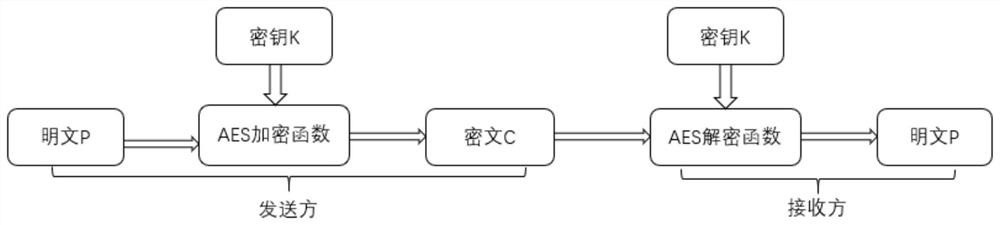
[0140] The logic calculation unit is used to generate an ECDH Based AES Key symmetric key K;
[0141] The logic computing unit is also used to divide the master key into user-based AES key and HMAC key; execut...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com