Buried point event detection method and device, terminal equipment and medium
A detection method and point detection technology, which is applied in the computer field, can solve problems such as false positives, missed detection of buried point events, and the impact of function codes, and achieve the effects of improving detection efficiency, improving accuracy, and reducing intrusion
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
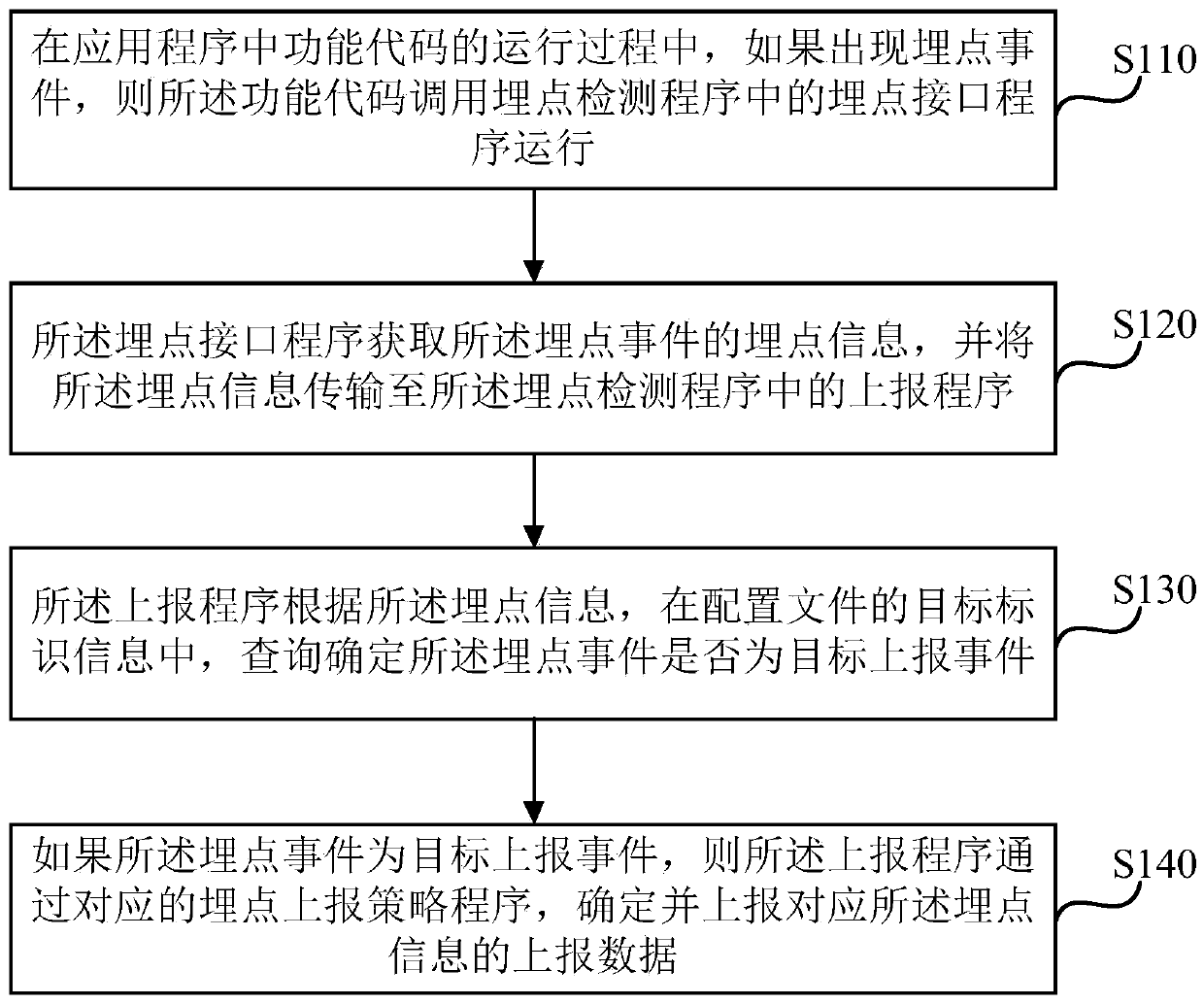
[0027] figure 1 It is a schematic flowchart of a method for detecting a buried point event provided by Embodiment 1 of the present disclosure. This method is applicable to the detection of a buried point event. Specifically, the method is applicable to the detection of buried points generated in an application program The event is detected. The method can be performed by a device for detecting buried point events, wherein the device can be implemented by software and / or hardware, and is generally integrated on a terminal device. In this embodiment, the terminal device includes but is not limited to: a mobile phone, a computer or a personal digital Assistant and other equipment.
[0028] Existing solutions for setting burying points in applications include manual burying, automatic burying and visual burying.
[0029] Manual point burying requires developers to write corresponding codes for the terminal platform, and when the user interacts with the application, the user's pa...
Embodiment 2
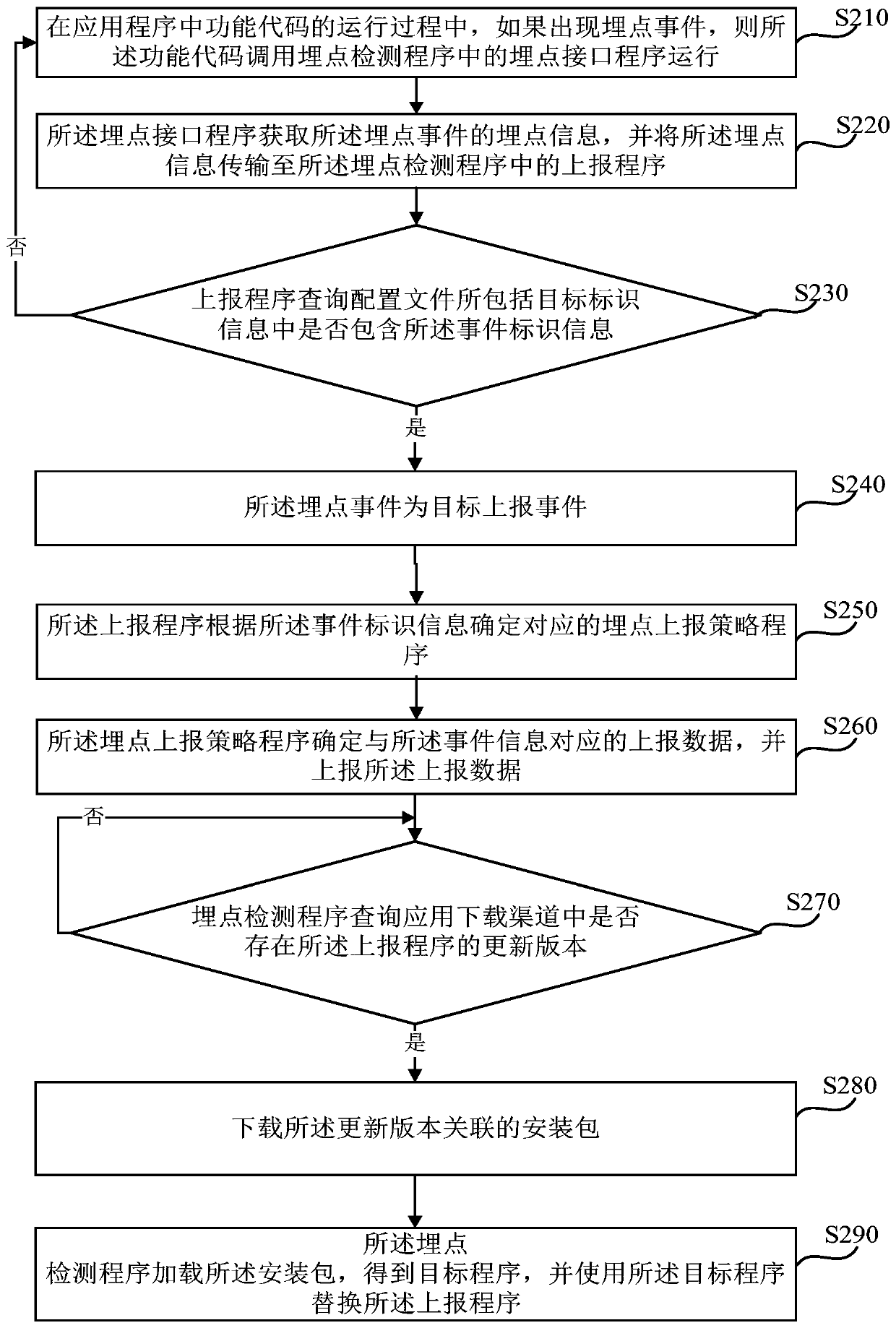
[0064] figure 2 It is a schematic flow chart of a method for detecting buried point events provided by Embodiment 2 of the present disclosure. Embodiment 2 is optimized on the basis of the foregoing embodiments. In this embodiment, the buried point information includes event identification information and event information, and the event information includes event name and event parameters.
[0065] Further, in this embodiment, the reporting program will query and determine whether the buried point event is a target reporting event in the target identification information of the configuration file according to the buried point information, and the optimization includes: the reporting program queries the configuration file Including whether the target identification information contains the event identification information;
[0066] If included, the buried point event is a target reporting event.
[0067] On the basis of the above-mentioned optimization, the reporting progra...
Embodiment 3
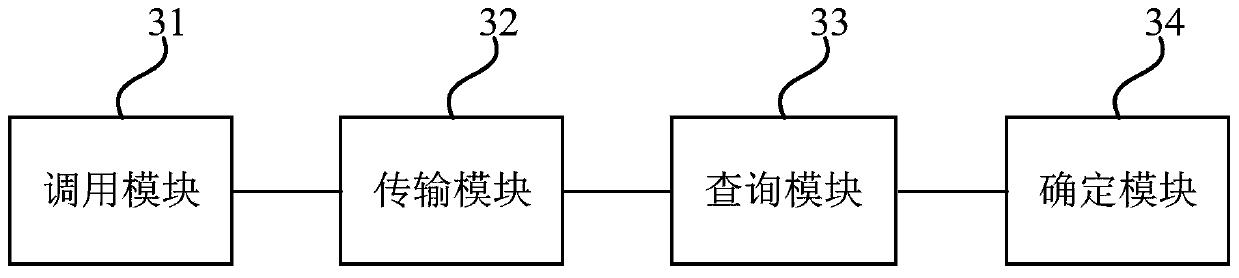
[0120] image 3 It is a schematic structural diagram of a detection device for a buried point event provided by Embodiment 3 of the present disclosure. The device is applicable to the detection of a buried point event. Specifically, the method is applicable to the detection of a buried point event generated in an application program. The event is detected. Wherein the device can be realized by software and / or hardware, and generally integrated on the terminal equipment.
[0121] Such as image 3 As shown, the device includes: a call module 31, a transmission module 32, a query module 33 and a determination module 34;
[0122] Wherein, the calling module 31 is used for running the function code in the application program, if a buried point event occurs, the function code calls the buried point interface program in the buried point detection program to run;
[0123] The transmission module 32 is used for the buried point interface program to obtain the buried point informatio...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com