A block chain transaction method based on multi-user CA digital certificate
A technology of digital certificates and transaction methods, applied in user identity/authority verification, digital transmission systems, data processing applications, etc., to achieve the effects of improving efficiency, shortening initiation time, and reducing burdens
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0054] The technical solution of the present invention will be described in further non-limiting detail below in combination with preferred embodiments and accompanying drawings.
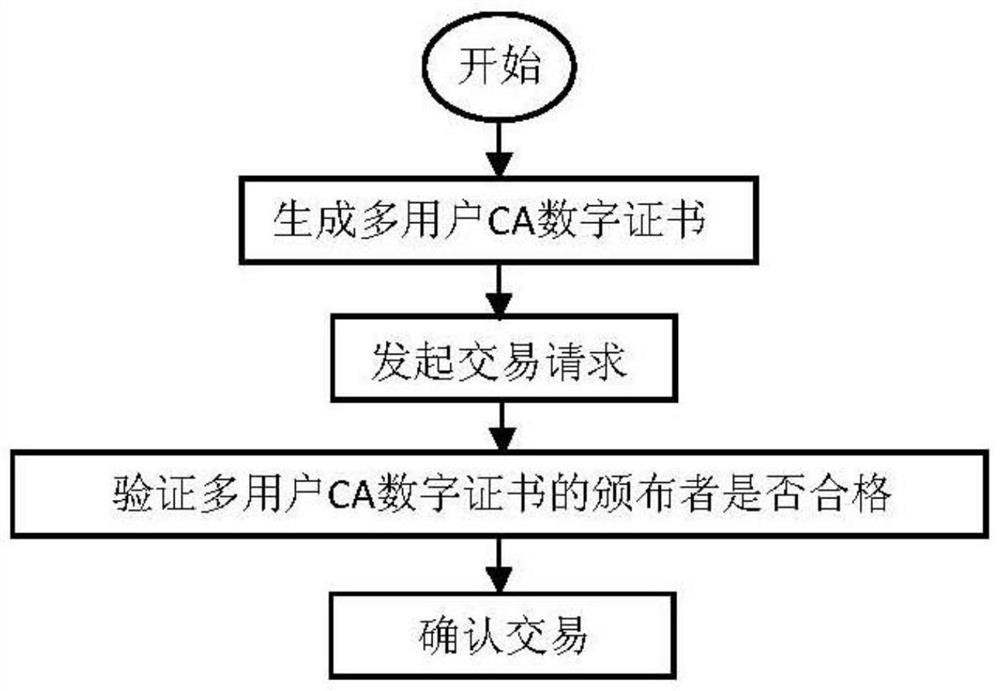
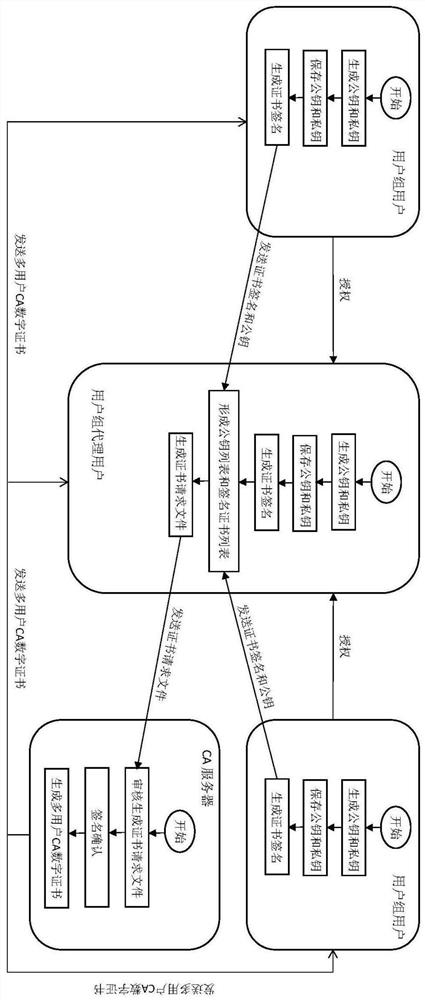
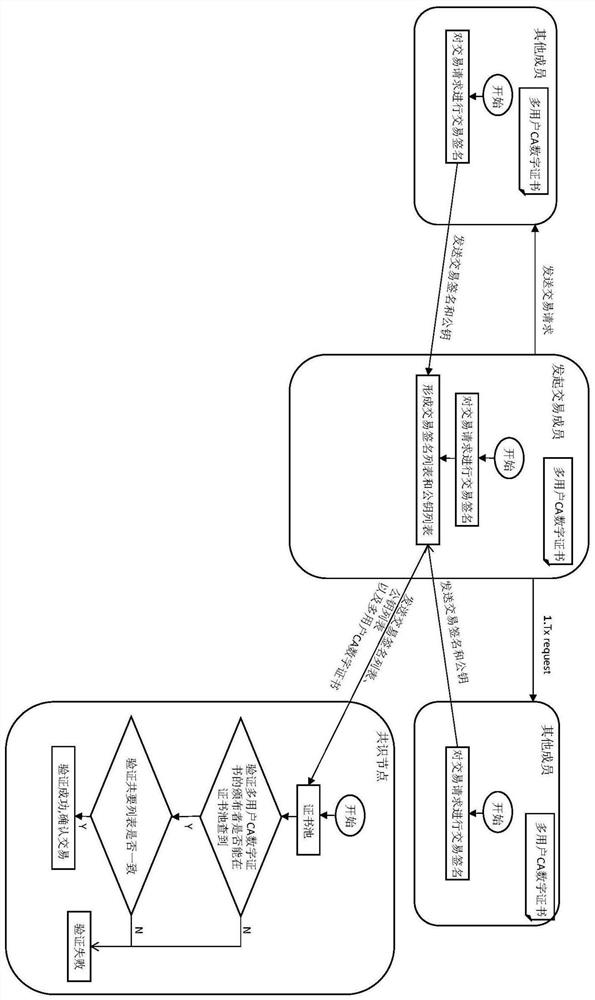
[0055] Such as figure 1 with figure 2 Shown, corresponding to a kind of blockchain transaction method based on multi-user CA digital certificate of the present invention, it comprises the following steps:
[0056] Step 1: Members of the user group participating in the transaction use their respective public keys and signatures to apply for a CA digital certificate to the CA server. After the review is passed, the CA server generates a multi-user CA digital certificate, including:
[0057] Step 1-A: Members of the user group participating in the transaction use the SM2 elliptic curve public key cryptography algorithm to generate public keys and private keys at their respective user nodes, and store them in their respective user nodes;
[0058] Step 1-B: Members of the user group entrust the author...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com