User risk assessment method and system based on network security device log data
A network security and risk degree technology, which is applied in the field of user risk assessment based on network security device log data, can solve problems such as user unauthorized access, user account abuse, and abnormal access behaviors that cannot be detected well
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0049] The implementation of the present invention will be described in detail below in conjunction with the drawings and examples.
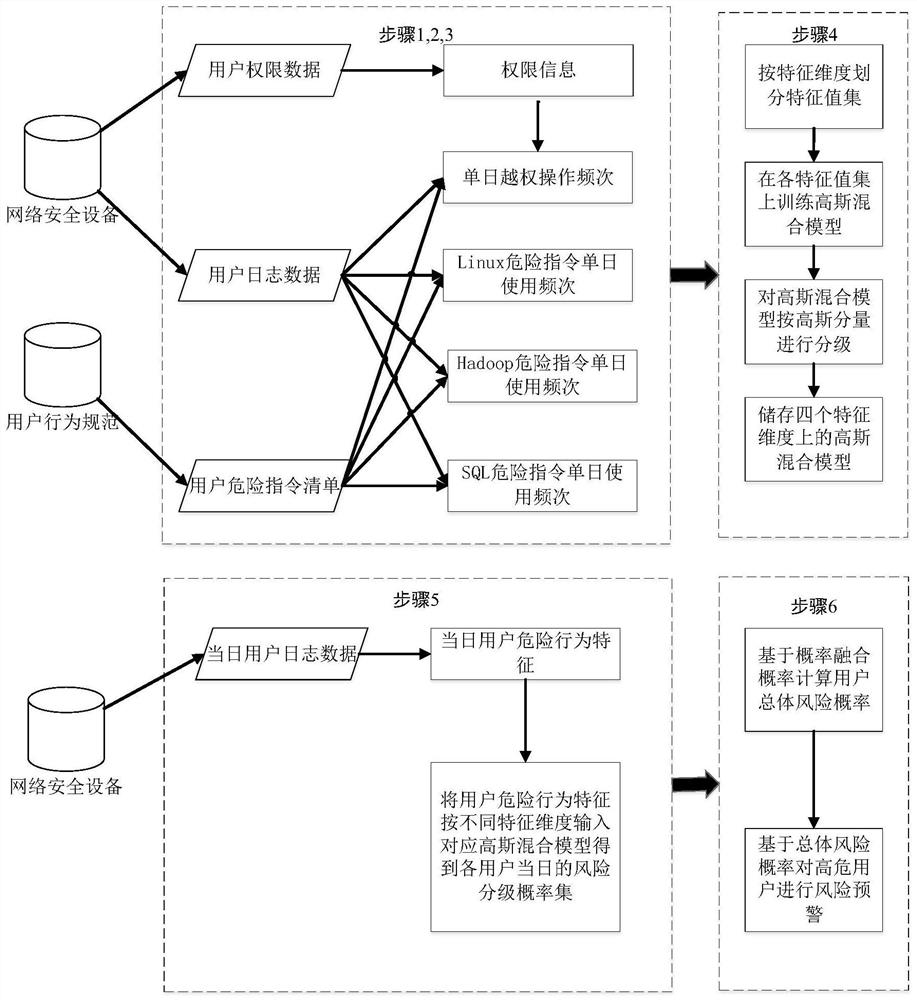
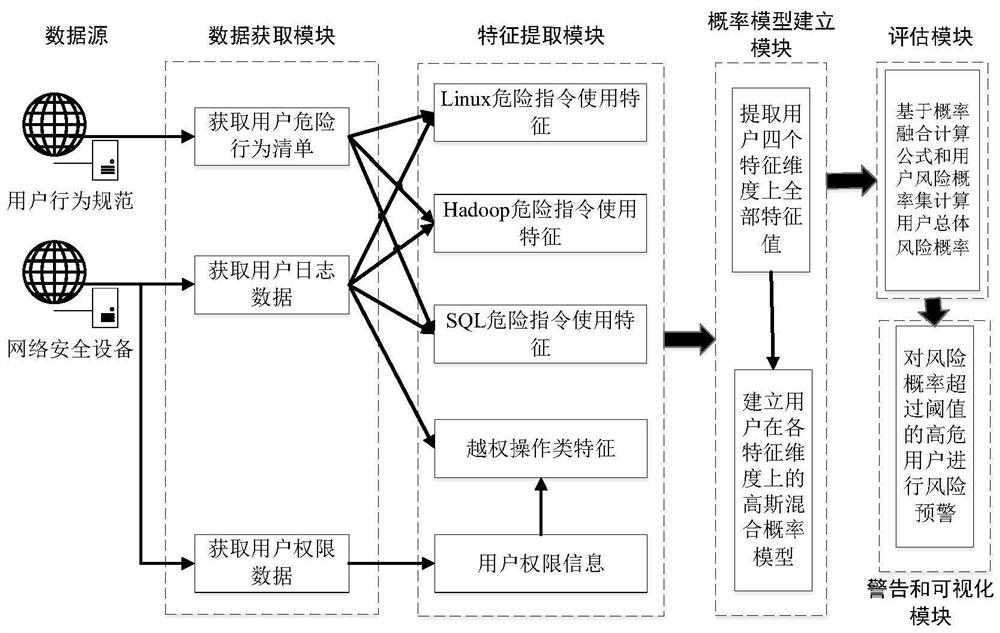
[0050] The method in the present invention will be divided into two parts: offline modeling and online analysis, specifically including data acquisition process, feature extraction process, probability model establishment process, and online user risk assessment process. figure 1 It is a block diagram of the user risk assessment method based on network security device log data of the present invention. The system of the present invention is illustrated in block diagram form. figure 2 It is a frame diagram of a user risk assessment system based on network security device log data of the present invention.
[0051] data acquisition process
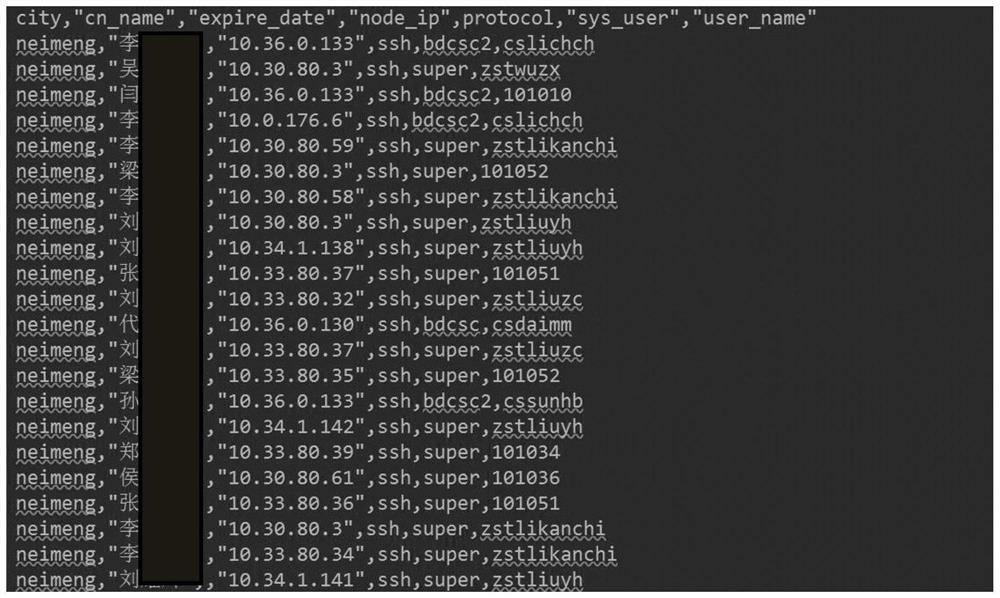
[0052] image 3 It is an instance of the user authority data of the network security device. Figure 4 is an instance of network security device user log data. Figure 5 It is an instance of the user's d...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com