Video encryption method for resisting contour attacks
An encryption method and video technology, which are applied in the fields of digital video signal modification, image communication, selective content distribution, etc., can solve the problems that the visual effect of the encryption method is not ideal and cannot resist MBS contour attack and traditional contour attack.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0074] The present invention will be further described below in conjunction with drawings and embodiments.
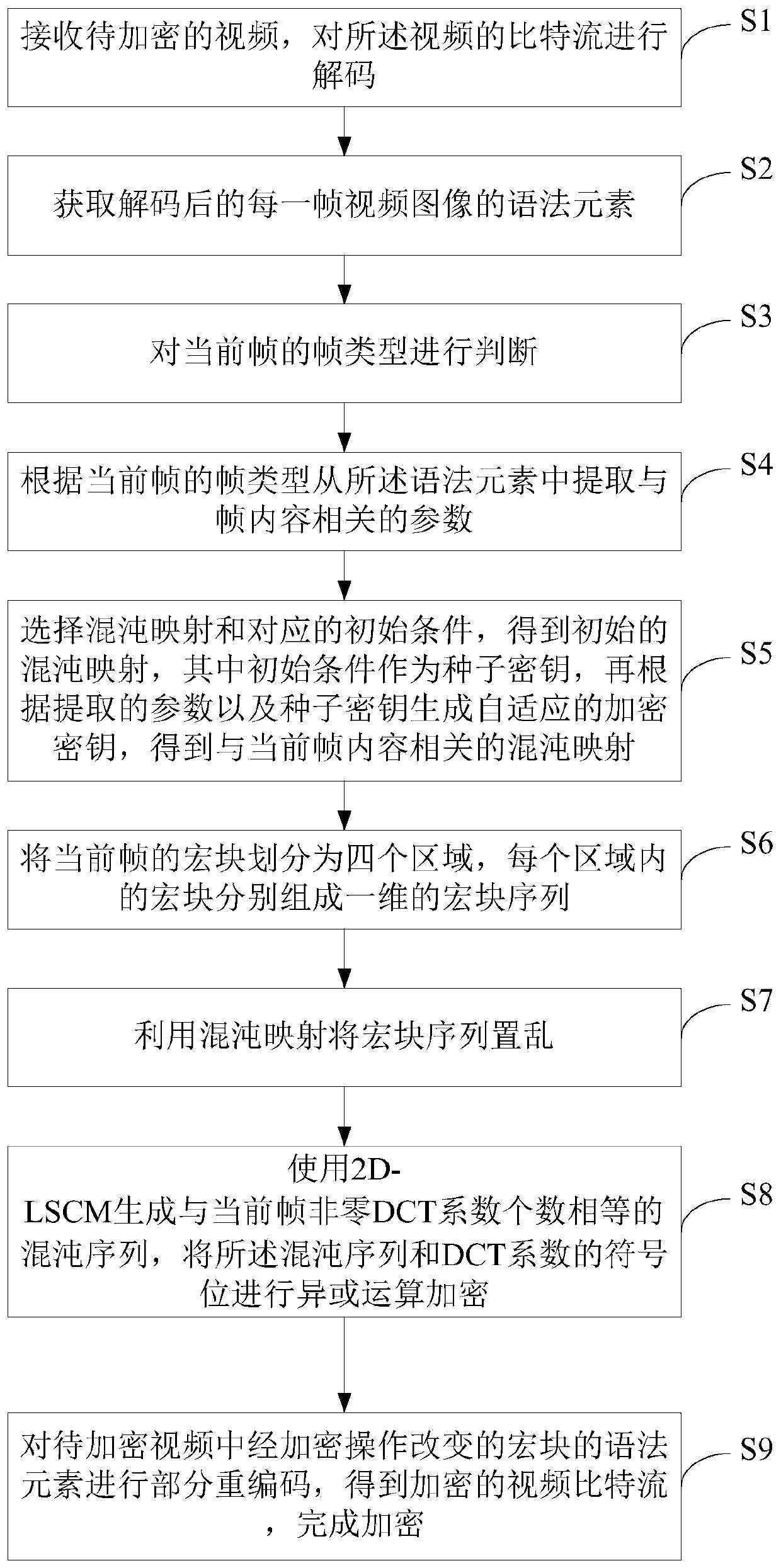
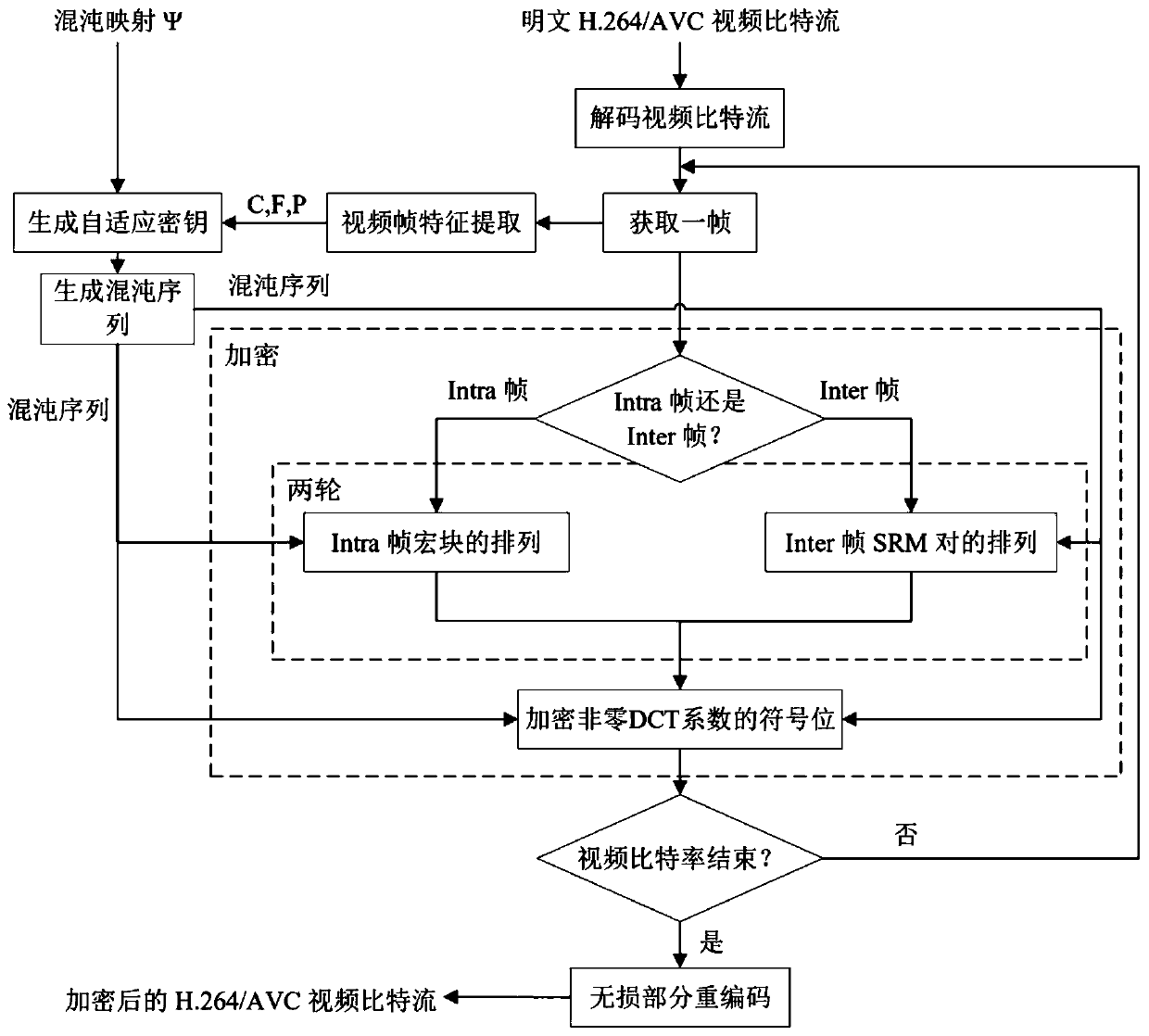
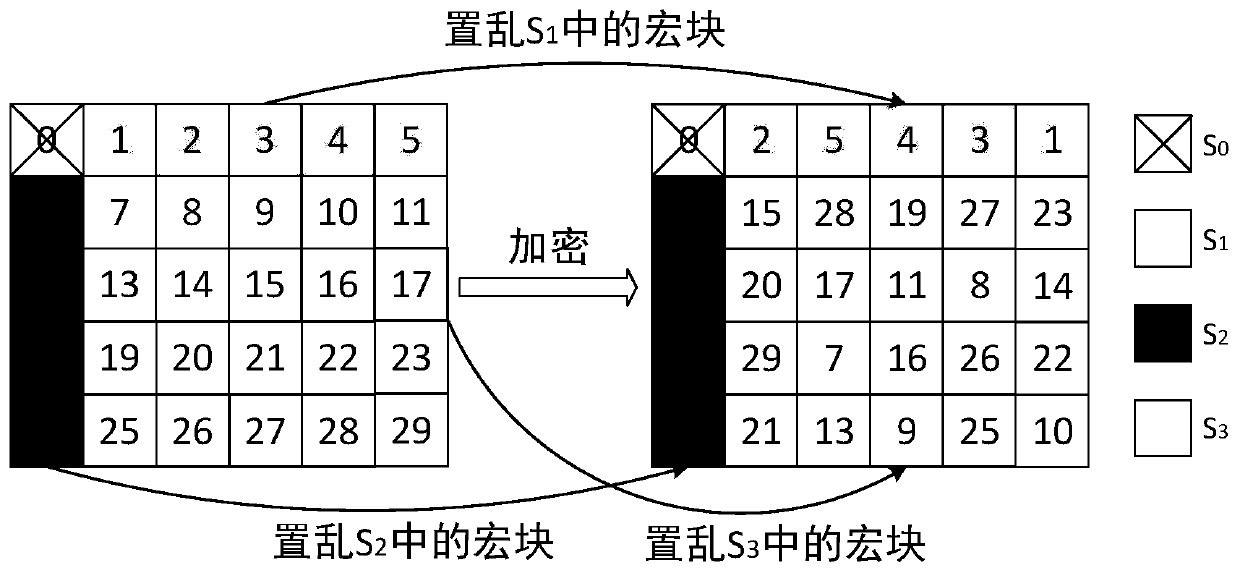
[0075] see Figure 1-4 , a kind of video encryption method for resisting profile attack, comprising:
[0076] S1, receive the video to be encrypted, and decode the bit stream of the video; the video to be encrypted is H.264 / AVC video, and for H.264 / AVC video files, it consists of a series of network abstractions Each network abstraction layer unit (NALU) includes a NAL header and a raw byte sequence load (RBSP), where the NALU of the video coding layer (VCL) type contains encoded video data, which can be Read out the required video corresponding information from it.
[0077] S2, obtaining the syntax element of each frame of video image after decoding; each frame of video image can be divided into I frame, P frame and B frame, and each frame can be divided into several macroblocks of 16×16 pixel size, A macroblock can be further divided into sub-macroblocks. Each cod...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com