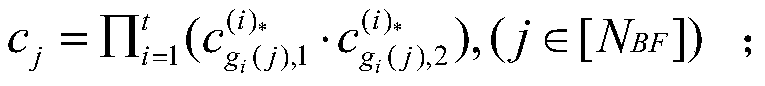Multi-party privacy set intersection method for resisting malicious enemies
A multi-party privacy and malicious technology, applied in the intersection of privacy sets, can solve problems such as low efficiency and poor effect, and achieve the effects of saving time, improving operating efficiency, and reducing computing and communication overheads
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0024] The present invention will be further described in detail below in conjunction with the accompanying drawings and embodiments.
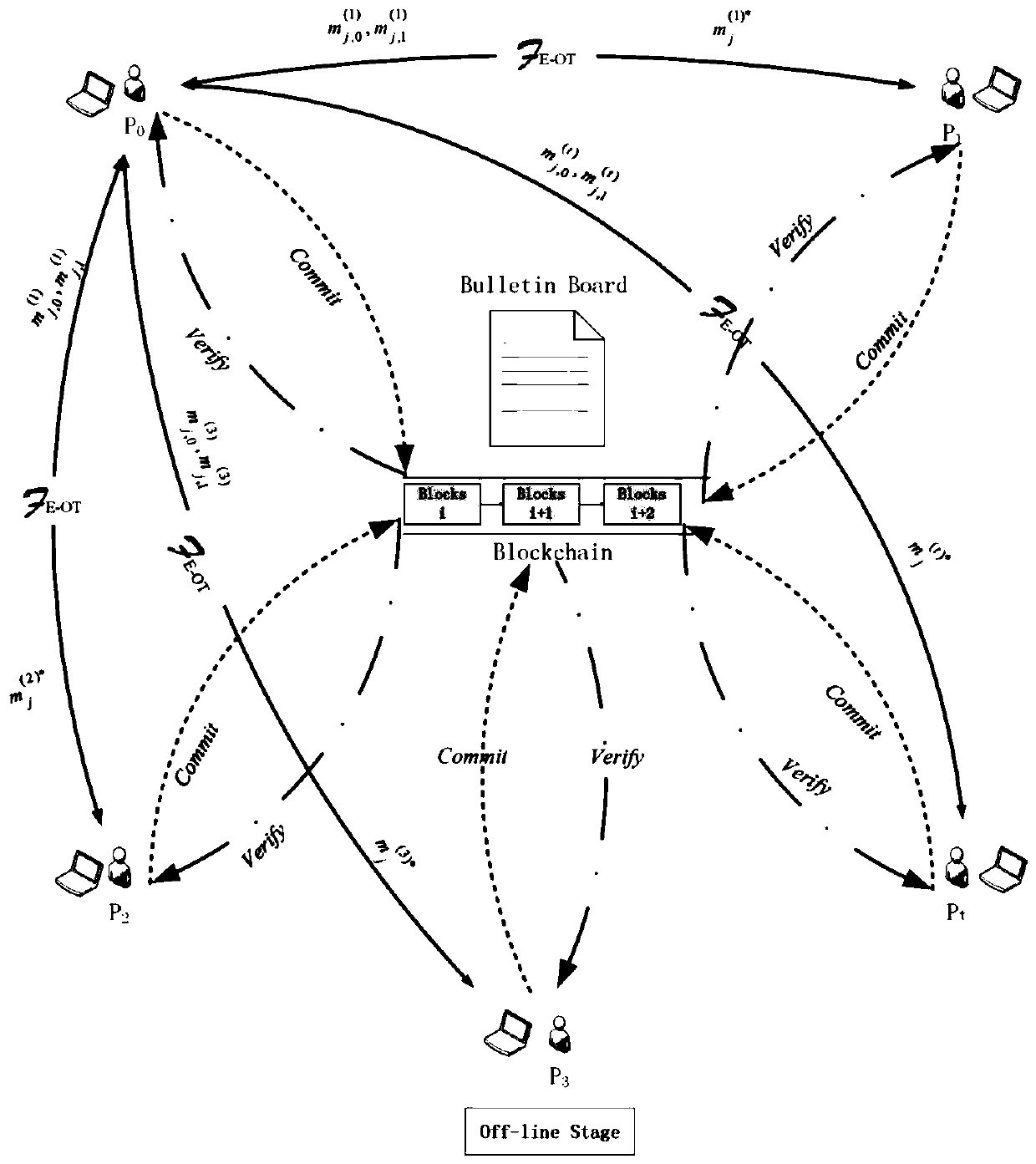
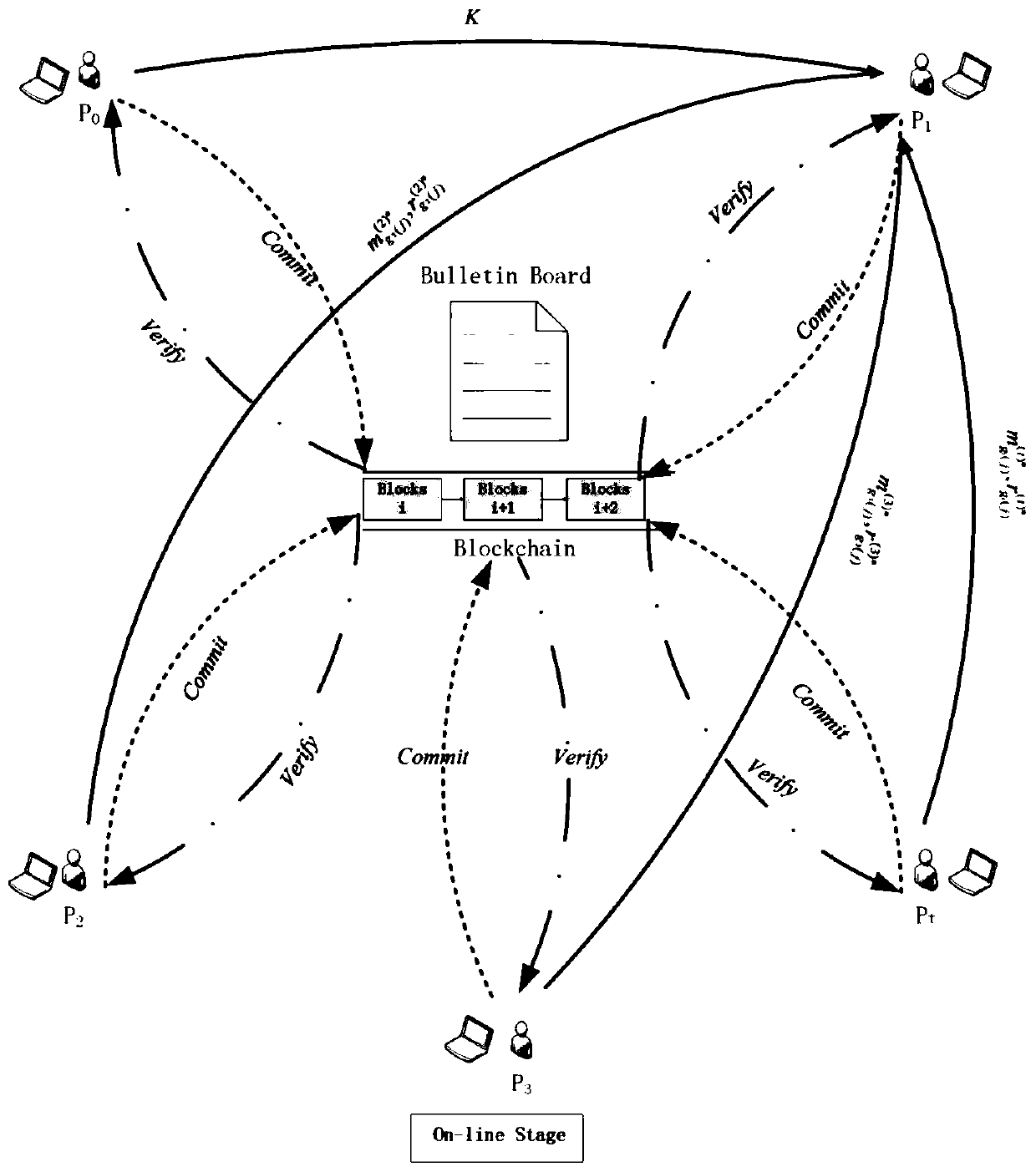
[0025] Such as figure 1 , 2 As shown, the network includes P 0 ,P 1 ,P 2 ,P 3 ,P t Multiple participants, that is, the participants in the network are P 0 with P i , i=1, 2...t, namely P i (i∈[t]).
[0026] In this embodiment, the privacy set intersection method is mainly divided into an offline stage and an online stage, which will be described in detail below.
[0027] Offline phase:
[0028] 1. Initialization phase
[0029] Parameter setting: participant P i has its own set of inputs Φ i is the participant P i The number of elements in the collection. N BF and N OT respectively represent the length of the Bloom filter and the input length of the receiver in the oblivious transfer protocol OT; k is the number of hash functions in the Bloom filter; H represents the random oracle whose output length is k; 0 The proportion o...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com