A fingerprint database establishment method based on the characteristics of web attack tools
A technology for establishing methods and tools, applied in the field of network security, can solve problems such as the inability to block network attacks quickly, timely and effectively, block and dispose of, and complete intelligence collection work early or in advance, so as to improve monitoring. The effect of early warning and evidence collection capabilities and reducing hidden risks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
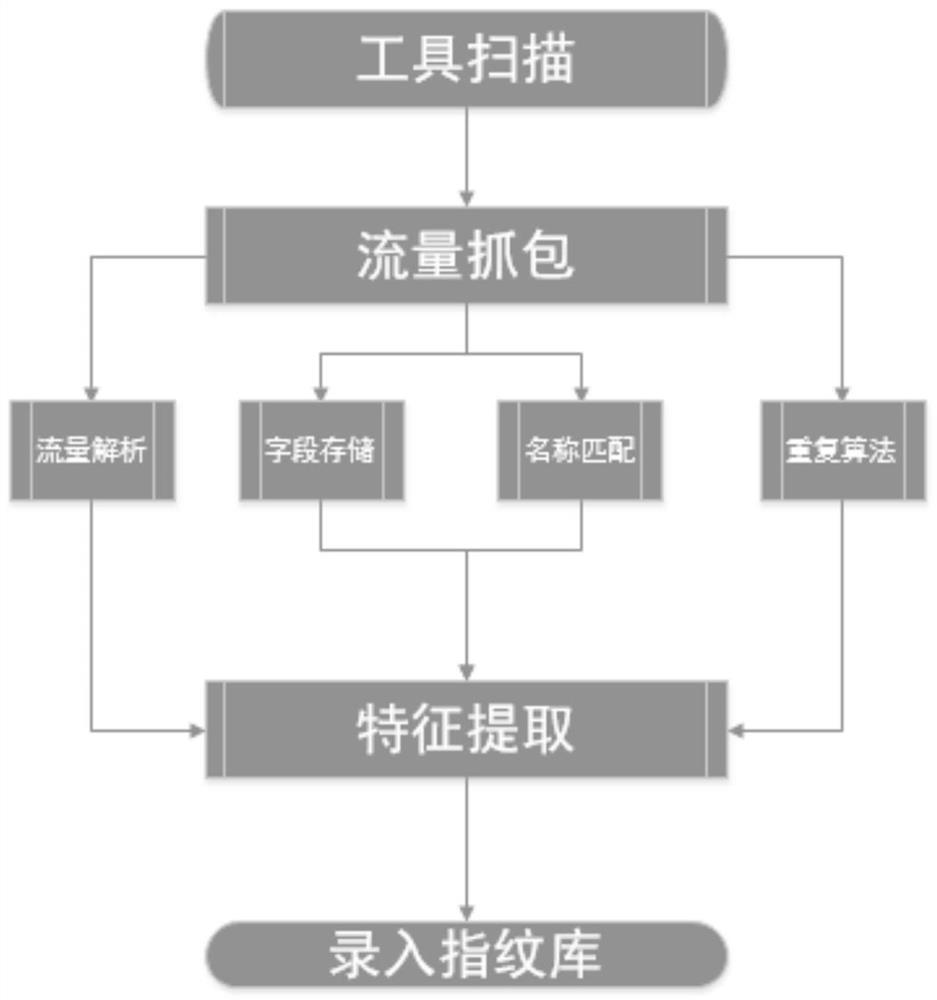
[0029] The following combination figure 1 and figure 2 Embodiment 1 will be described.
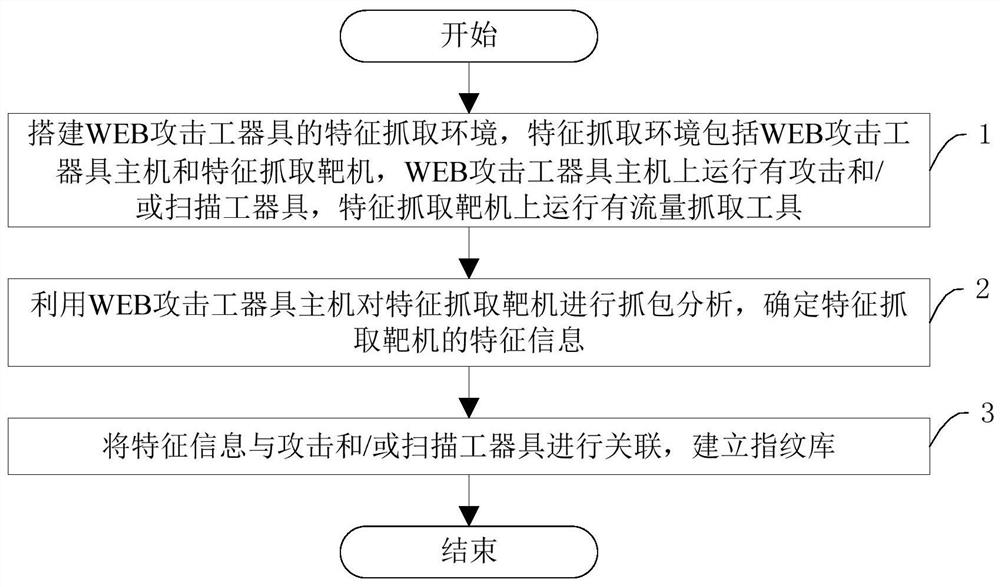
[0030] Such as figure 1 As shown, the present embodiment provides a method for establishing a fingerprint library based on the characteristics of WEB attack tools, including:
[0031] Step 1. Set up the feature capture environment of WEB attack tools. The feature capture environment includes the WEB attack tool host and the feature capture target machine. Attack and / or scanning tools are running on the WEB attack tool host. Feature capture There is a traffic grabbing tool running on the target machine.
[0032] Specifically, the WEB attack tool host is mainly installed with mainstream WEB attack and scanning tools, such as: system-type BT5, kali, Parrot, BackBox and other web-scanning attack systems; scanning-type Nikto, WebInspect, Burpsuite, Acunetix Web Vulnerability Scanner (AWVS ), AppScan, NMAP, SQLMAP and other scanning attack applications;
[0033] Feature Capture The target ...
Embodiment 2
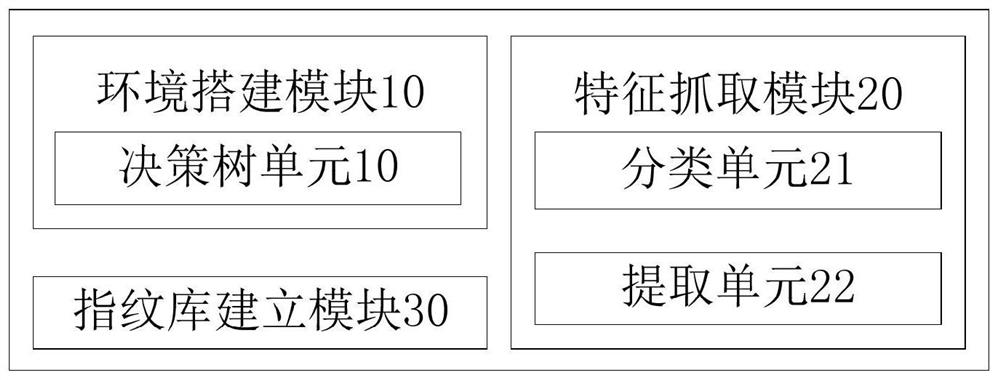
[0050] Such as image 3 As shown, the present embodiment provides a fingerprint library system based on the features of WEB attack tools, including: an environment building module 10, a feature capture module 20, and a fingerprint library building module 30;
[0051] The environment building module 10 is used to set up the feature capture environment of WEB attack tool, feature capture environment includes WEB attack tool host and feature capture target machine, attacking and / or scanning tools run on the WEB attack tool host, The traffic capture tool is running on the feature capture target machine;
[0052] Specifically, the WEB attack tool host is mainly installed with mainstream WEB attack and scanning tools, such as: system-type BT5, kali, Parrot, BackBox and other web-scanning attack systems; scanning-type Nikto, WebInspect, Burpsuite, Acunetix Web Vulnerability Scanner (AWVS ), AppScan, NMAP, SQLMAP and other scanning attack applications;
[0053] Feature Capture The t...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com