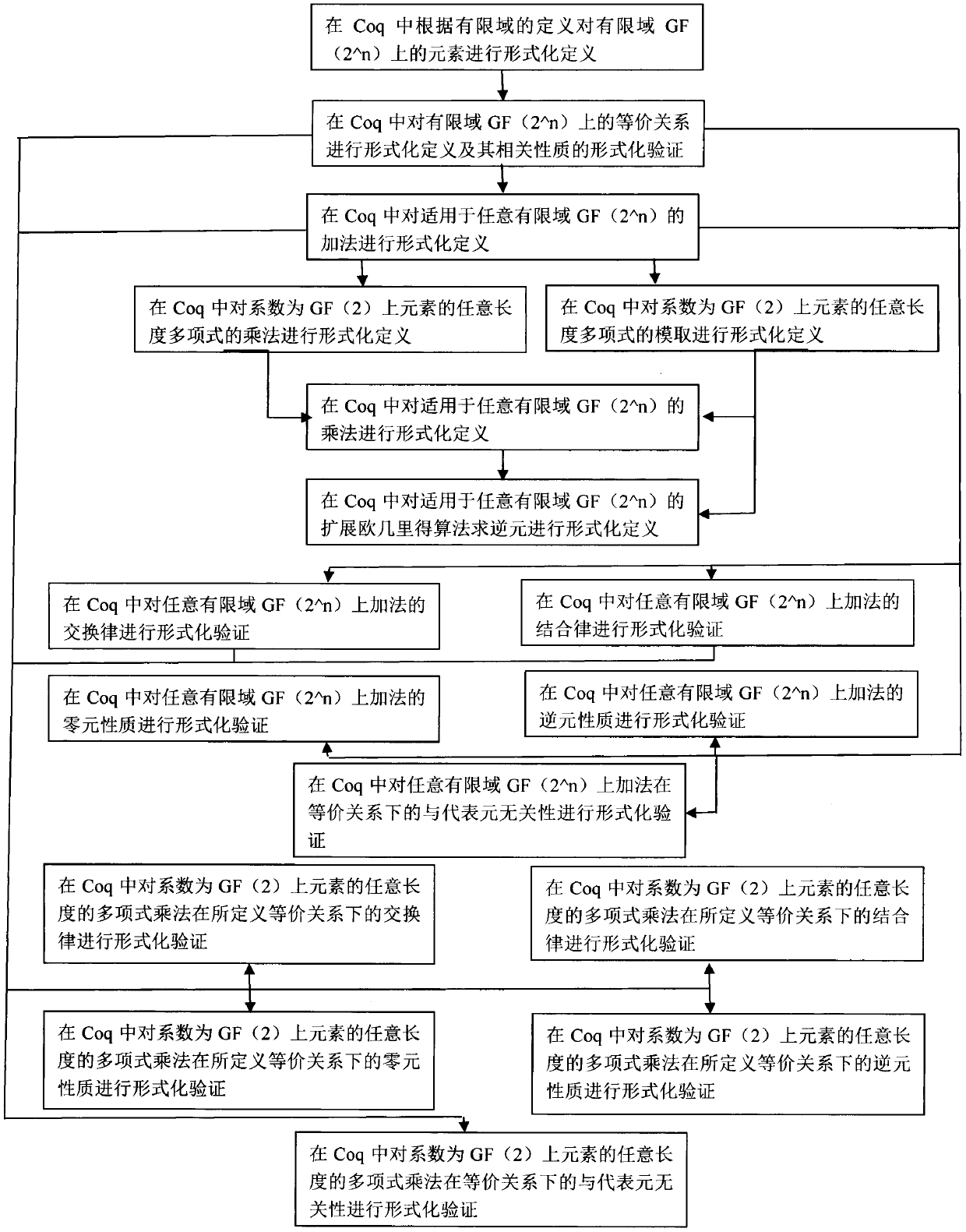
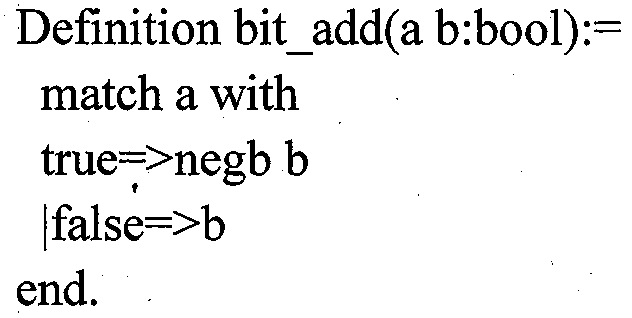
Formalized verification method of finite field GF(2 ^ n) based on Coq
A formal verification, finite field technology, applied in the formal verification supporting encryption algorithm and modular multiplication operation, the security software reliability verification field based on the theorem prover Coq, can solve the problem of mathematical derivation and mathematical algorithm reliability verification and other problems to avoid mistakes
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment example
[0098] The invention can be used to generate finite-field multiplicative masks against side-channel attacks.
[0099] According to the paper "On Masked Galois-Field Multiplication for Authenticated Encryption Resistant to Side Channel Analysis" published by Hirokazu Oshida et al., finite field multiplication can be used to generate masks against side channel attacks, and the present invention provides a formal definition that can Method for multiplication over finite fields GF (2^n) of arbitrary length and size.
[0100] The invention can be used to verify the column confusion part in the AES algorithm. In the column confusion process of the AES algorithm, the operation on the finite field GF (2^8) is used to realize the confusion operation. The addition and multiplication operations defined in the invention Can be used for column obfuscation operation, set to (a 0 a 1 a 2 a 3 ) performs a column obfuscation operation, and the result is (b 0 b 1 b 2 b 3 ),
[0101...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com