Measuring method, equipment and system based on trusted high-speed encryption card
An encryption card and equipment technology, applied in the transmission system, digital transmission system, secure communication device, etc., can solve the problem of not being able to ensure the active measurement of the platform system at the same time
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0050] According to the embodiment of the present application, an embodiment of a measurement method based on a trusted high-speed encryption card is provided. It should be noted that the steps shown in the flow chart of the accompanying drawing can be implemented in a computer system such as a set of computer-executable instructions and, although a logical order is shown in the flowcharts, in some cases the steps shown or described may be performed in an order different from that shown or described herein.
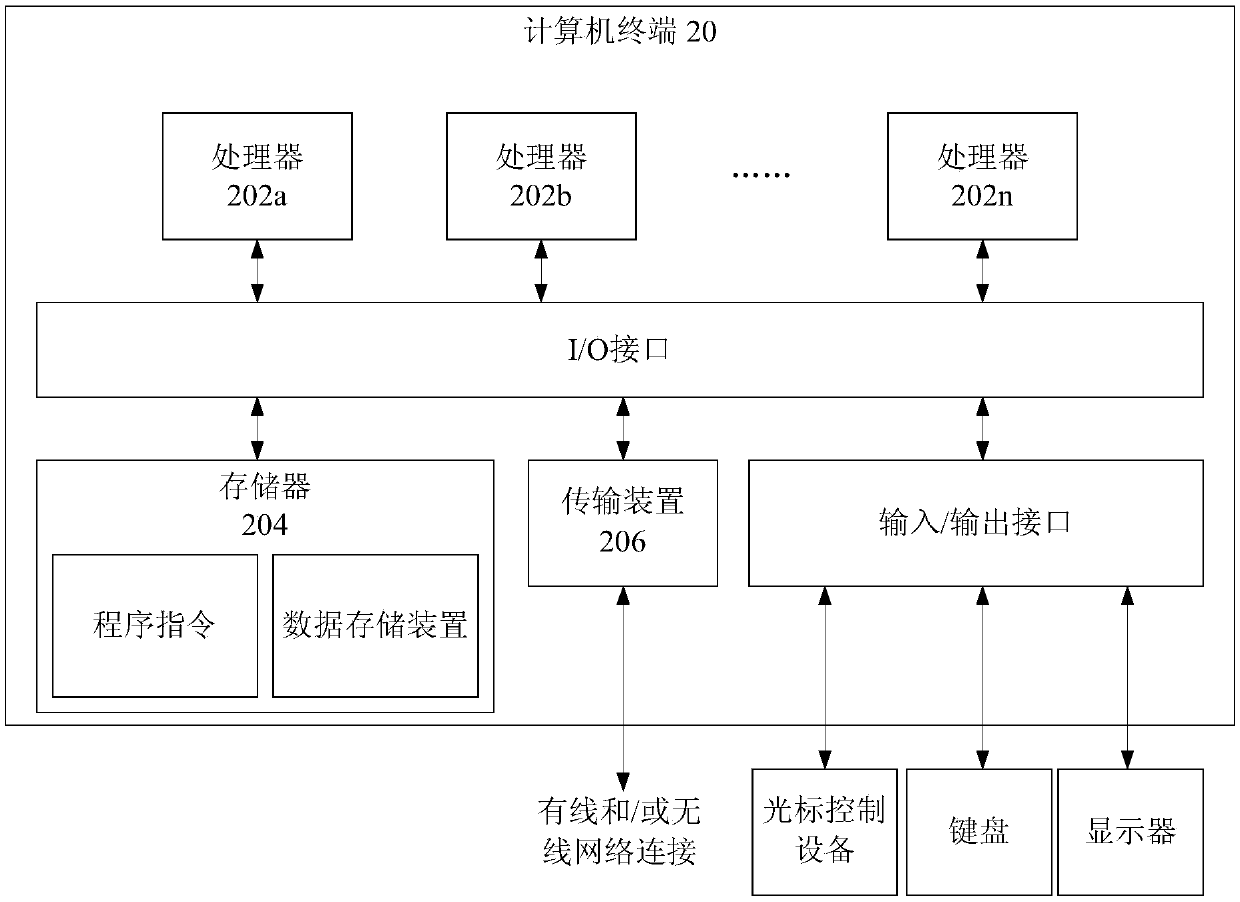
[0051] The method embodiment provided in Embodiment 1 of the present application may be executed in a mobile terminal, a computer terminal, or a similar computing device. figure 2 It shows a hardware structure block diagram of a computer terminal (or mobile device) for realizing the measurement method based on the trusted high-speed encryption card. Such as figure 2 As shown, the computer terminal 20 (or mobile device 20) may include one or more (202a, 202b, . or a pr...
Embodiment 2
[0123] According to the embodiment of the present application, an embodiment of a measurement method based on a trusted high-speed encryption card is also provided. It should be noted that the steps shown in the flow chart of the accompanying drawing can be implemented in a computer such as a set of computer-executable instructions system, and, although a logical order is shown in the flowcharts, in some cases the steps shown or described may be performed in an order different from that shown or described herein.
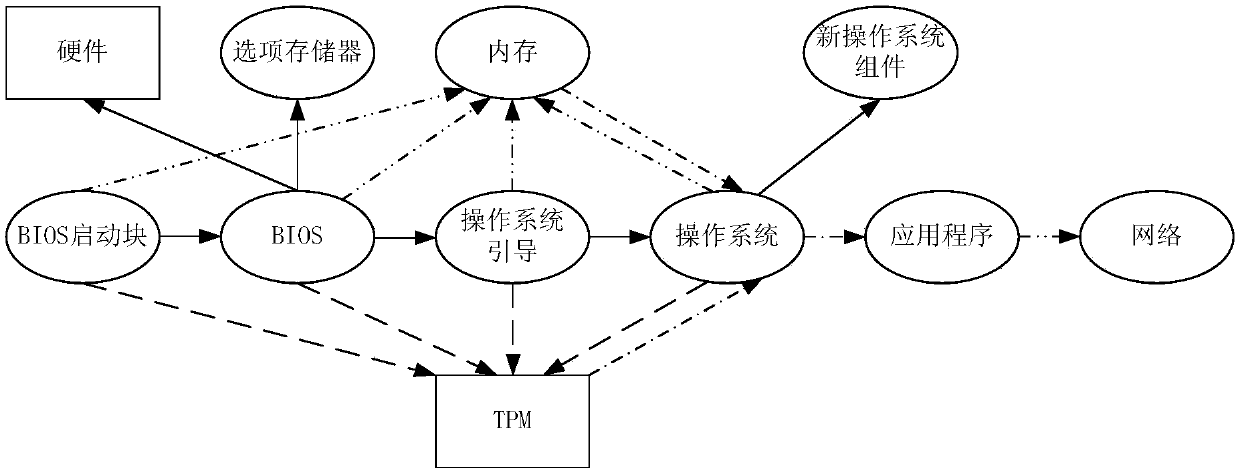
[0124] Under the above operating environment, this application provides such Figure 6 Metrics based on trusted high-speed encryption cards shown.
[0125] Specifically, the above-mentioned trusted high-speed encryption card may be the same as the trusted high-speed encryption card in Embodiment 1, and details are not described here.
[0126] Figure 6 It is a flowchart of a measurement method based on a trusted high-speed encryption card according to Embodiment 2...
Embodiment 3
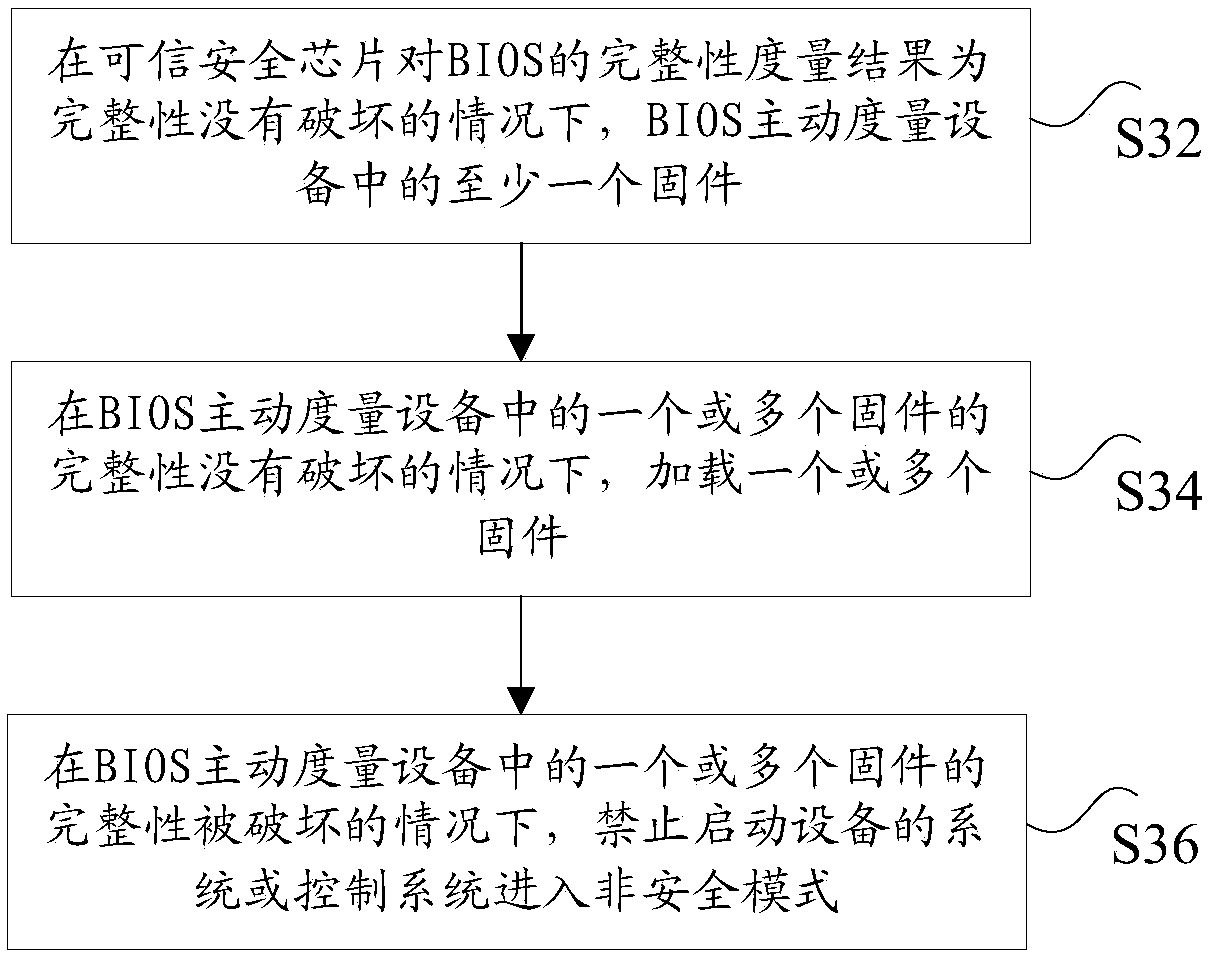
[0191] According to an embodiment of the present application, a measurement device based on a trusted high-speed encryption card for implementing the above-mentioned measurement method based on a trusted high-speed encryption card is also provided, such as Figure 9 As shown, the device 900 includes: a first measurement module 902 , a loading module 904 and a control module 906 .
[0192] Among them, the measurement module 902 is used to actively measure at least one firmware in the device by the BIOS when the integrity measurement result of the trusted security chip on the BIOS is that the integrity is not damaged; the loading module 904 is used to actively measure the firmware in the device by the BIOS. When the integrity of one or more firmwares is not damaged, load one or more firmwares; the control module 906 is used to prohibit starting the device when the integrity of one or more firmwares in the BIOS active measurement device is damaged The system or control system ent...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com