Attack data cleaning method, device, apparatus, storage medium and system
A technology for attacking data and equipment, which is applied in the field of computer networks, can solve problems affecting network transmission speed and achieve the effect of guaranteeing transmission speed
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach
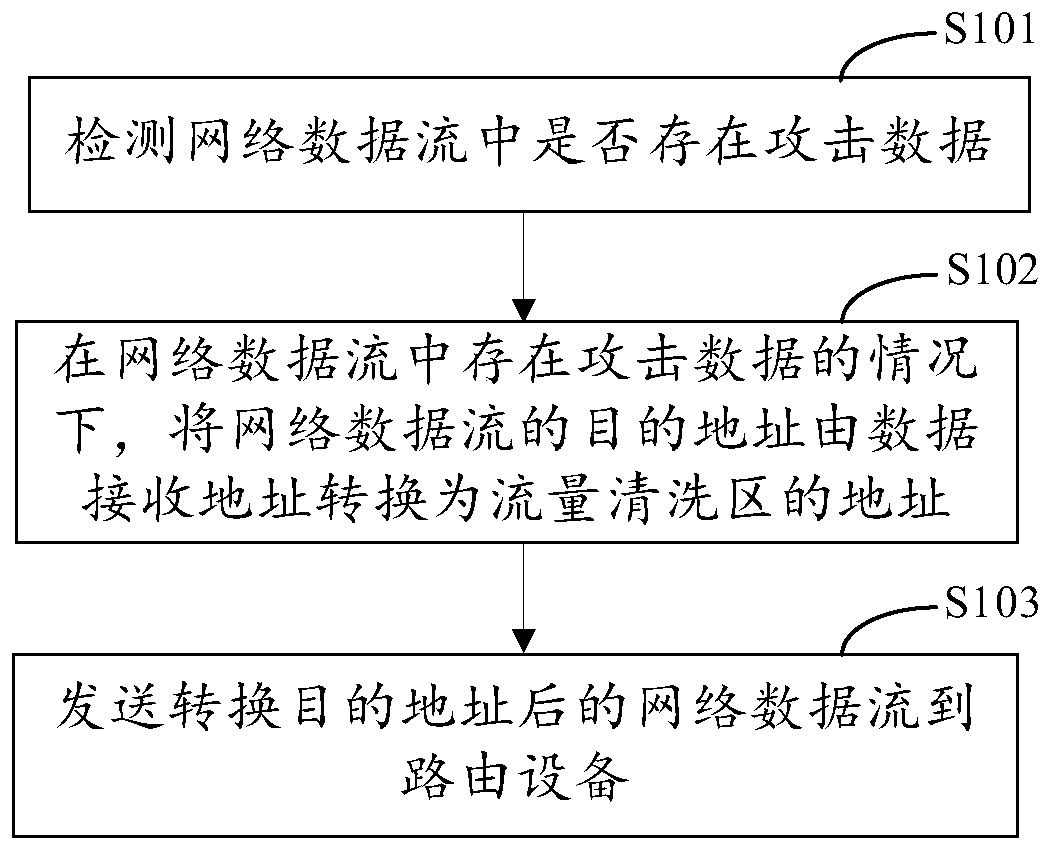
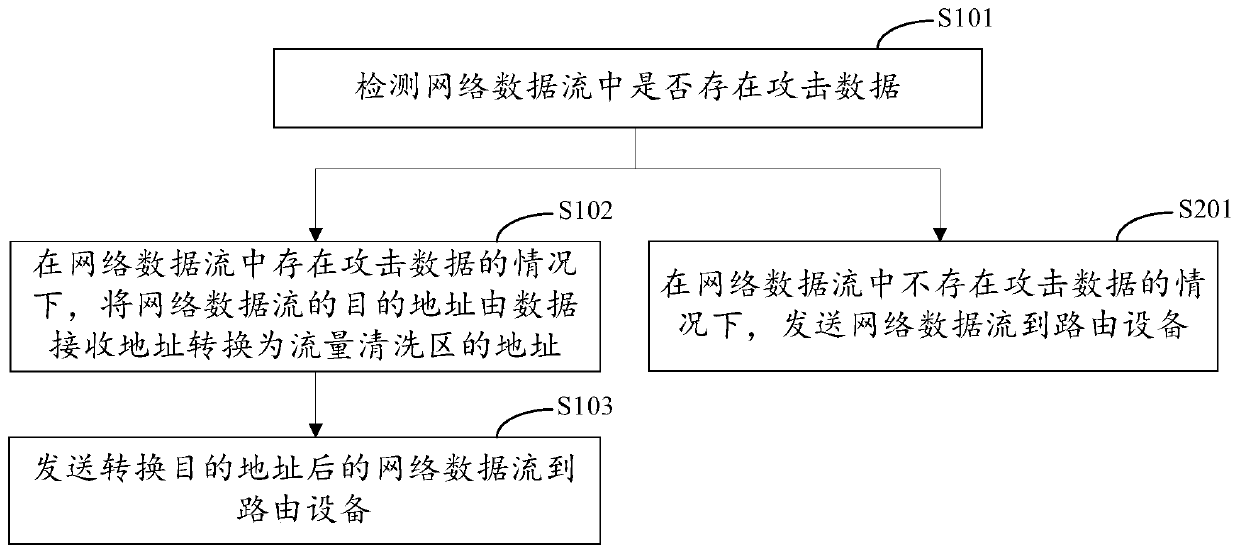
[0052] As an exemplary implementation, such as figure 2 As shown, the attack data cleaning method provided in the embodiment of the present application, after detecting whether there is attack data in the network data stream, further includes:
[0053] Step S201. In the case that there is no attack data in the network data stream, send the network data stream to the routing device.
[0054] In an exemplary embodiment, if there is no attack data in the network data stream, the network data stream can be directly sent to the routing device, and the transmission speed of normal data will not be affected by cleaning the attack data.
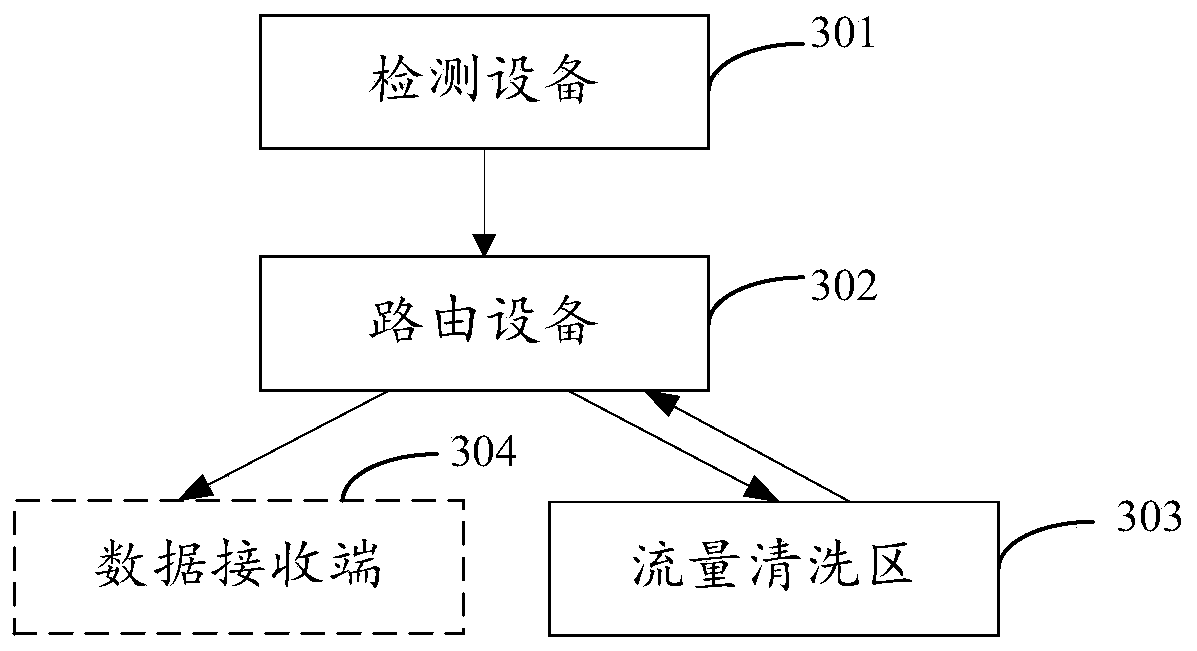
[0055] The attack data cleaning method provided in the embodiment of the present application can be applied to a detection device. The detection device can detect whether there is attack data to determine whether to convert the destination address of the network data flow before sending the network data flow to the routing device. The normal netwo...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com