Distributed system sensitive data transmission protection method and device
A distributed system and sensitive data technology, applied in the field of network security, can solve problems such as vulnerability to attack, troublesome application operation, integration, etc., and achieve the effect of preventing theft and illegal transmission and ensuring integrity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0039] The technical solutions of the embodiments of the present invention will be clearly and completely described below in conjunction with the accompanying drawings of the present invention.
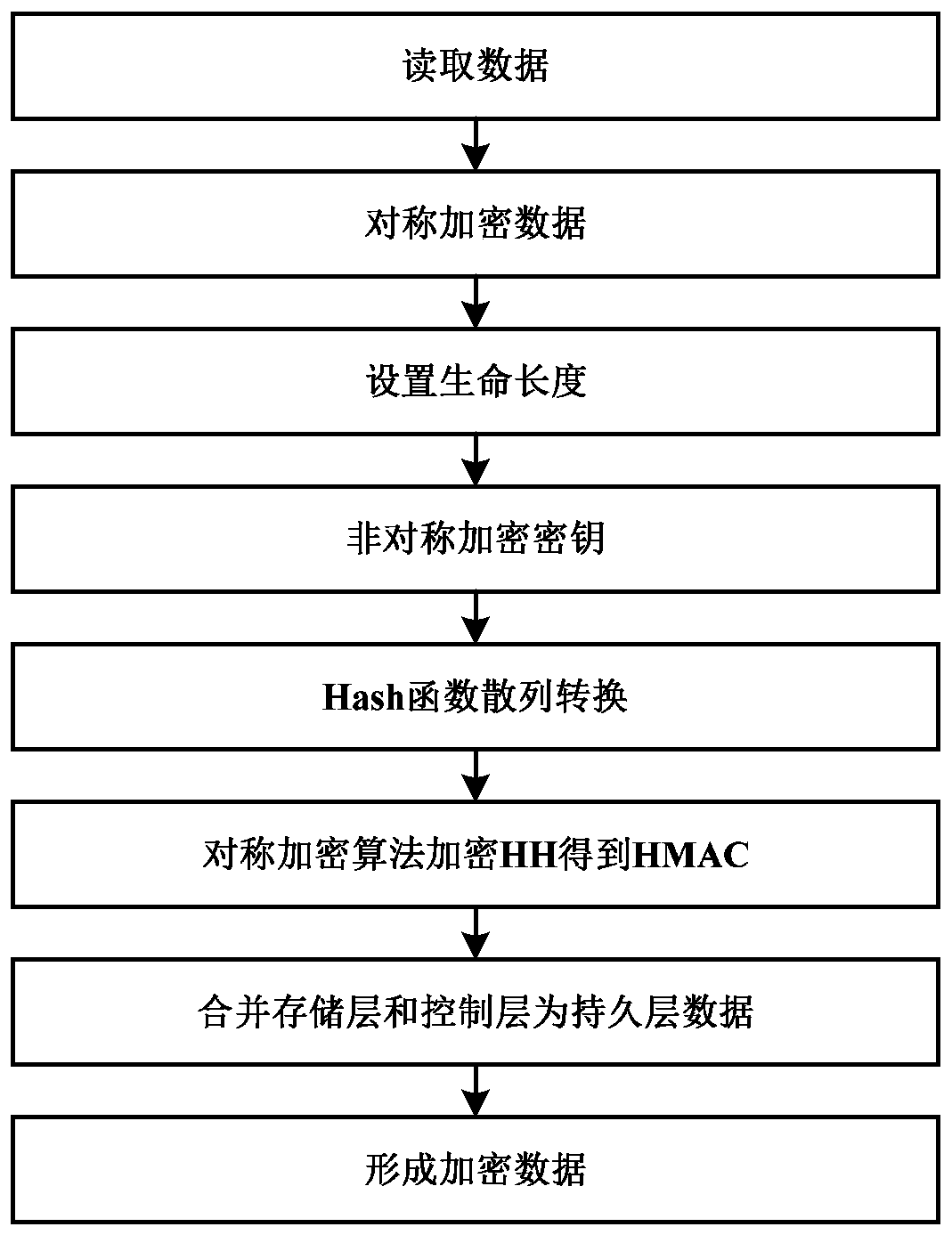
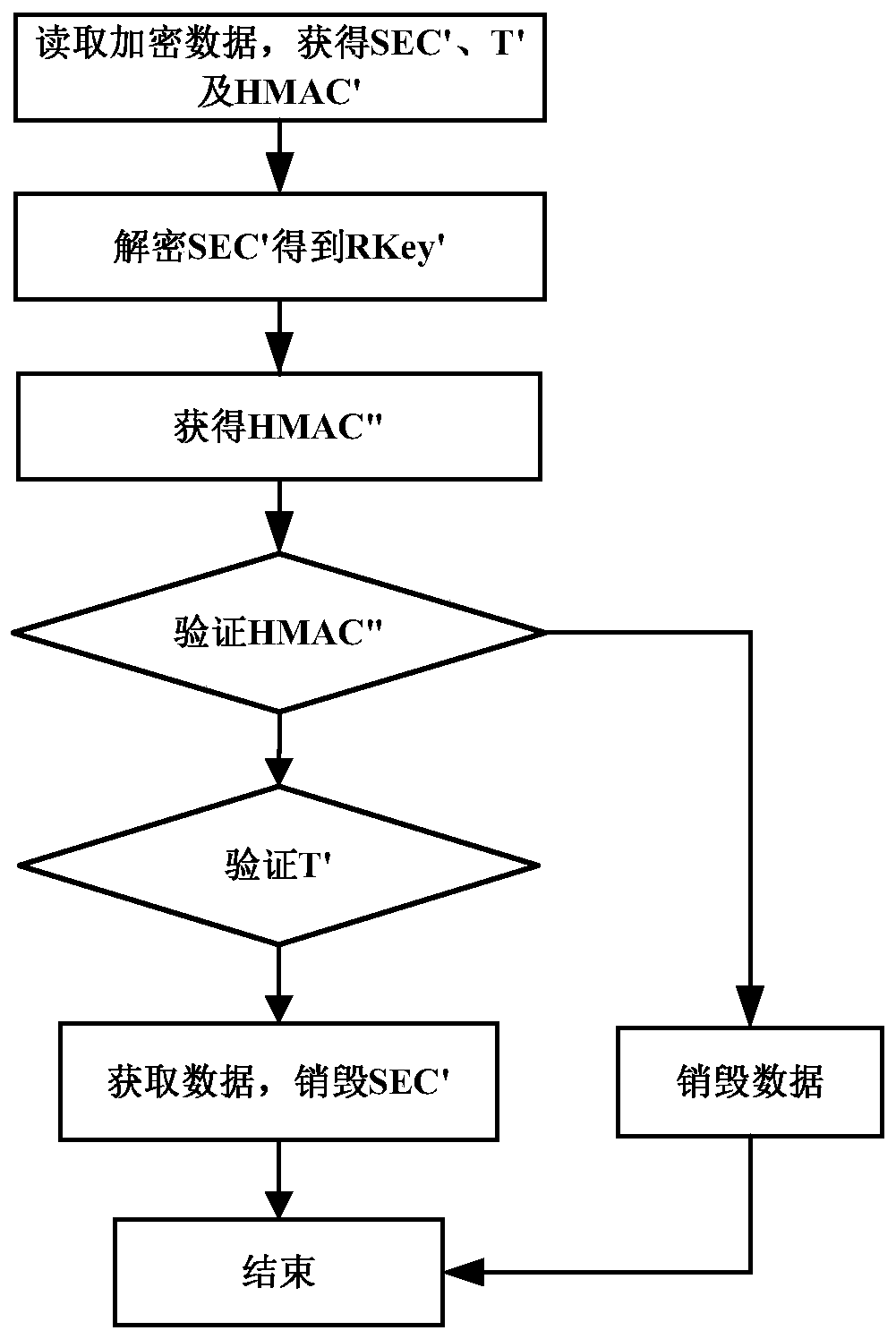
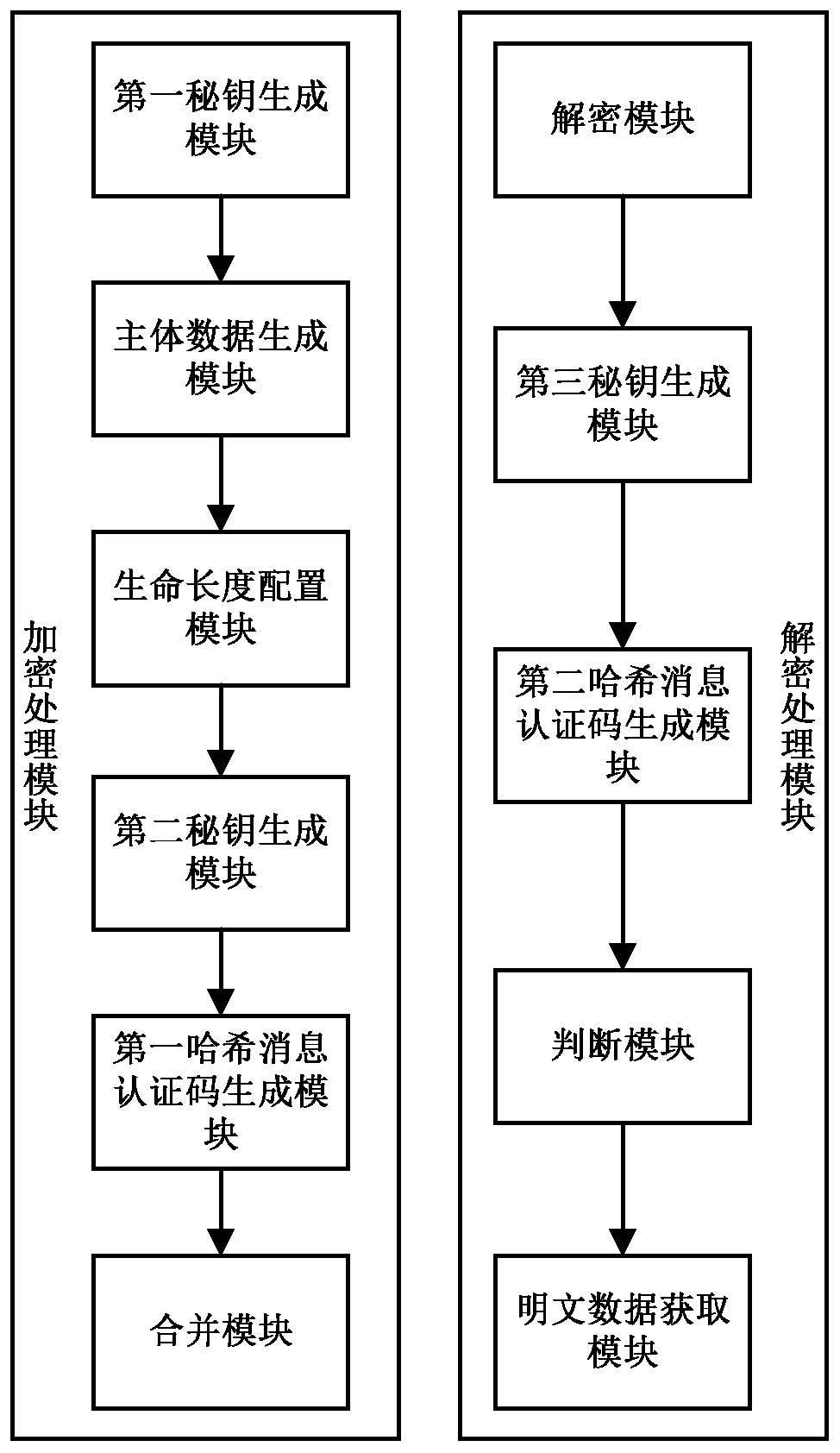
[0040] The sensitive data transmission protection method disclosed in the present invention is applied to a distributed system. The distributed system includes several nodes. The method includes that each node performs encryption processing and decryption processing, wherein, such as figure 1 As shown, the encryption process includes the following steps:
[0041] Step S100, randomly generate a symmetric key RKey, encrypt the read data through the symmetric key RKey, generate the main body data Body, configure the life length T of the data at the same time, and perform asymmetric encryption on the symmetric key RKey Encryption processing to generate encrypted symmetric key SEC;
[0042] Specifically, during the data transmission process, the node encrypts the data, and the node random...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com