Unified identity management and authentication method based on blockchain
An authentication method and identity management technology, applied in digital data authentication, electrical digital data processing, special data processing applications, etc., can solve problems such as difficulty in meeting heterogeneous networks, and achieve the effect of ensuring privacy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
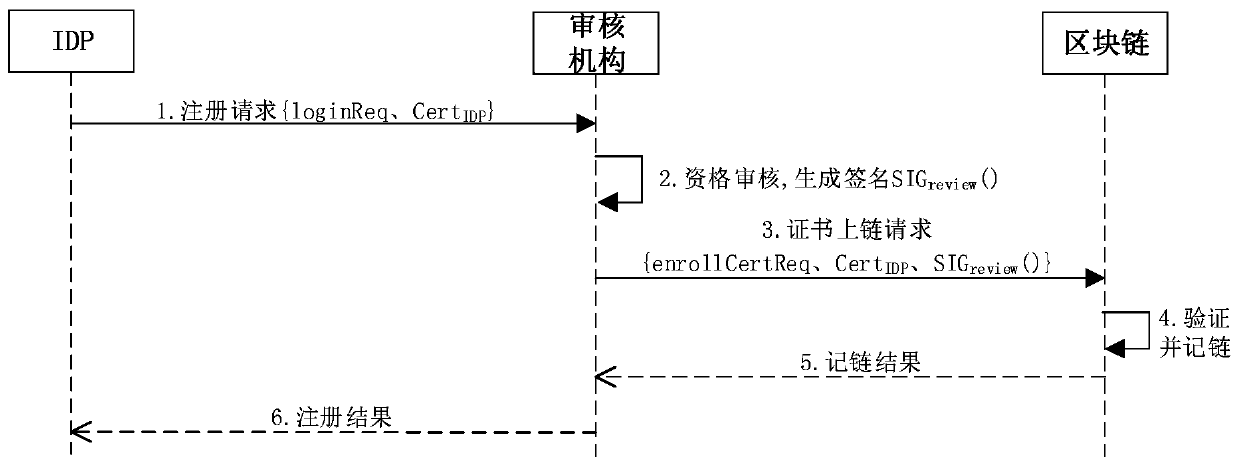
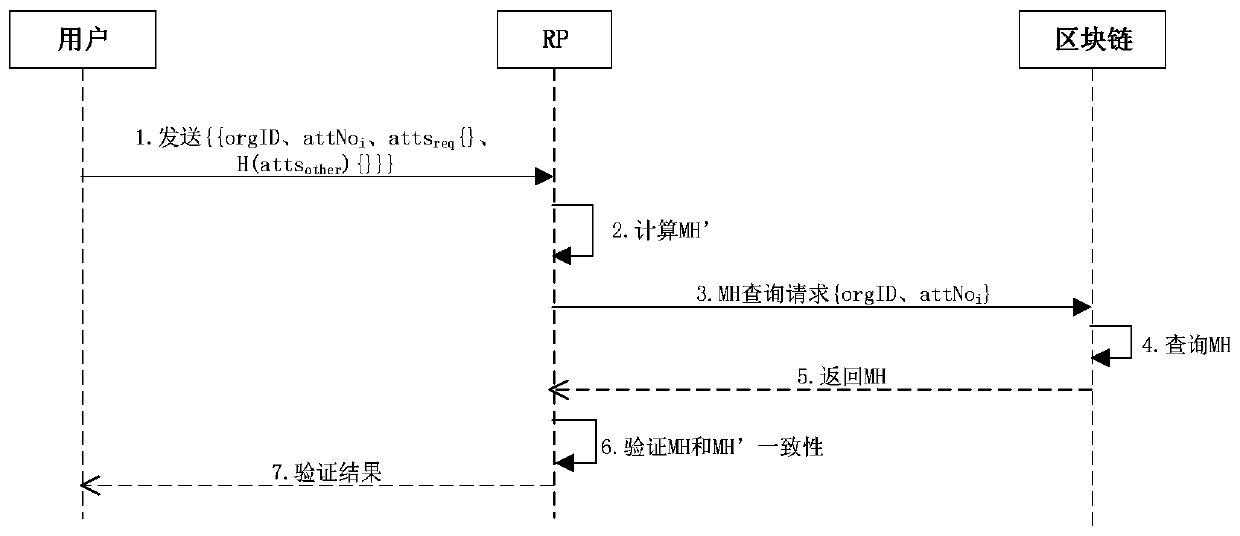
[0019] A blockchain-based unified identity management and authentication method, including the following:
[0020] The heterogeneous identity alliance maintains the identity alliance chain through distributed joint management. Each identity provider stores its own entity ID and corresponding hash through the connection on the chain, and different entity IDs of the same user cannot be associated, realizing the privacy of user identity information Protect. In addition, the entire alliance chain will not store the plaintext information of the user's identity, but provide credible verification in the form of a hash summary, which not only protects user privacy, but also provides unified identity management services to the outside world.
[0021] The public key signature algorithm used in the present invention is the SM2 signature algorithm (GM / T 0003), and the hash algorithm used is the SM3 hash algorithm (GM / T 0004).
[0022] The technical solution of the present invention is di...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com