Method and device for identifying illegal machine card separation of Internet of Things
A technology for illegal machine cards and IoT cards, applied in the field of IoT, can solve problems such as errors in the identification code of IoT cards, and achieve the effect of ensuring safety and accurate identification methods.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
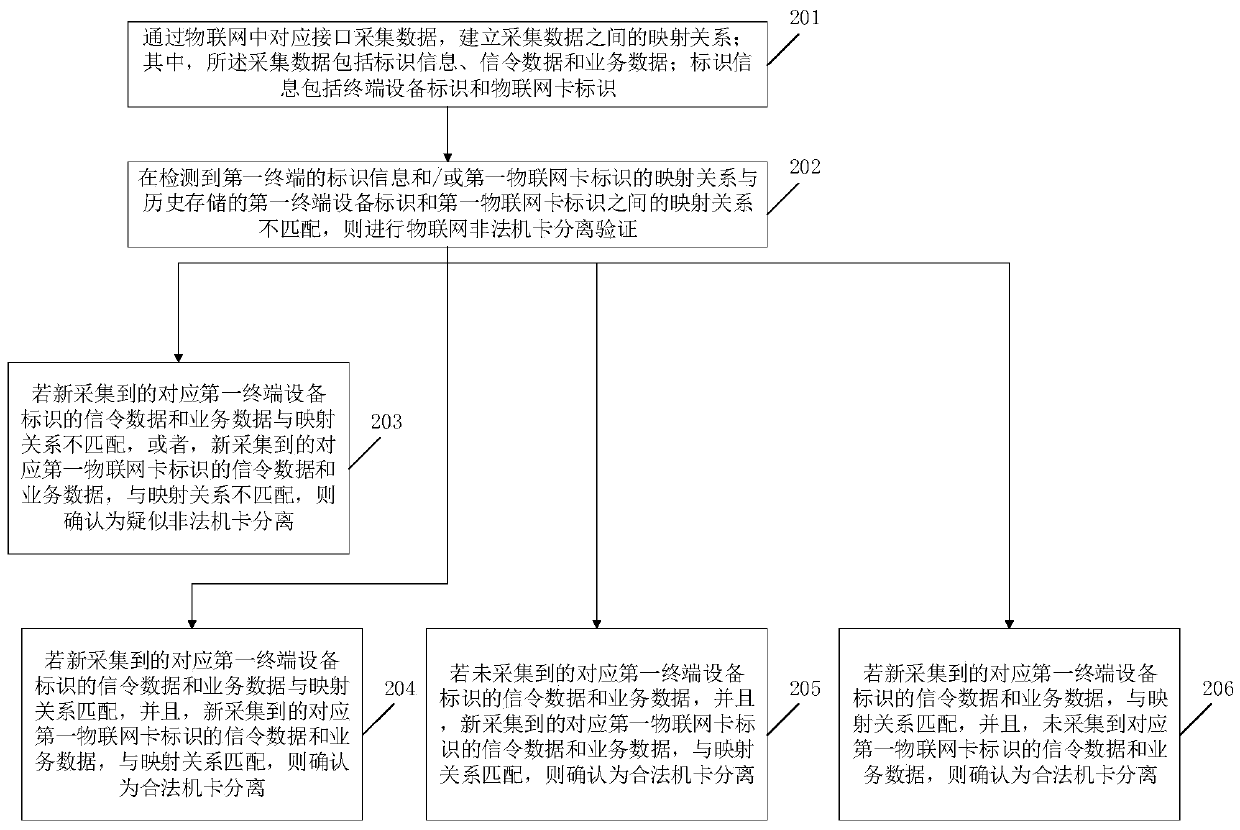
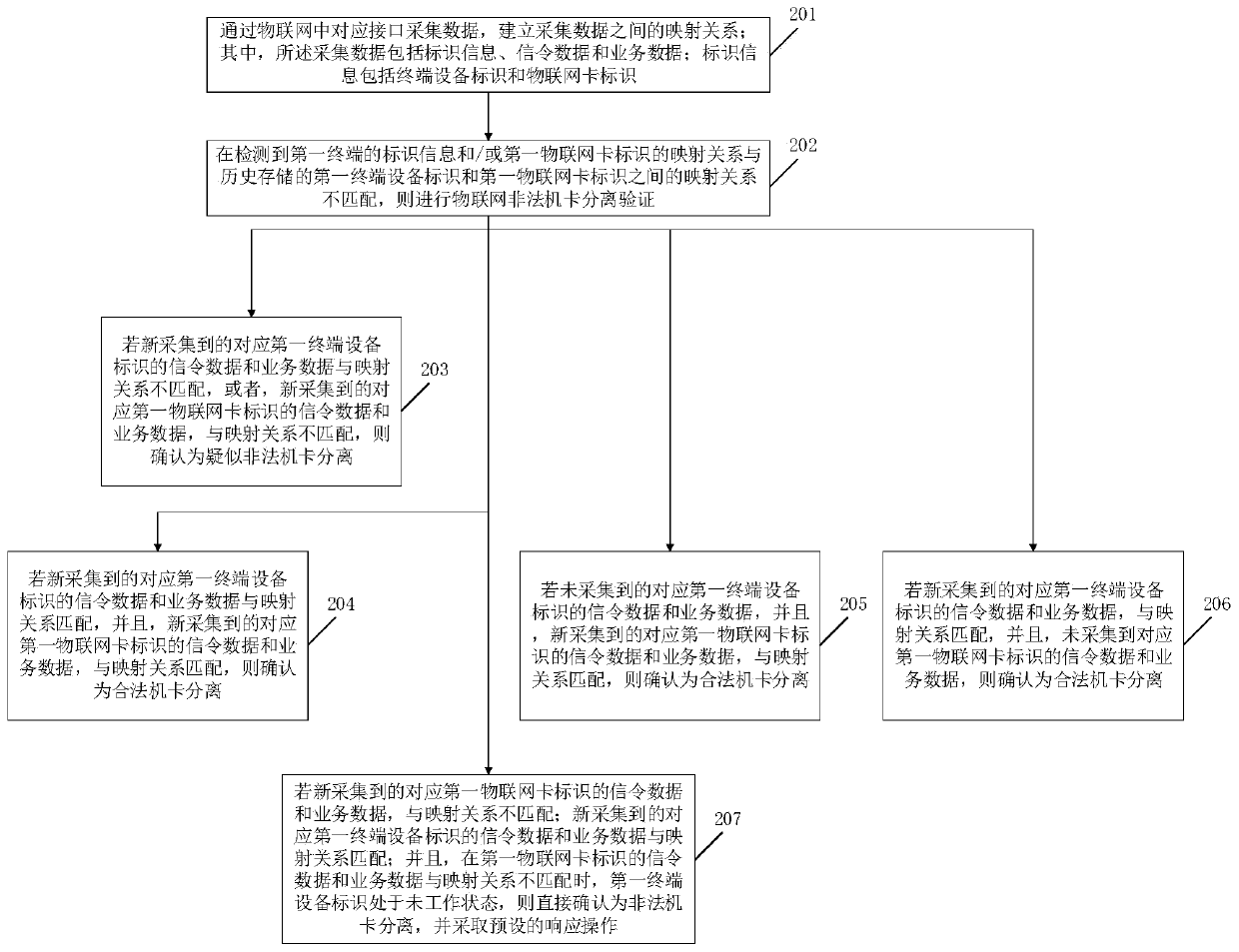
[0045] Embodiment 1 of the present invention provides a method for separating and identifying illegal machine cards in the Internet of Things, such as figure 1 shown, including:
[0046] In step 201, collect data through the corresponding interface in the Internet of Things, and establish a mapping relationship between the collected data; wherein, the collected data includes identification information, signaling data and service data; identification information includes terminal equipment identification and the Internet of Things card logo.
[0047] Among them, the terminal equipment identification is specifically the International Mobile Equipment Identity (International Mobile Equipment Identity, abbreviated as: IMEI), and the IMEI is the number burned into the IoT terminal equipment by the manufacturer when the equipment leaves the factory; Digital Network (Mobile Subscriber International ISDN / PSTN Number, abbreviated as: MSISDN) and / or International Mobile Subscriber Iden...
Embodiment 2
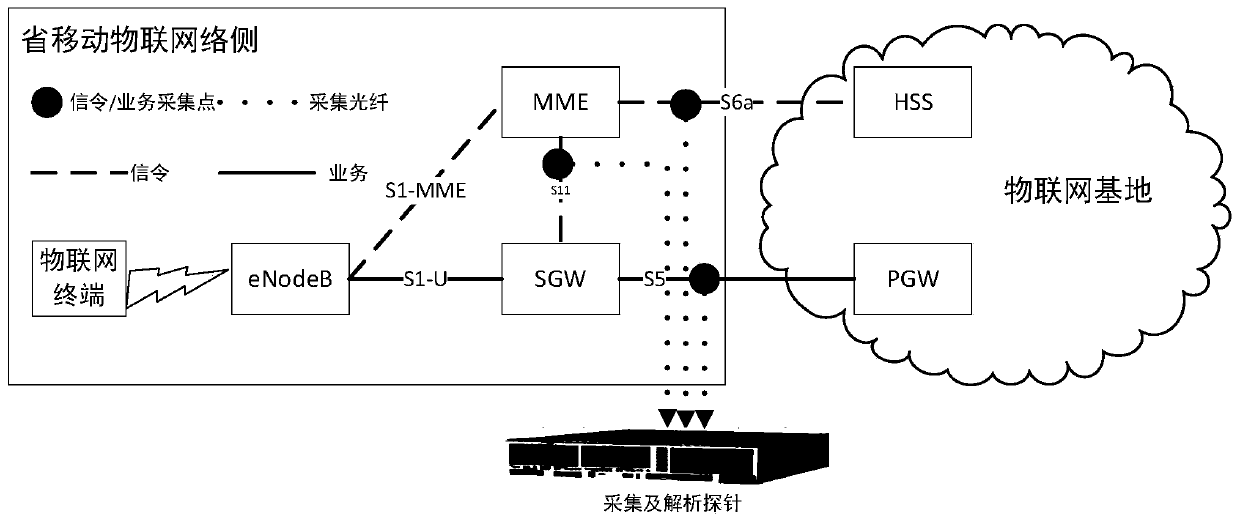
[0077] Such as Figure 4 As shown, it is a schematic diagram of the architecture of the device for separating and identifying illegal machine cards in the Internet of Things according to an embodiment of the present invention. The device for separating and identifying illegal machine cards in the Internet of Things in this embodiment includes one or more processors 21 and memory 22 . in, Figure 4 A processor 21 is taken as an example.
[0078] Processor 21 and memory 22 can be connected by bus or other means, Figure 4 Take connection via bus as an example.
[0079] The memory 22, as a non-volatile computer-readable storage medium, can be used to store non-volatile software programs and non-volatile computer-executable programs, such as the method for separating and identifying illegal machine cards in the Internet of Things in Embodiment 1. The processor 21 runs the non-volatile software programs and instructions stored in the memory 22, thereby executing the method for ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com