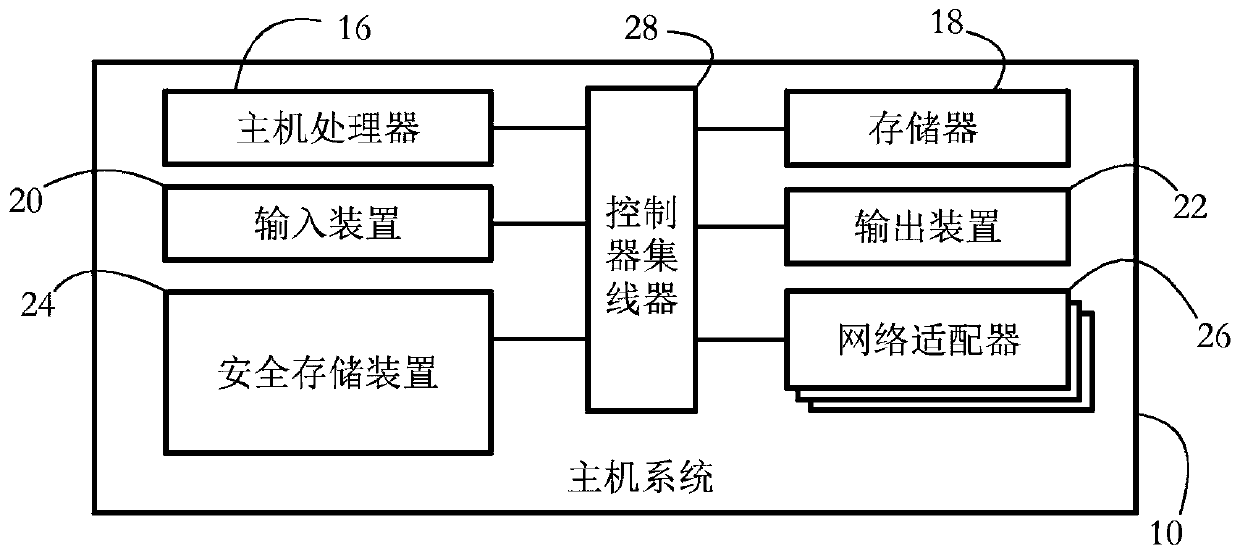
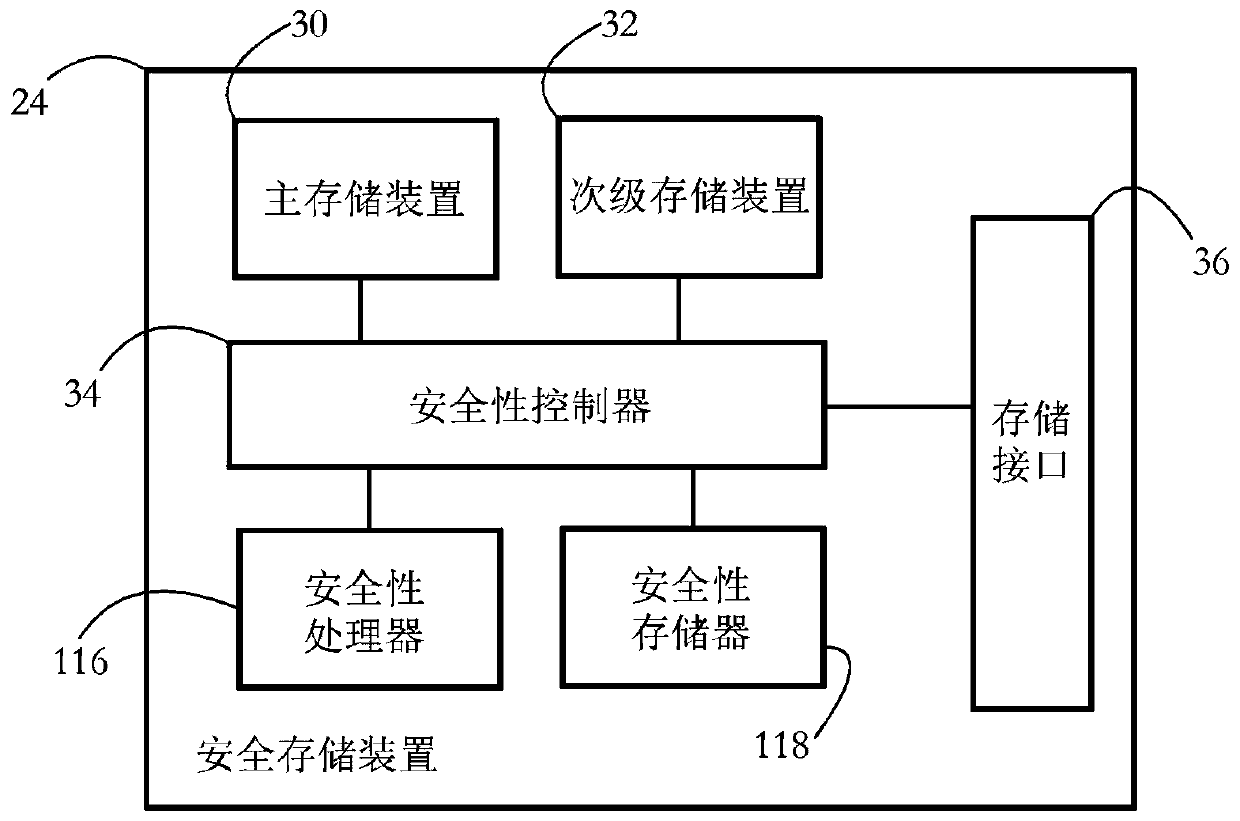
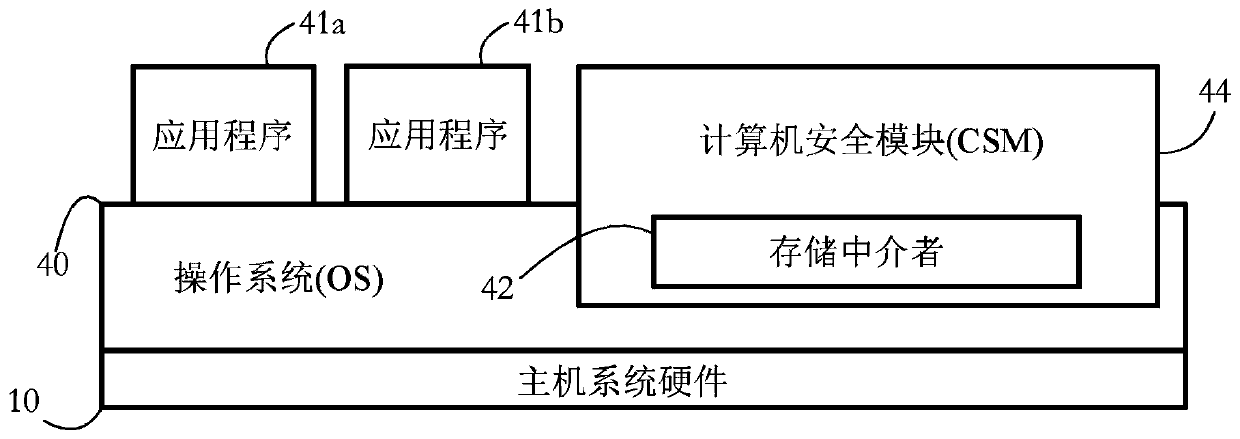
Secure storage device
A storage device and secure storage technology, applied in computer security devices, instruments, transmission systems, etc., can solve problems such as loss of data and sensitive information, identity theft, productivity, loss, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0019] In the following description, it should be understood that all recited connections between structures may be direct operative connections, or indirect operative connections through intermediate structures. A component set contains one or more components. Any reference to an element should be understood to mean at least one element. A plurality of elements includes at least two elements. Unless otherwise required, any described method steps do not necessarily have to be performed in the particular illustrated order. Deriving a first element (eg, data) from a second element encompasses that the first element is equal to the second element, and that the first element is generated by processing the second element and optionally other data. Making a determination or decision based on parameters encompasses making a determination or decision based on parameters and optionally other data. Unless otherwise specified, an indicator of a quantity / data may be the quantity / data i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com