Front-end test method of distributed communication system
A technology of distributed communication and testing methods, applied in the field of front-end testing of distributed communication systems, can solve the problems of wasting testing time, testing errors, and testing process errors, improving efficiency and accuracy, avoiding malicious tampering, and ensuring stability sexual effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
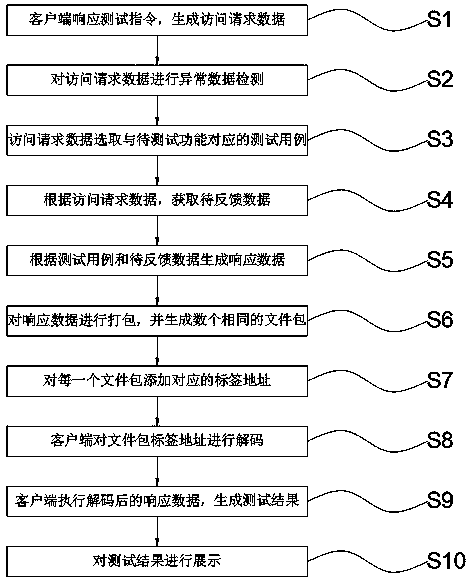
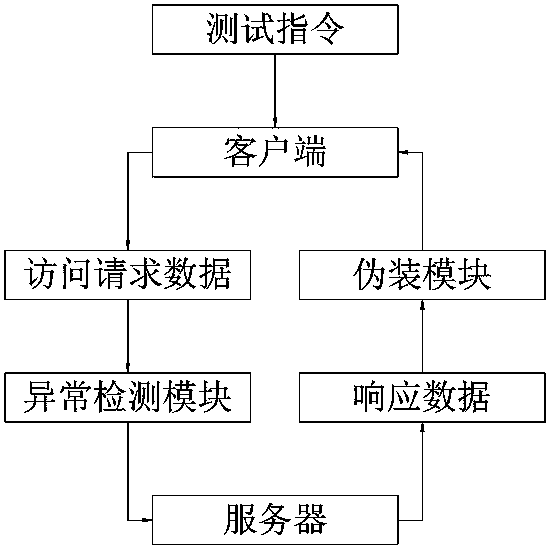
[0085] The client responds to the test command and generates access request data;
[0086] The anomaly detection module intercepts the access request data and performs anomaly detection;
[0087] If the access request data is abnormal, the client responds to the test command again and regenerates the access request data.
Embodiment 2
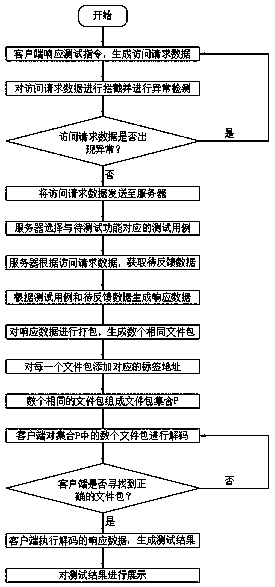
[0089] The client responds to the test command and generates access request data;
[0090] The anomaly detection module intercepts the access request data and performs anomaly detection;
[0091] The access request data is detected to be normal, and the access request data is sent to the server;
[0092] The server selects a test case corresponding to the function to be tested;
[0093] The server obtains the data to be fed back according to the access request data;
[0094] The server generates response data according to the test case and the data to be fed back;
[0095] The server packs the response data, and at the same time, generates nine identical file packages;
[0096] Ten file packages make up the response data file package set P={P 1 ,P 2 ,P 3 ,P 4 ,P 5 ,P 6 ,P 7 ,P 8 ,P 9 ,P 10};
[0097] The tag address corresponding to each file packet in the response data file packet set P is:
[0098] P 1 =(1,5),P 2 =(2,8),P 3 =(3,12),P 4 =(4,20),P 5 =(5,29)...
Embodiment 3
[0116] The client responds to the test command and generates access request data;
[0117] The anomaly detection module intercepts the access request data and performs anomaly detection;
[0118] The access request data is detected to be normal, and the access request data is sent to the server;
[0119] The server selects a test case corresponding to the function to be tested;
[0120] The server obtains the data to be fed back according to the access request data;
[0121] The server generates response data according to the test case and the data to be fed back;
[0122] The server packs the response data, and at the same time, generates nine identical file packages;
[0123] Ten file packages make up the response data file package set P={P 1 ,P 2 ,P 3 ,P 4 ,P 5 ,P 6 ,P 7 ,P 8 ,P 9 ,P 10};
[0124] The tag address corresponding to each file packet in the response data file packet set P is:
[0125] P 1 =(1,5),P 2 =(2,8),P 3 =(3,13),P 4 =(4,20),P 5 =(5,29)...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com