A tag-based policy configuration method and device
A policy configuration and label technology, applied in the field of network security, can solve the problem of inflexible policy management and achieve the effect of improving flexibility and efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
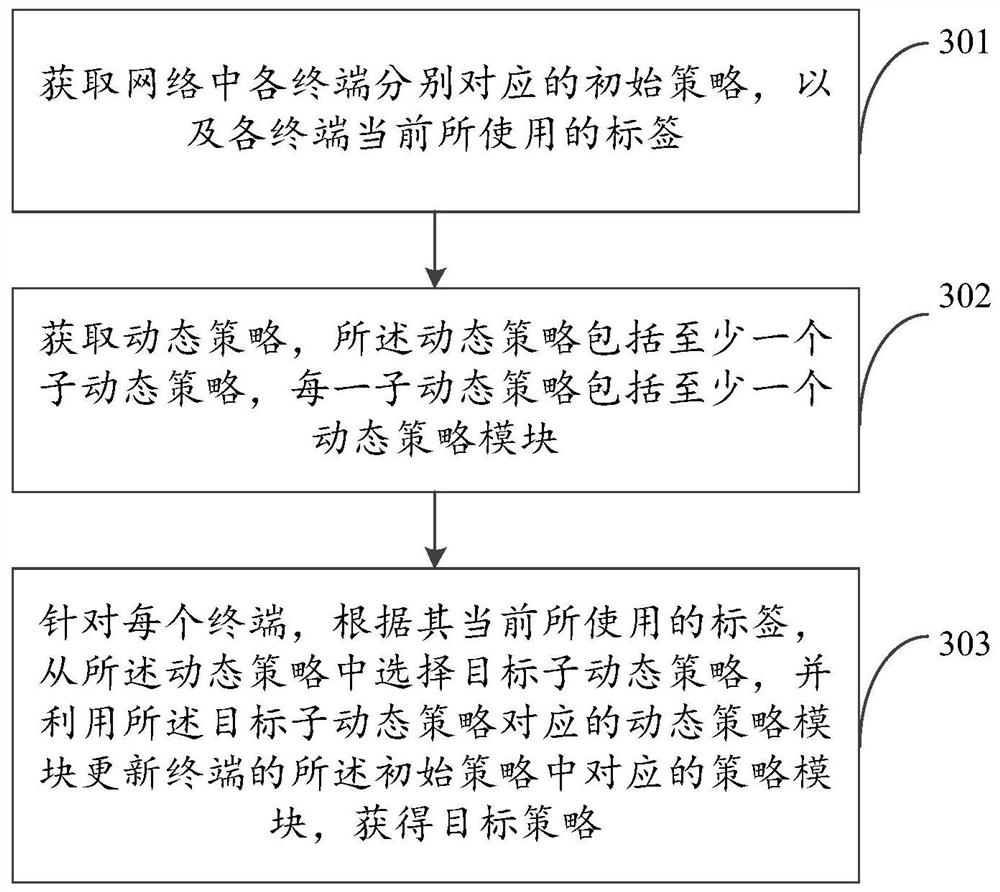
[0044] The technical solutions in the embodiments of the present application will be described below with reference to the drawings in the embodiments of the present application.
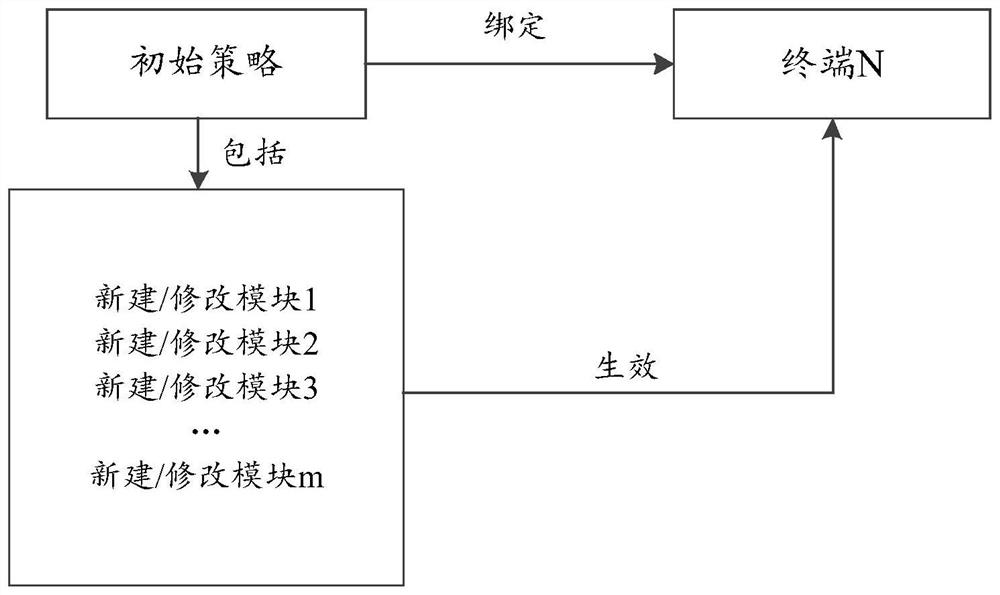
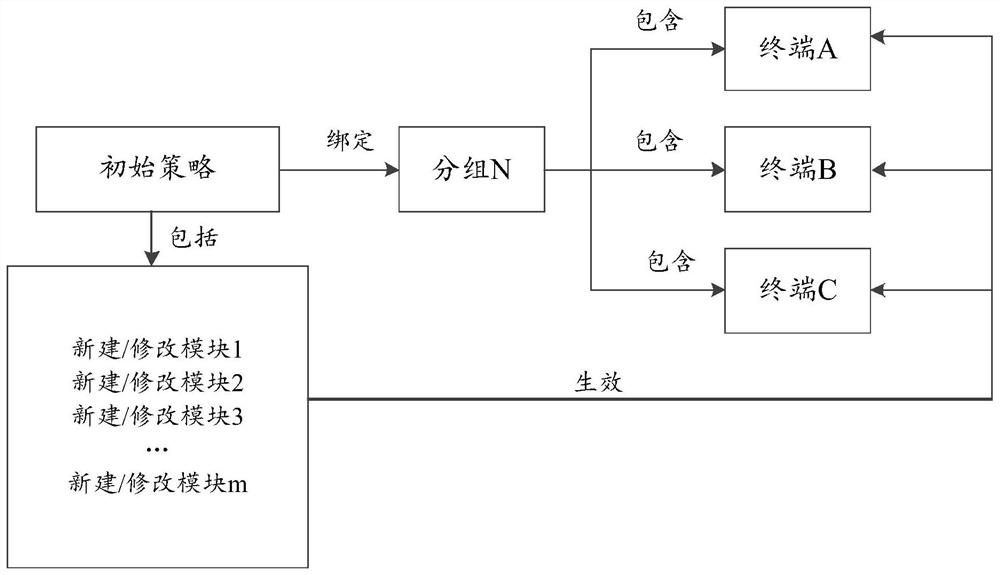
[0045] Prior to this application, the strategies required for different services of the terminal are different, therefore, it is necessary to dynamically adjust the strategy according to the current service situation of the terminal in real time. Among them, a policy refers to a set of rules for all related activities in a certain area. Policy management refers to the formulation, adjustment, and adaptation of the above rules. There are mostly two existing policy management methods, one is a terminal-based policy management method, and the other is a group-based policy management method.
[0046] figure 1 A schematic diagram of a terminal-based policy management method provided for the comparative embodiment, such as figure 1 As shown in , the modified policy is modified on the basis of the bound...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com