Portable network security attack and defense target range teaching device and use method thereof
A network security and teaching device technology, applied in the field of intelligent computer design, can solve problems such as error-prone, learners can't intuitively feel the importance of network security, the danger of network attack, and not obvious, so as to achieve the effect of improving the effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
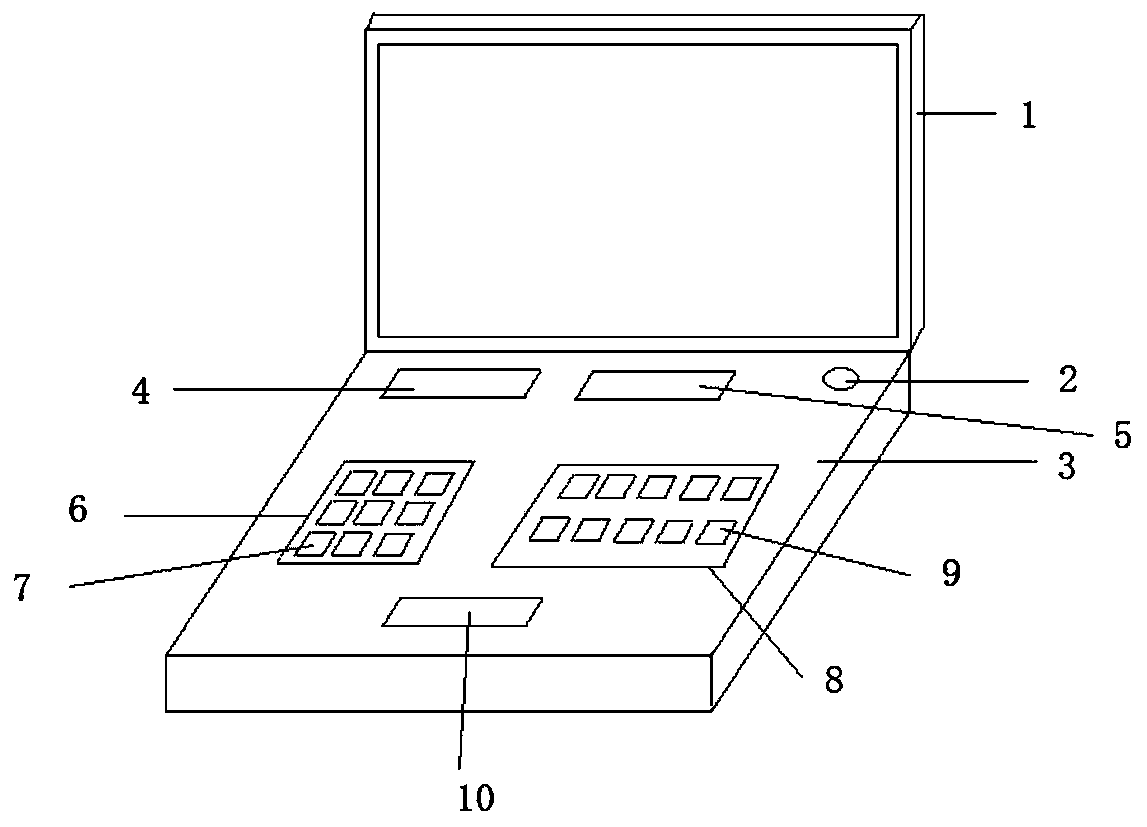
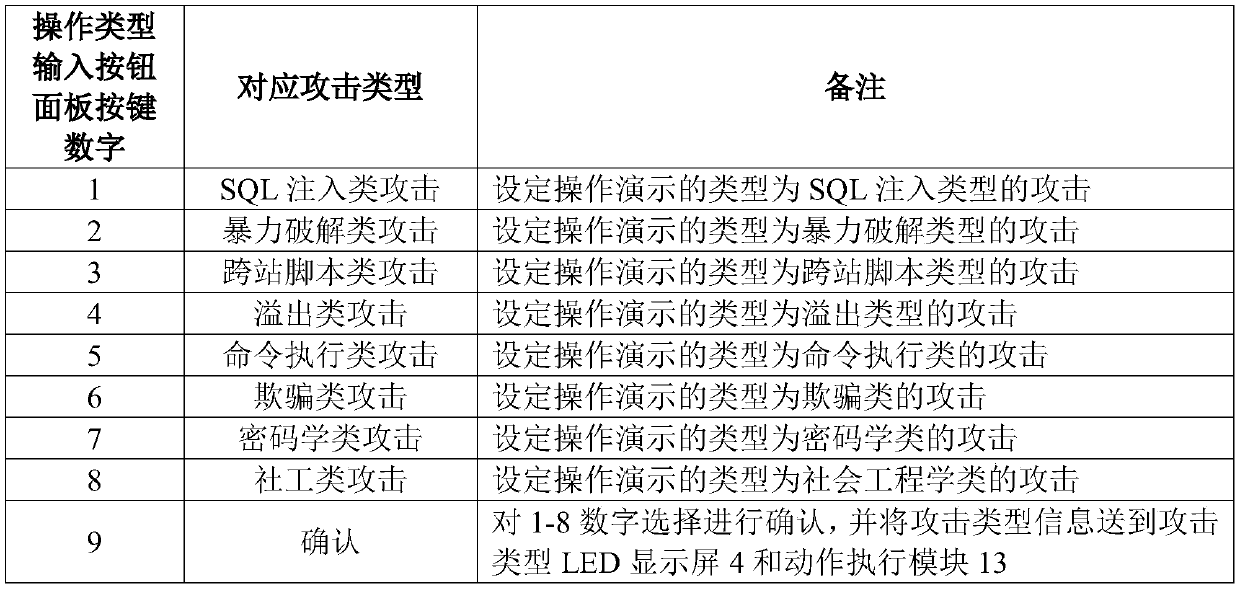
[0019] Such as figure 1 , figure 2 As shown, a portable network security attack and defense shooting range teaching device of the present invention includes a display 1, a computer host 3 connected to the display 1 through a connecting shaft, a power switch 2 arranged on the outer surface of the computer host 3, and an attack type LED display 4, attack command LED display screen 5, operation type input button panel 6, attack command input button panel 8 and start button 10, the operation type input button 7 arranged on the operation type input button panel 6 and attack command input button panel 8 respectively And the attack command input button 9, the operation type input button 7 includes eight attack type numeric buttons and a confirmation button, and the attack command input button 9 includes nine attack command numeric buttons and a confirmation button;
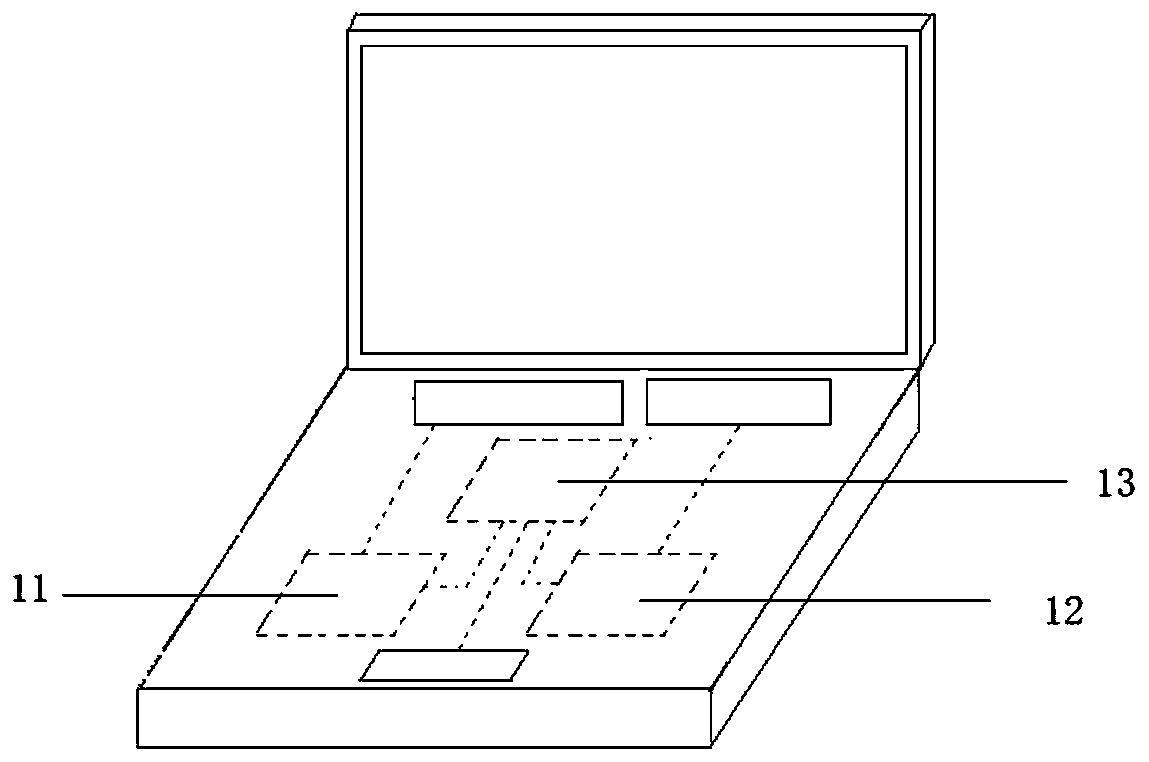
[0020] It also includes an operation type instruction translation module 11, an attack instruction translation modul...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com