Attribute-based connection keyword search method in multi-data owner environment
A technology for data owners and owners, applied in the field of keyword search, can solve problems such as reducing the computing cost of the client and increasing the number of keywords linearly
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0049] Now in conjunction with embodiment, accompanying drawing, the present invention will be further described:
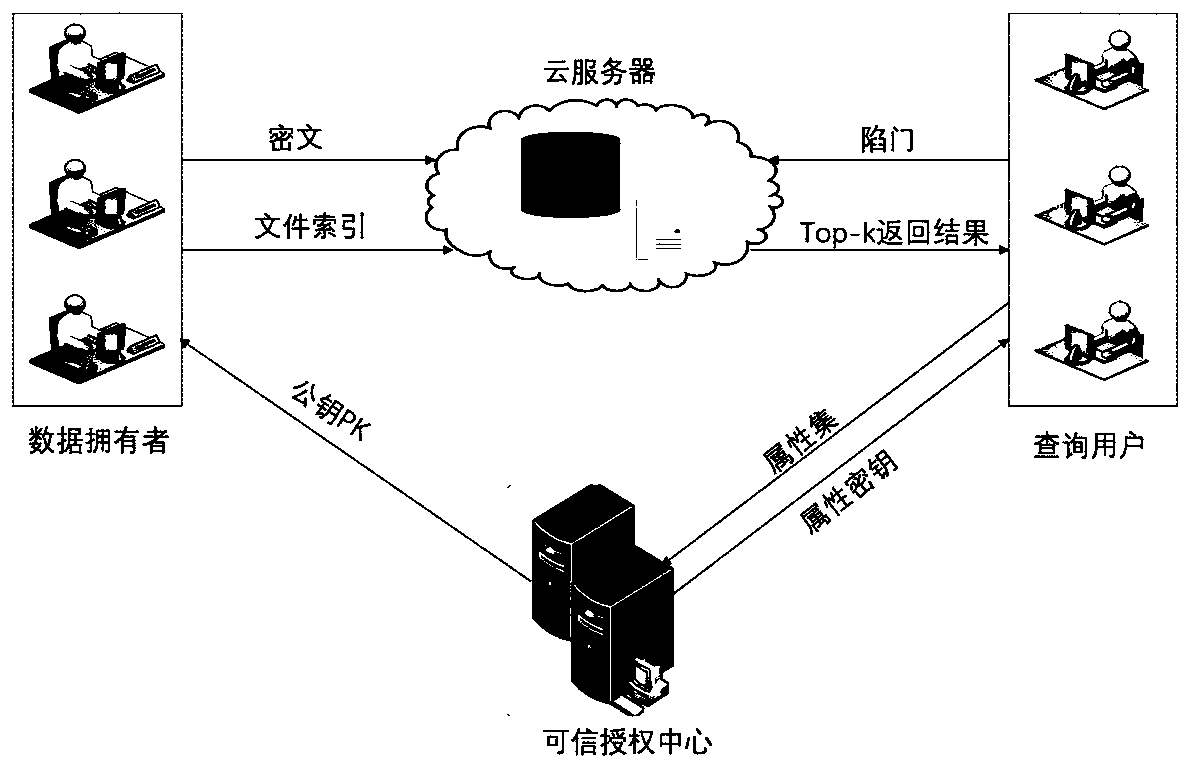
[0050] Consider a cloud storage system that implements join keyword search and fine-grained access control. The system includes multiple data owners, multiple query users, cloud servers and trusted authorization centers. The trusted authorization center is responsible for system initialization, generating system public parameters and master keys, and at the same time generating attribute private keys for query users. Data owners manage files and generate indexes. Query users to generate trapdoors for searching. The cloud server stores file ciphertext and file index, and uses powerful computing power to help users search.
[0051] The parameters involved in this method are defined as:
[0052] Table 1 Parameter definition
[0053]
[0054] The following are the specific implementation steps:
[0055] 1. System initialization.
[0056] Let H: {0, 1) * → ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com