DDoS attack detection method and device, computer equipment and storage medium
An attack detection and target device technology, applied in the field of network security, can solve the problems of low detection accuracy, inapplicability to the Internet of Things environment, and high detection delay
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
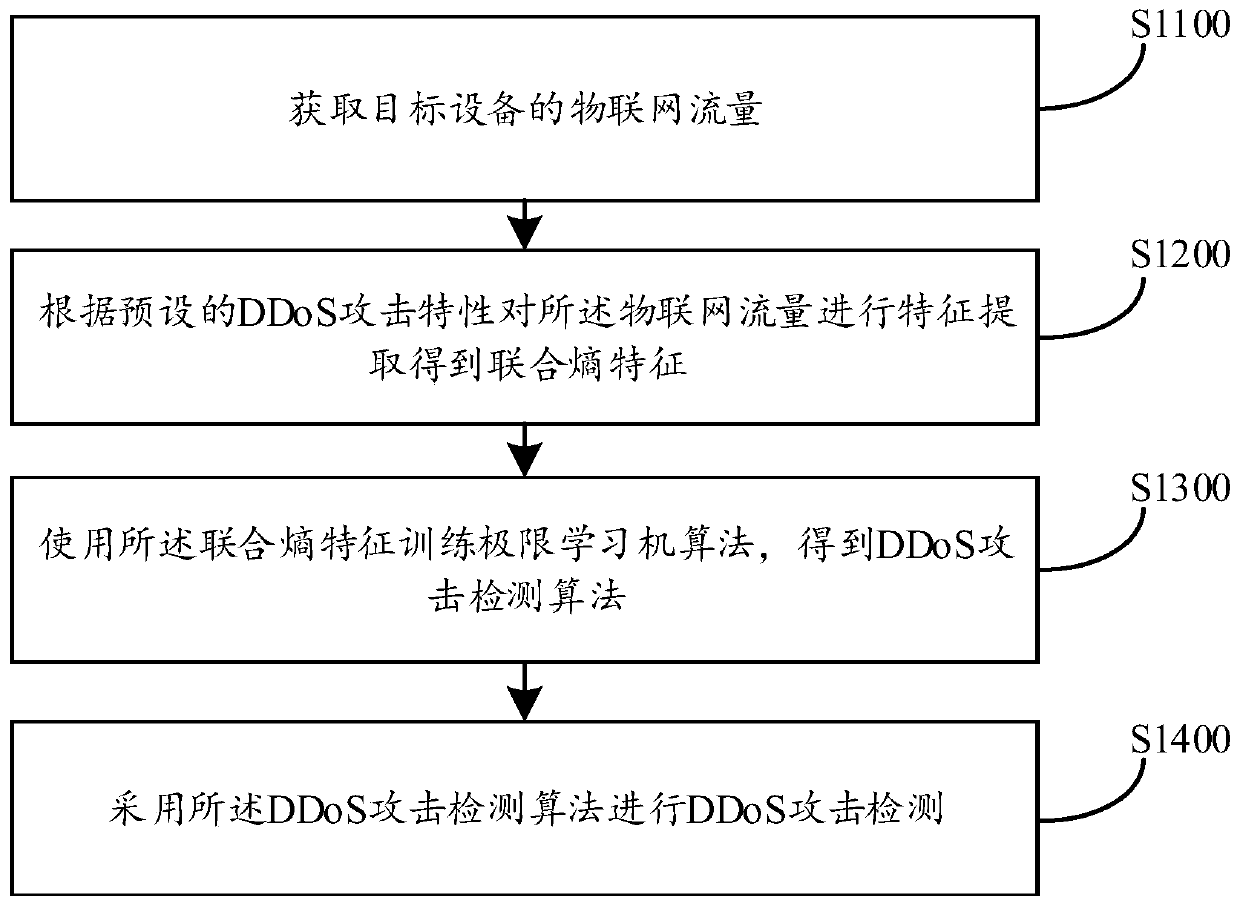
[0078] For details, please refer to figure 1 , figure 1 It is a schematic flowchart of the basic flow of the method for DDoS attack detection in this embodiment.
[0079] Such as figure 1 Shown, a kind of method for DDoS attack detection comprises the following steps:
[0080] S1100. Obtain the Internet of Things traffic of the target device;
[0081] Internet of Things traffic refers to the data traffic generated by the network services performed by the target device in the Internet of Things environment. In some embodiments, the target device is an intelligent electronic device connected to the Internet of Things, including but not limited to: smart phones, computers, tablets Computers, vehicle-mounted smart devices, etc., the target device will generate IoT traffic in the IoT environment. Taking the target device as a PC (Personal Computer, personal computer) terminal as an example, when the user enters the Internet of Things by using a PC terminal, the system can obtain...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com