Threat intelligence IOC credibility analysis method
An analysis method and reputation technology, applied in electrical components, transmission systems, etc., can solve the problems of inaccurate threat intelligence source data and lack of failure mechanism for threat intelligence, and achieve the effect of ensuring data failure mechanism
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0027] The present invention will be described in further detail below in conjunction with the examples, but the protection scope of the present invention is not limited thereto.
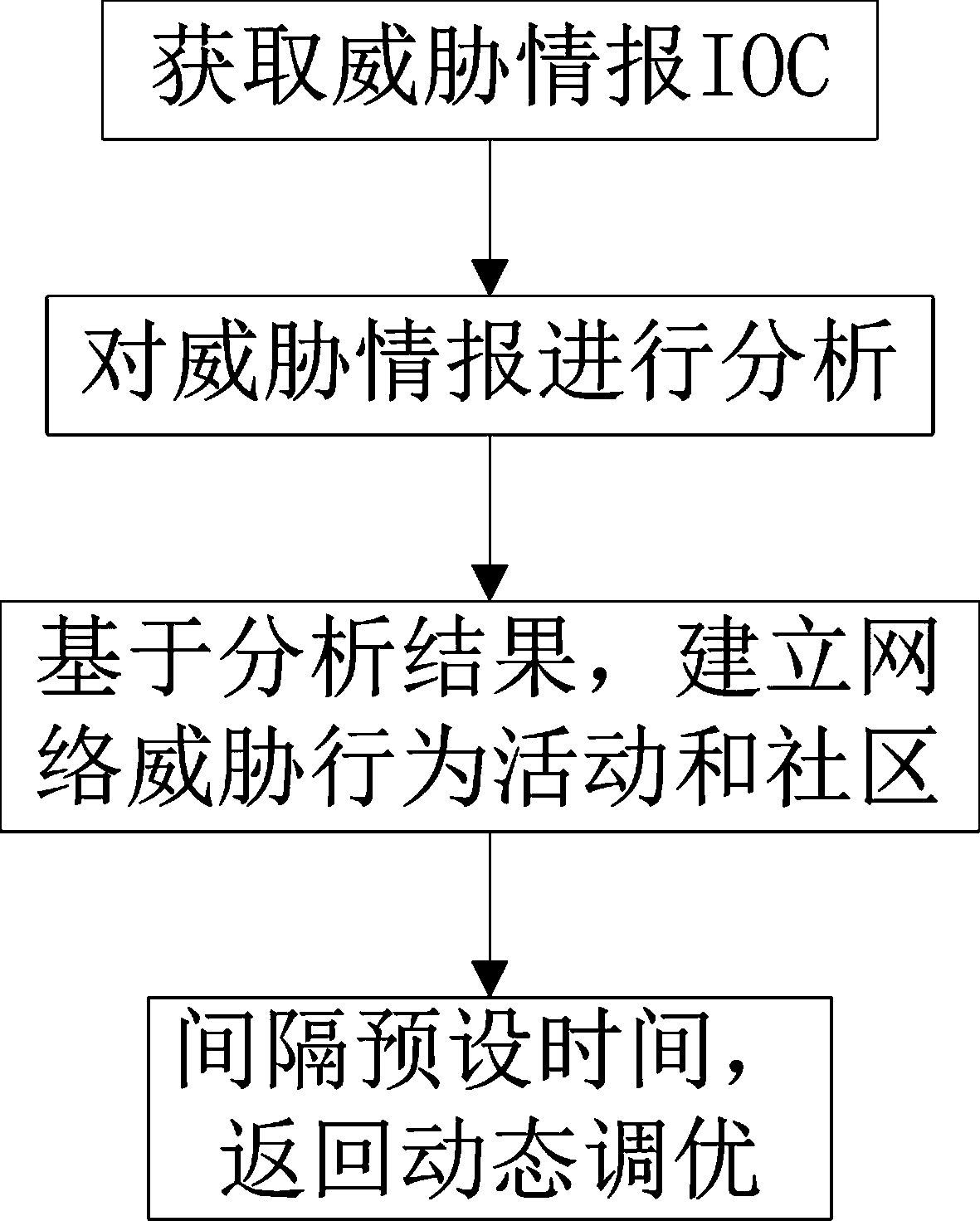
[0028] The invention relates to a threat intelligence IOC reputation analysis method, which achieves the purpose of having a reliable reputation evaluation system for threat intelligence IOCs in various channels, and dynamically adjusts the evaluation system to ensure an effective mechanism
[0029] In this invention, in fact, the IOC of threat intelligence collection mainly comes from three data sources: security vendor’s own equipment (including the company’s use of equipment to capture data in project practice), purchased security vendor data, and open source intelligence data. Among them, for third-party open source intelligence data sources, security vendor data cannot judge the data production process and data evaluation mechanism, and in the actual production process, due to technical, geograp...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com