Cluster alarm method and device, setting and storage medium
A cluster and detection technology, applied in the field of clusters, can solve problems such as inability to maintain clusters, high latency in cluster maintenance, and over-monitoring of clusters, so as to reduce the time for discovering and repairing operating failures, reduce the frequency of cluster downtime, and increase cluster downtime. effect of duration
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
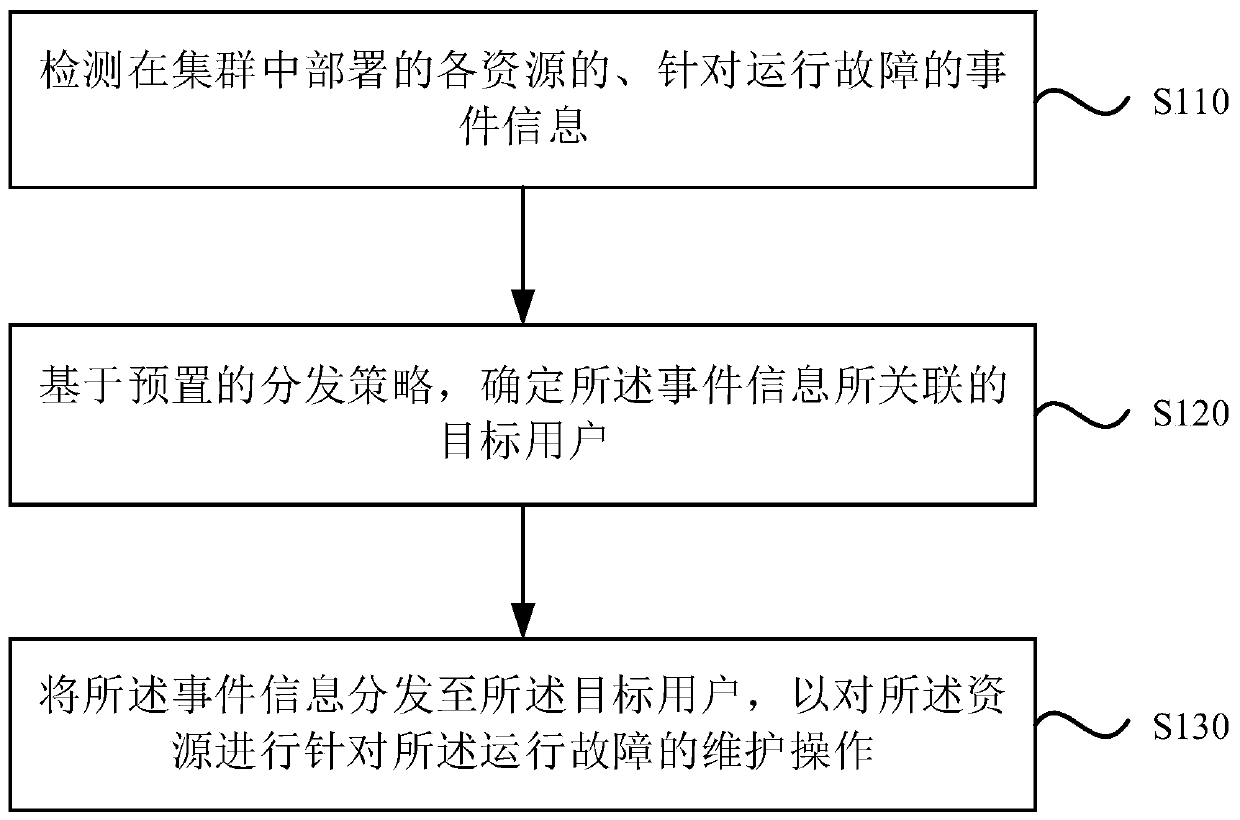
[0056] Figure 1A It is a flow chart of a cluster alarm method provided by Embodiment 1 of the present invention, Figure 1B It is a schematic structural diagram of a cluster alarm system provided by Embodiment 1 of the present invention. This embodiment is applicable to the situation of monitoring and alarming a cluster, and the method can be executed by an alarm device of the cluster. The alarm device of the cluster may be nodes (Nodes) in the cluster, and the nodes may be Internet of Things devices, computers, servers, mobile terminals, and the like. In this embodiment, a cluster alarm device is used as a server for detailed description, and the server may be an independent server or a cluster server.
[0057] refer to Figure 1A , the method specifically includes the following steps:
[0058] S110. Detect event information of each resource deployed in the cluster and aimed at operation failure.
[0059] In this embodiment, the resources of the cluster include hardware r...
Embodiment 2
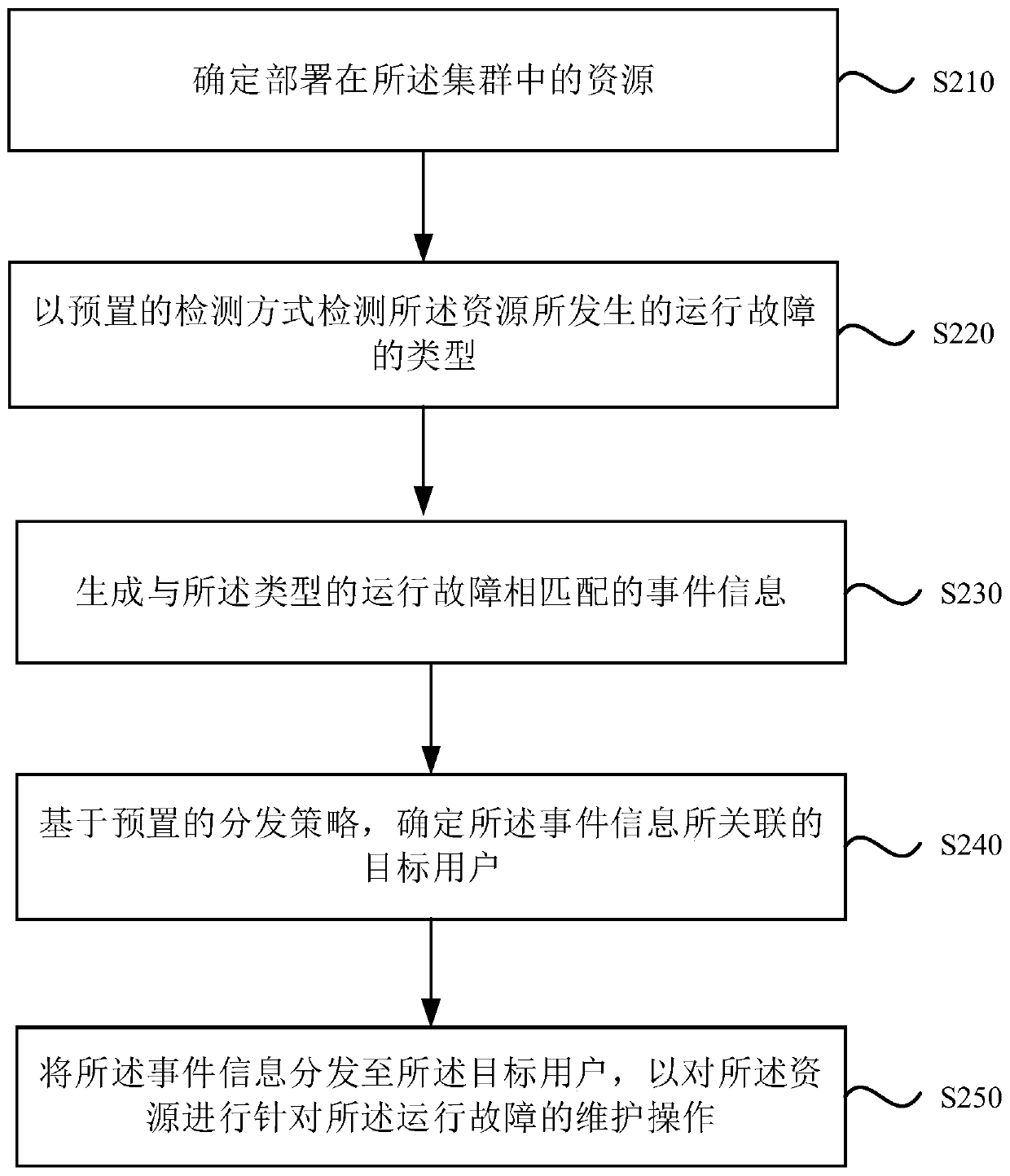
[0097] figure 2 It is a flow chart of a cluster alarm method provided by Embodiment 2 of the present invention.
[0098] This embodiment is further refined on the basis of the foregoing embodiments, and specifically, at least includes: a description of a detection method for an operation failure.
[0099] refer to figure 2, the method specifically includes the following steps:
[0100] S210. Determine resources deployed in the cluster.
[0101] In an embodiment, a cluster management tool may be used to detect the cluster. Exemplarily, when the cluster is built using Kubernetes, the resource interface exposed by the Kubernetes cluster can be used to monitor the cluster.
[0102] Specifically, the resource interface can be used to obtain information about the program deployed in the cluster and the environment information in which the program runs, and the environment information can include the running status of each resource in the cluster. For example, you can use the ...
Embodiment 3
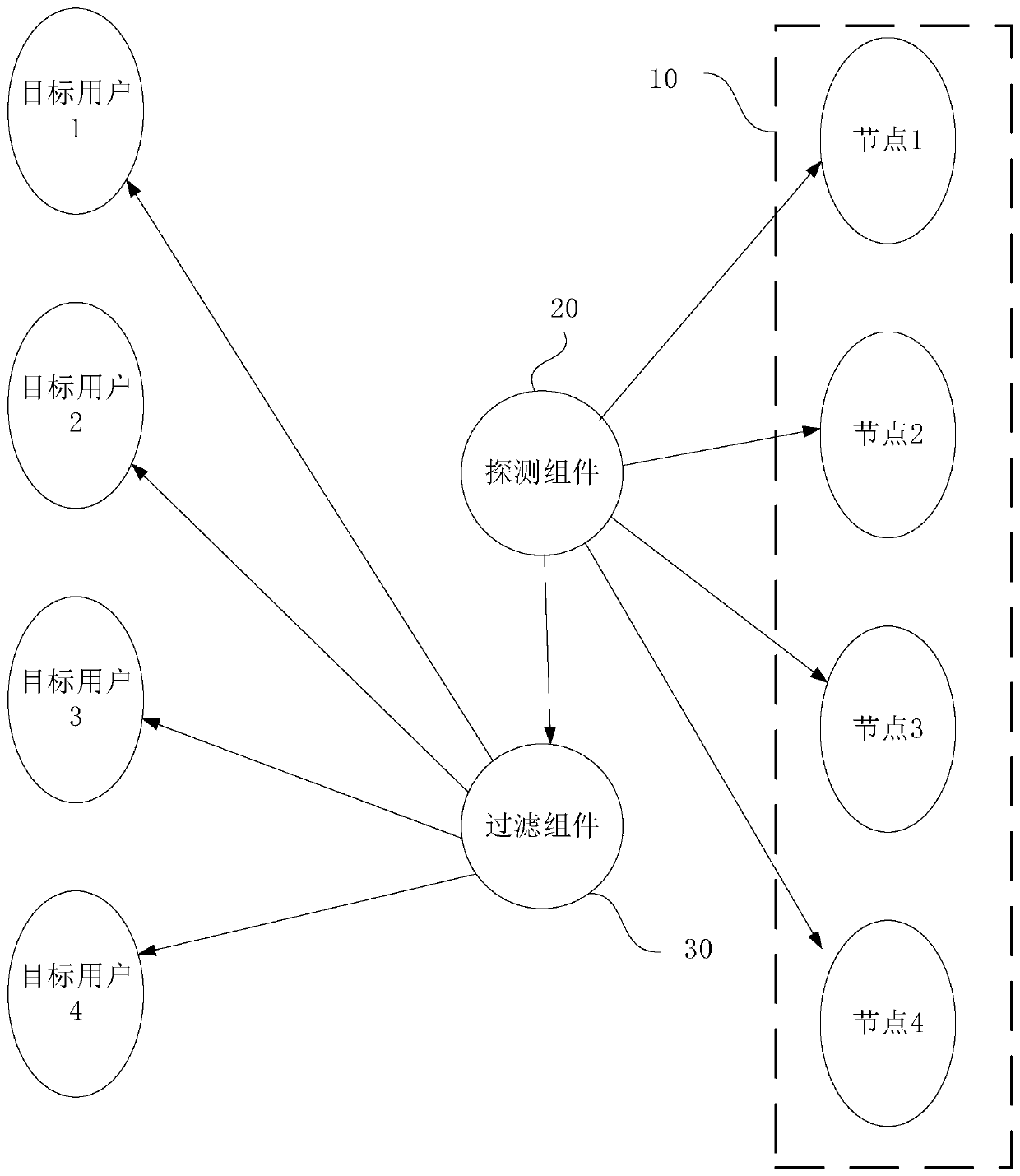
[0144] image 3 It is a schematic structural diagram of a cluster alarm device provided by Embodiment 3 of the present invention. This embodiment is applicable to the situation of monitoring and alarming a cluster, and the device can be integrated into an alarm device of the cluster. The alarm device of the cluster may be nodes (Nodes) in the cluster, and the nodes may be Internet of Things devices, computers, servers, mobile terminals, and the like. In this embodiment, a cluster alarm device is used as a server for detailed description, and the server may be an independent server or a cluster server.
[0145] refer to image 3 , the device specifically includes the following structures: an event information detection module 310 , a target user determination module 320 and a distribution module 330 .
[0146] An event information detection module 310, configured to detect event information for operation failures of each resource deployed in the cluster;
[0147] A target u...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com