Data security monitoring method and device, electronic equipment and readable medium
A security monitoring and data technology, applied in the computer field, can solve the problems of fine data mining analysis, poor retrospective analysis of historical network traffic data, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
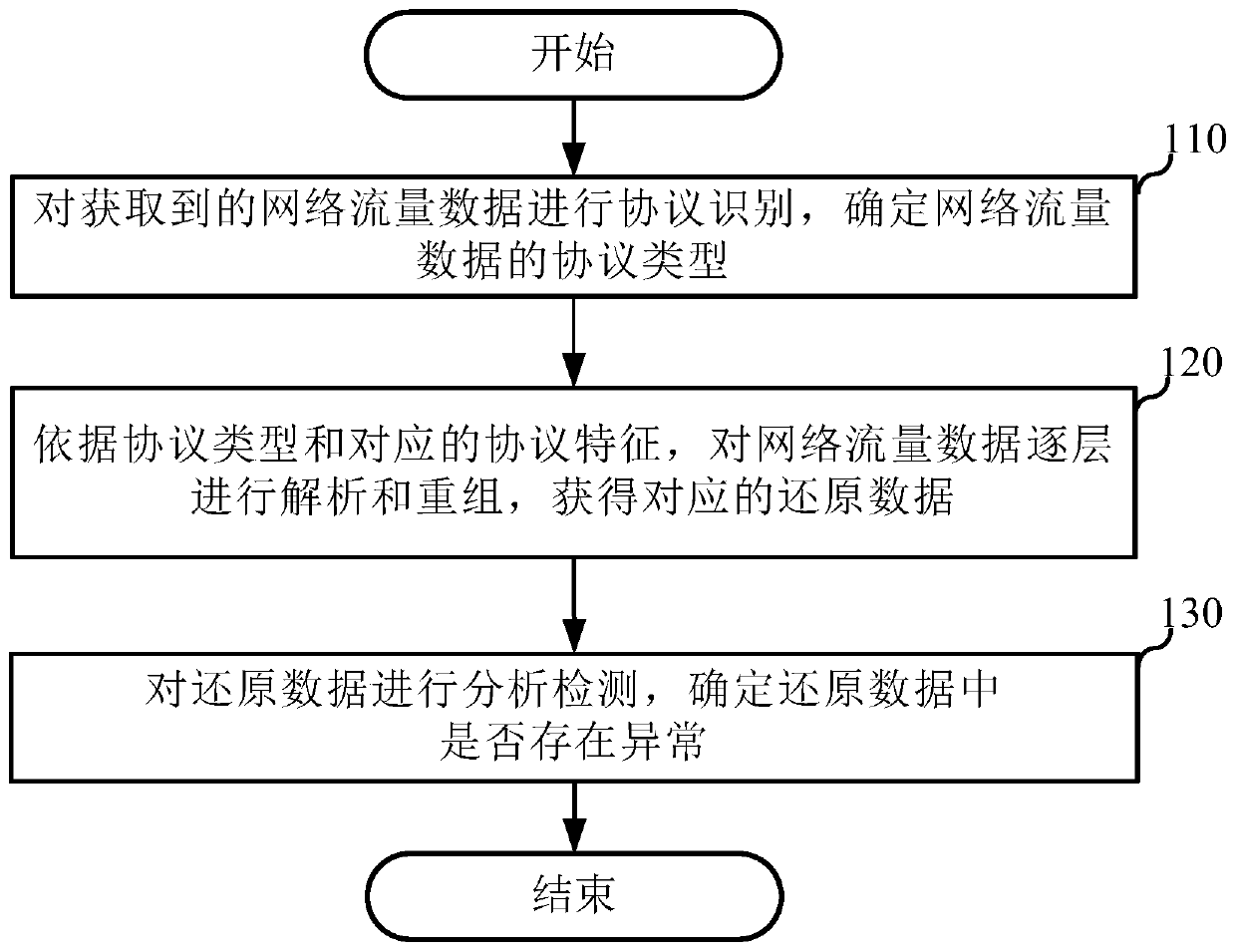
[0033] An embodiment of the present application provides a data security monitoring method, which can be applied to a data security monitoring device. Such as figure 1 shown, including:
[0034] Step 110: Perform protocol identification on the acquired network traffic data to determine the protocol type of the network traffic data.
[0035] Step 120: Analyze and reorganize the network traffic data layer by layer according to the protocol type and the corresponding protocol features to obtain the corresponding restored data.
[0036] For example, the restored data may be any one or several of various data records, text files, picture files and video files. The above description of the restored data is only an example, and the details can be set according to the actual situation. Other restored data that are not illustrated are also within the protection scope of the present application, and will not be repeated here.
[0037] In some specific implementations, the restored da...
Embodiment 2
[0149] Figure 7 This is a block diagram of a data security monitoring device provided by the embodiment of the present application. For the specific implementation of the device, please refer to the relevant description of the first embodiment, and the repetition will not be repeated. It is worth noting that the specific implementation of the device in this embodiment is not limited to the above embodiments, and other undescribed embodiments are also within the protection scope of the device.
[0150] Such as Figure 7 As shown, the data security monitoring device specifically includes: a protocol type determination module 701 is used to identify the protocol of the acquired network traffic data, and determine the protocol type of the network traffic data; a parsing and reorganization module 702 is used to base the protocol type and the corresponding The protocol feature is to analyze and reorganize the network traffic data layer by layer to obtain the corresponding restored...
Embodiment 3
[0157] An embodiment of the present application provides an electronic device. Figure 9 It is a structural diagram of an exemplary hardware architecture of an electronic device that can implement the data security monitoring method and device according to the embodiments of the present application.
[0158] Such as Figure 9 As shown, the electronic device 900 includes an input device 901 , an input interface 902 , a central processing unit 903 , a memory 904 , an output interface 905 , and an output device 906 . Wherein, the input interface 902, the central processing unit 903, the memory 904, and the output interface 905 are connected to each other through the bus 907, and the input device 901 and the output device 906 are respectively connected to the bus 907 through the input interface 902 and the output interface 905, and then connected to the electronic device 900 other component connections.
[0159] Specifically, the input device 901 receives external input informat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com