Alliance chain fragmentation method and device
A technology of alliances and nodes, applied in the blockchain field, can solve the problems of low efficiency of alliance chain sharding, achieve the effects of reducing time consumption, avoiding sharding, and improving accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
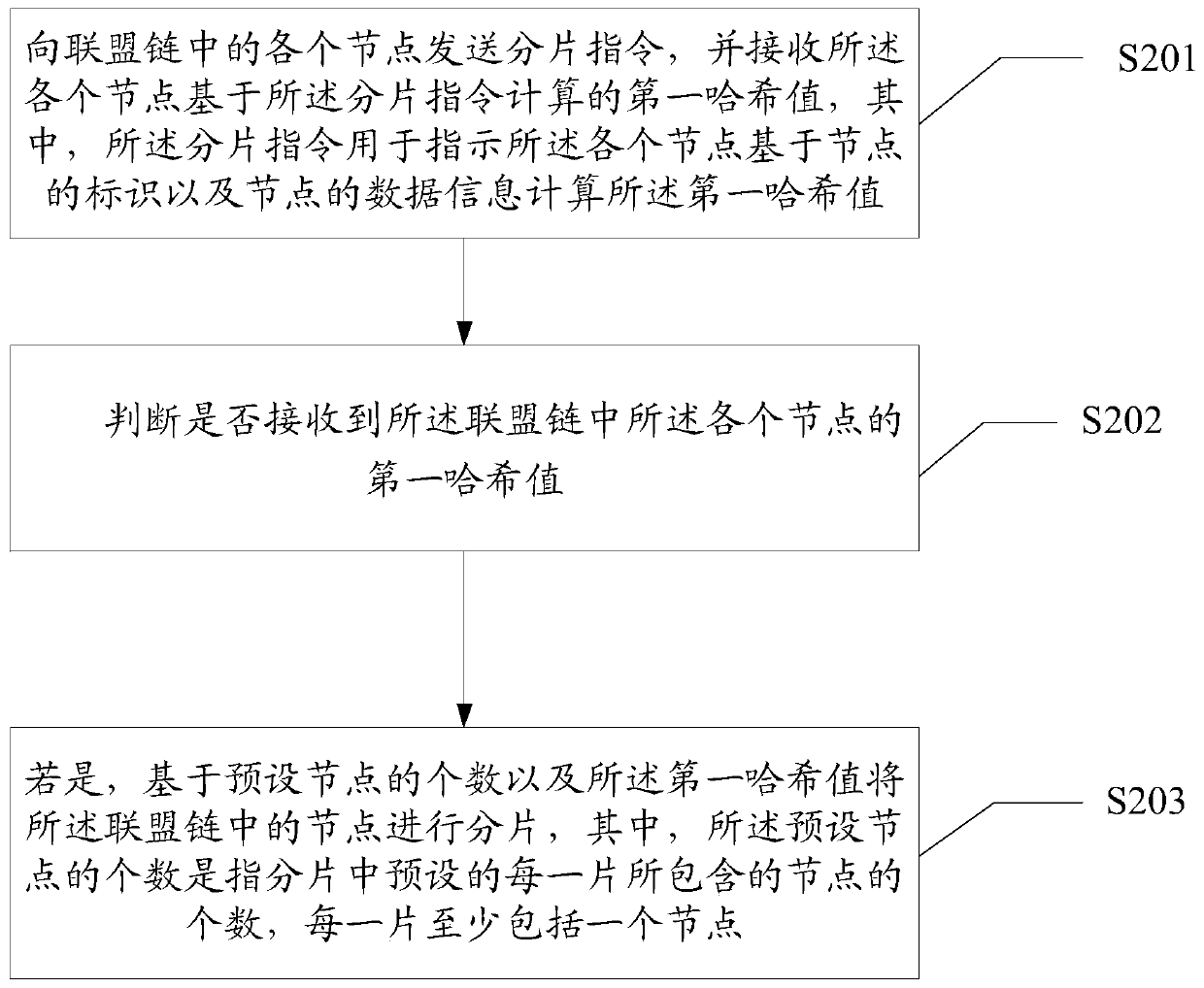
[0048] A method for sharding the consortium chain provided by the embodiment of the present application will be described in further detail below in conjunction with the accompanying drawings. The specific implementation of the method may include the following steps (the method flow is as follows: figure 2 shown):
[0049]Step 201, the server sends fragmentation instructions to each node in the consortium chain, and receives the first hash value calculated by each node based on the fragmentation instruction, wherein the fragmentation instruction is used to indicate that each node The first hash value is calculated based on the identifier of the node and the data information of the node.
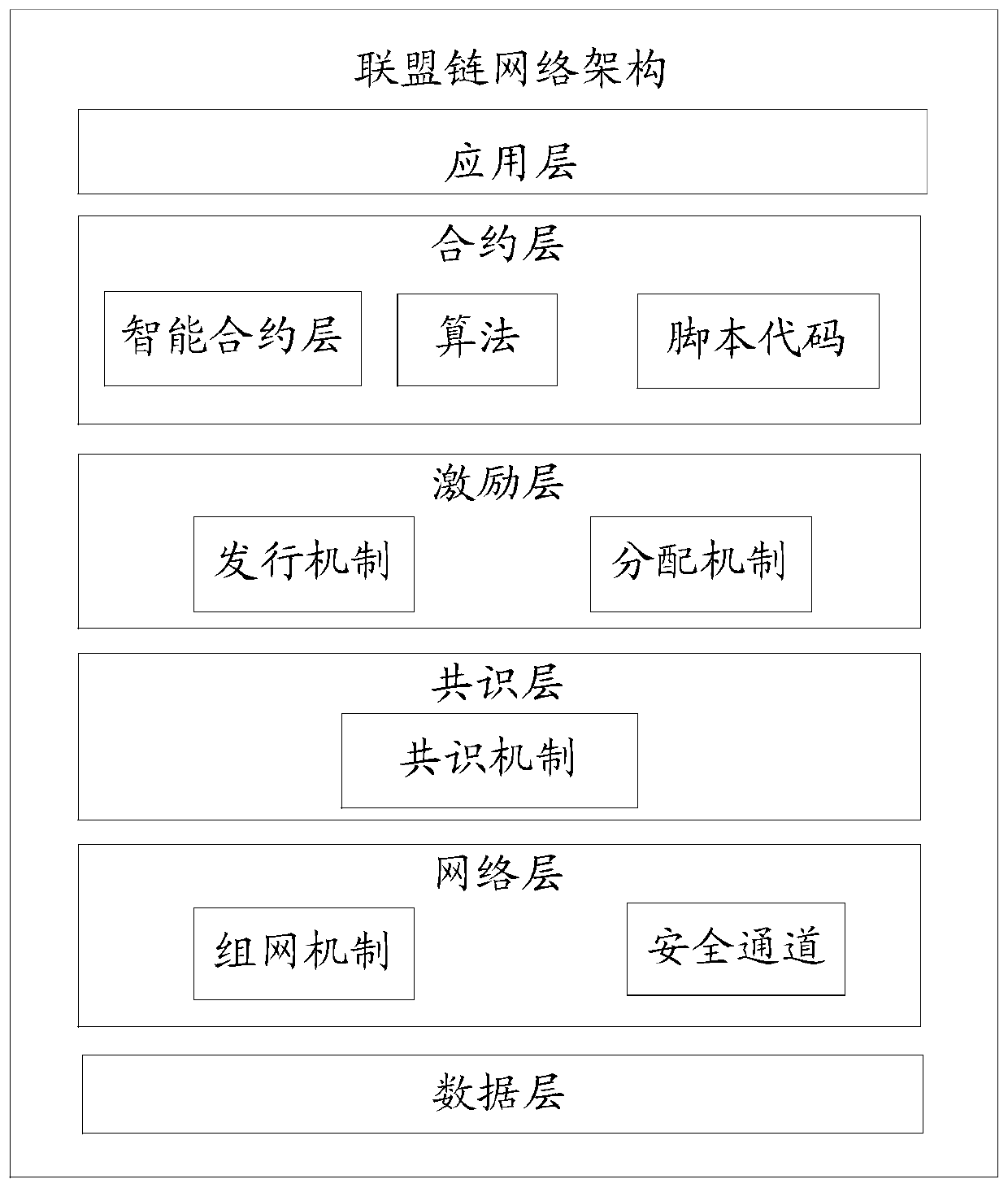
[0050] like image 3 As shown, the alliance chain network architecture includes application layer, contract layer, incentive layer, consensus layer, network layer and data layer. Among them, the application layer is mainly used to encapsulate various application scenarios and cases. For exa...
Embodiment 2
[0068] This application provides a device for alliance chain sharding, such as Figure 4 shown, the device includes:
[0069] The transceiver module 401 is configured to send fragmentation instructions to each node in the consortium chain, and receive the first hash value calculated by each node based on the fragmentation instruction, wherein the fragmentation instruction is used to indicate the Each node calculates the first hash value based on the identifier of the node and the data information of the node;
[0070] A judging module 402, configured to judge whether the first hash value of each node in the consortium chain is received;
[0071] The processing module 403 is configured to, if the first hash value of each node in the alliance chain is received, divide the nodes in the alliance chain based on the number of preset nodes and the first hash value A slice, wherein the preset number of nodes refers to the number of nodes contained in each slice preset in the slice, ...
Embodiment 3
[0083] This application provides a server, such as Figure 5 As shown, the server includes:
[0084] Memory 501, configured to store instructions executed by at least one processor;
[0085] The processor 502 is configured to execute instructions stored in the memory to execute the method described in Embodiment 1.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com