SM2-based two-party collaborative signature method and decryption method
A technology for signing messages and ciphertexts, which is applied to public keys for secure communications, encryption devices with shift registers/memory, and key distribution. and the effect of having a greater risk of safety in use
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
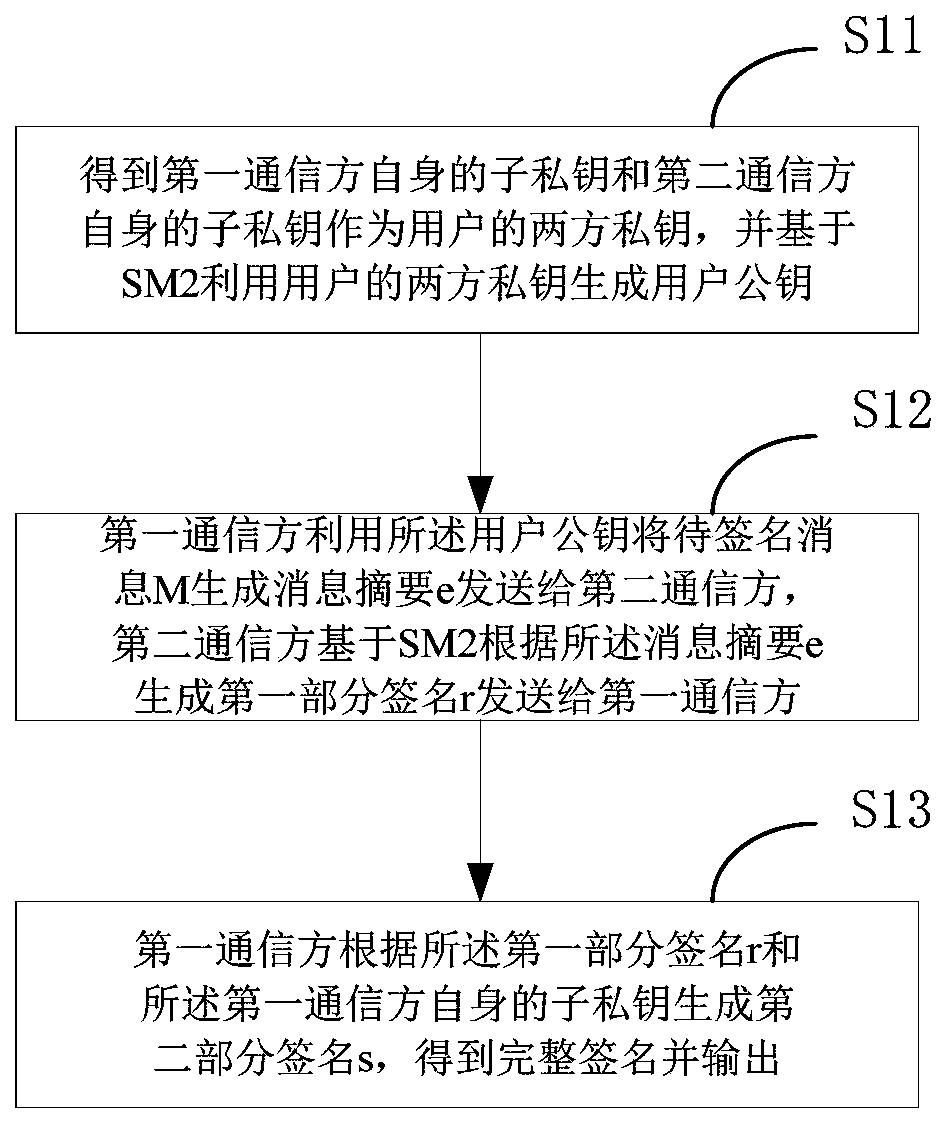
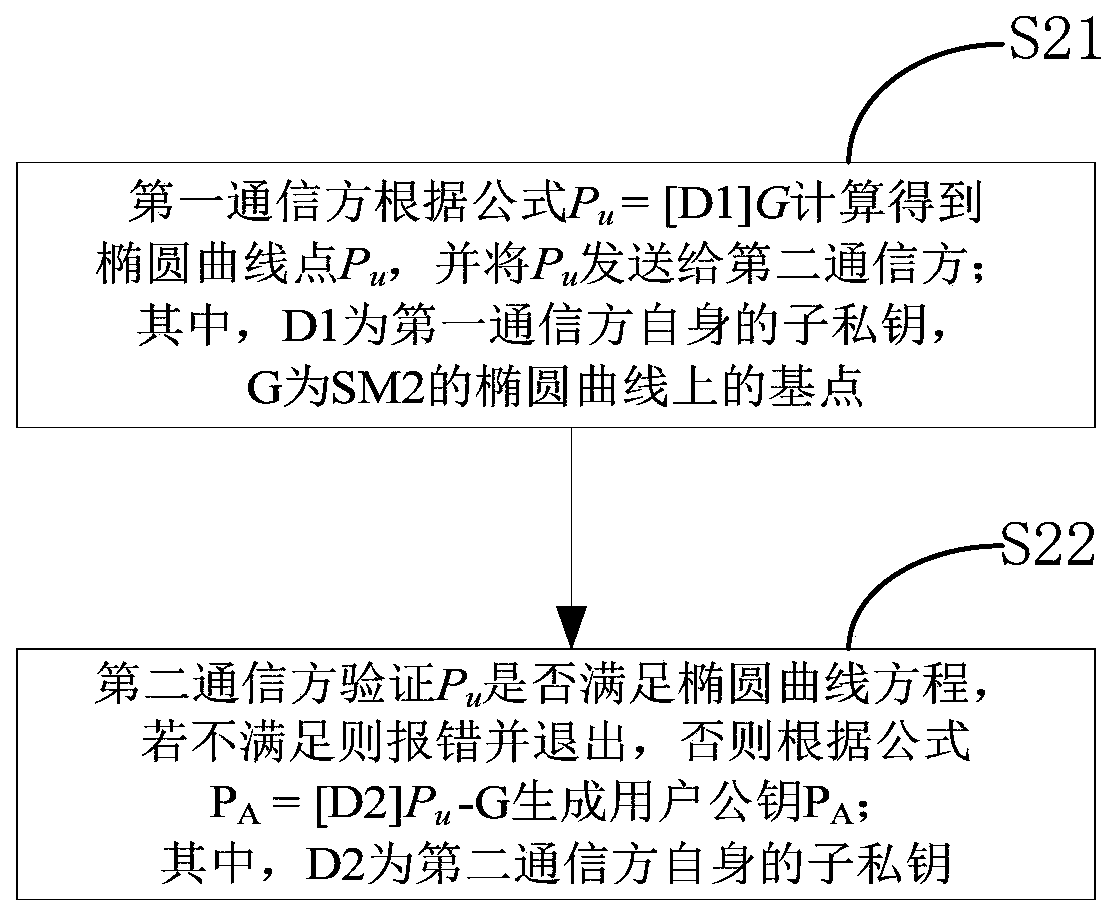
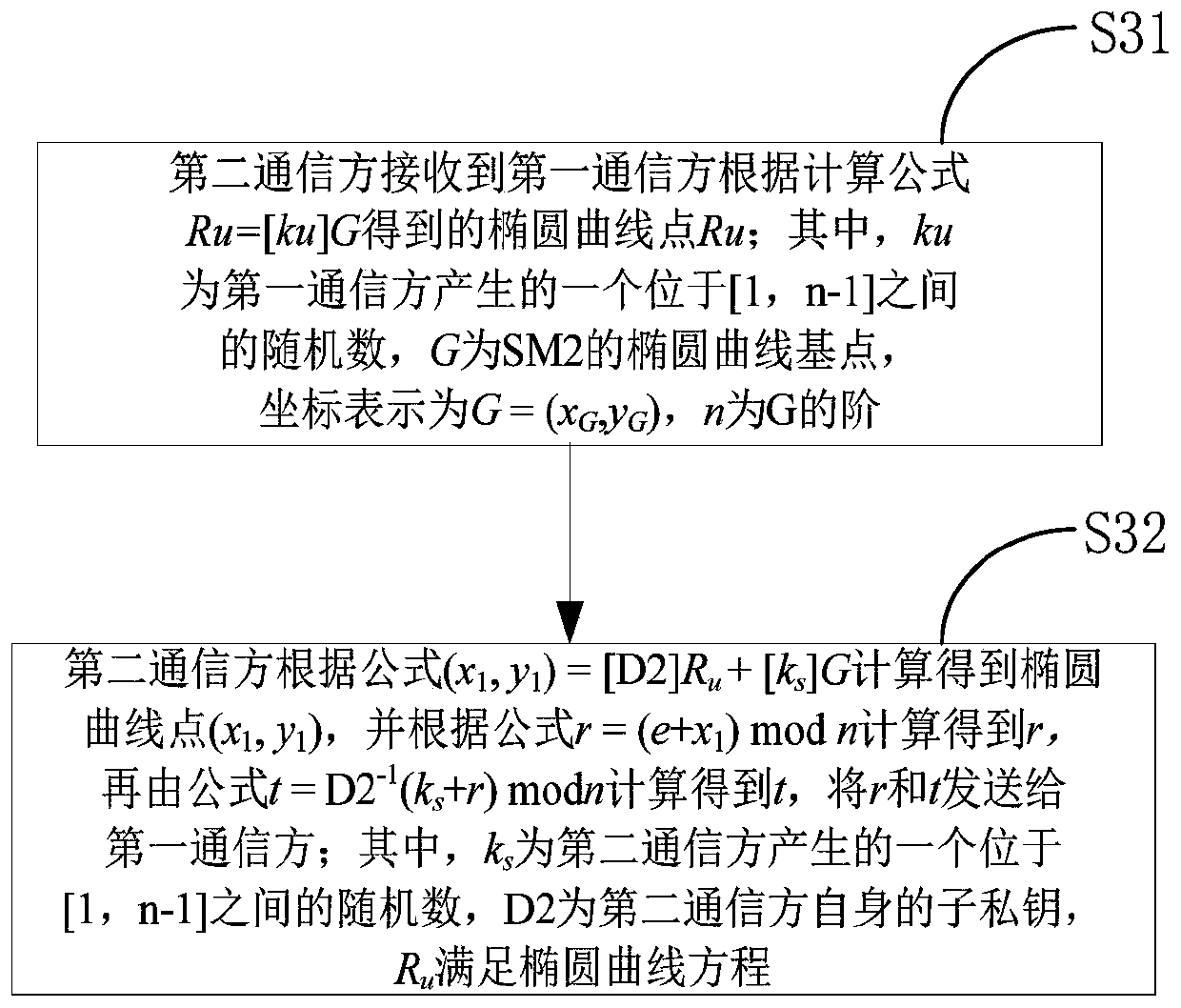
[0041] Preferred embodiments of the present invention will be described in detail below in conjunction with the accompanying drawings, wherein the accompanying drawings constitute a part of the application and together with the embodiments of the present invention are used to explain the principle of the present invention and are not intended to limit the scope of the present invention.
[0042] Abbreviations and key terms:
[0043] f p : A prime field containing p elements.
[0044] E(F p ): F p The set of all rational points (including the point O at infinity) of the upper elliptic curve E.
[0045] (p,a,b,G,n,h): The curve parameters of the SM2 algorithm, where p is a 256-bit prime number; a and b are F p elements in , used to define F p An elliptic curve E on the above; G is the base point, expressed by coordinates G=(x G ,y G ); n is the order of G; h is the cofactor.
[0046] h v ( ): a cryptographic hash function with a message digest length of v bits, and the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com