Portable authentication system and method
An authentication system and authentication method technology, applied in the field of portable authentication systems, can solve problems such as weak security barriers, high risk of password being stolen, and low security, so as to prevent illegal and malicious authentication behaviors, avoid confidential file leakage, and encrypt sex high effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
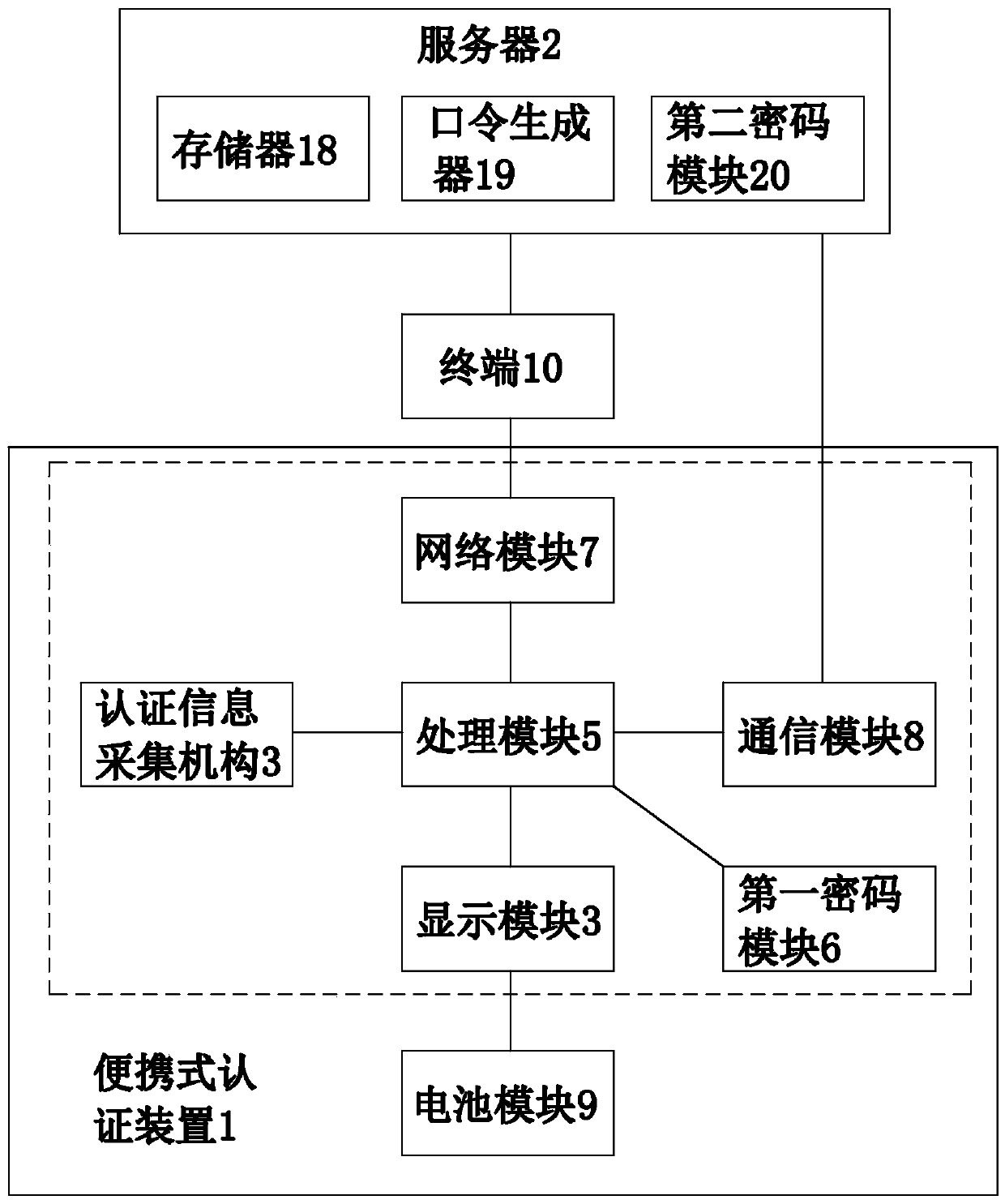
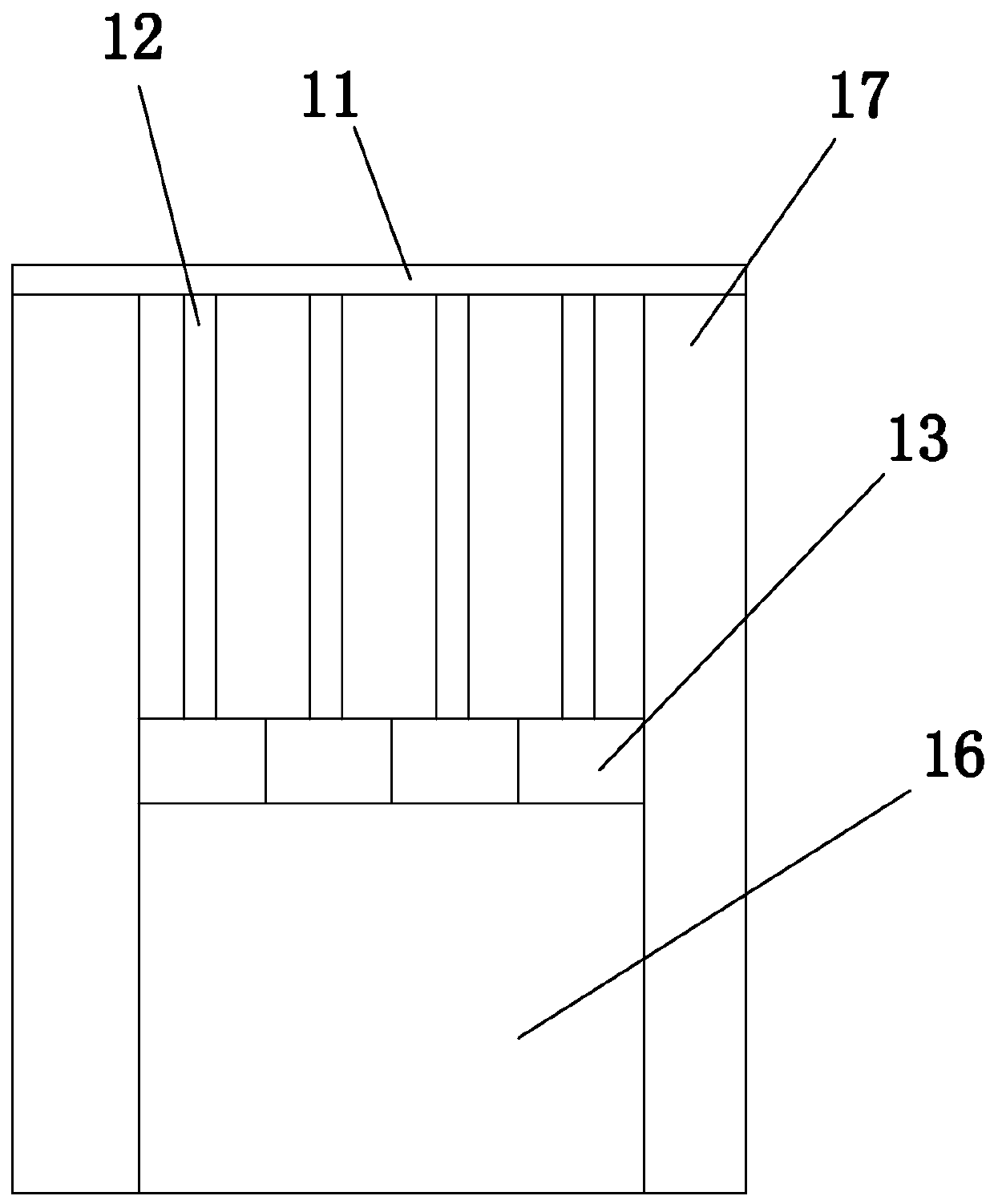
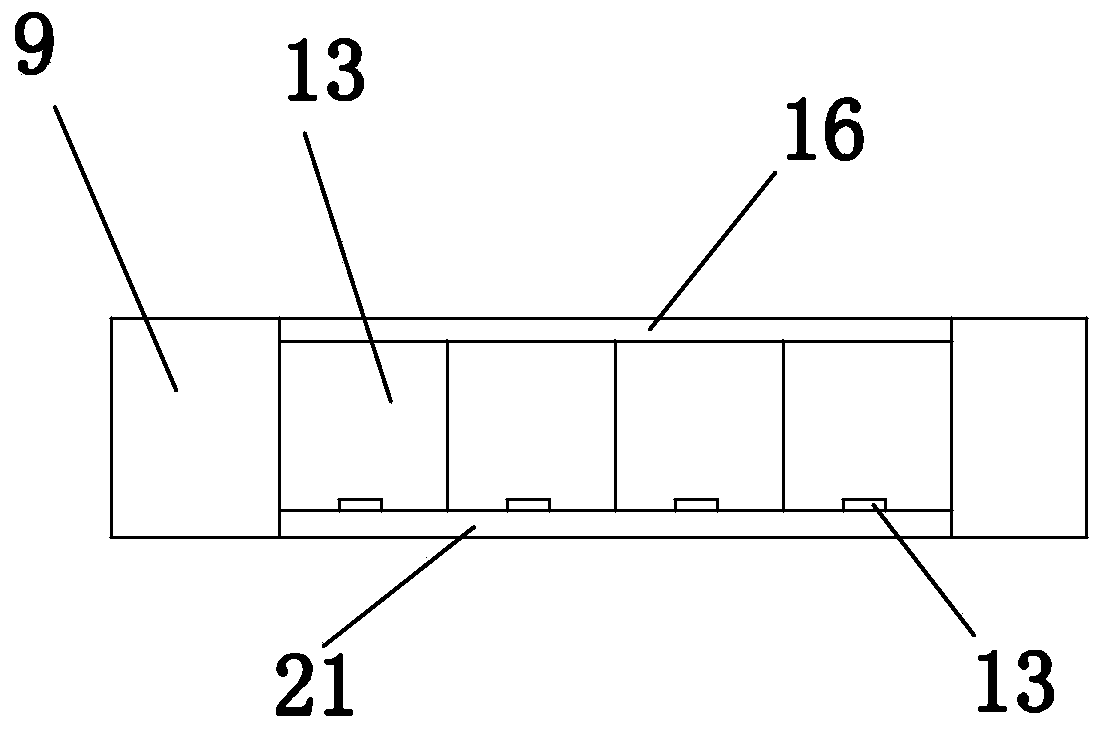
[0037] In this embodiment, a portable authentication system, such as figure 1As shown, it includes a portable authentication device 1 and a server 2, the portable authentication device includes an authentication information collection mechanism 3, a display module 4, a processing module 5, a first password module 6, a network module 7, a communication module 8 and a battery module 9, and the processing module Respectively connected to the authentication information collection mechanism, the display module, the first password module, the network module and the communication module, the portable authentication device is connected to the terminal 10 that will access the server through the network module, and obtains network services through the terminal, and the portable authentication device communicates with the terminal 10 through the communication module Server communication. The network module is a USB interface, the terminal is a PC, the USB interface of the portable authen...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com