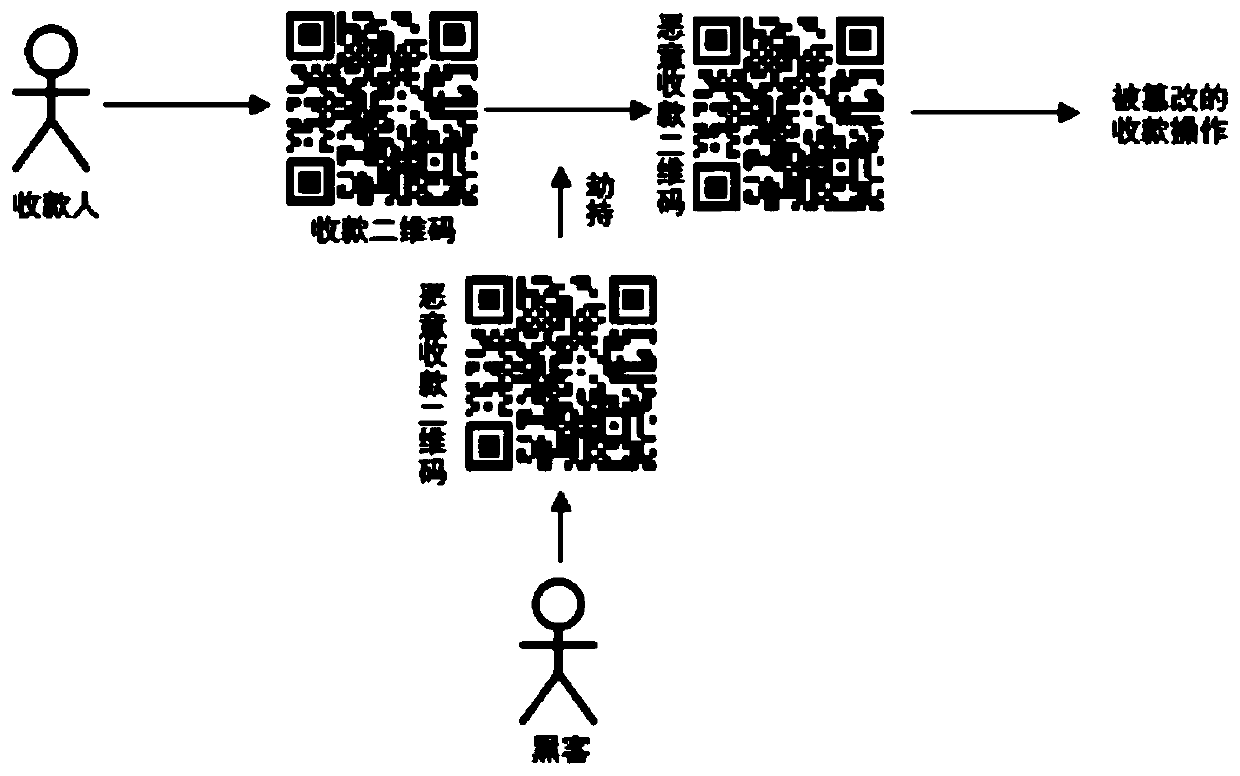
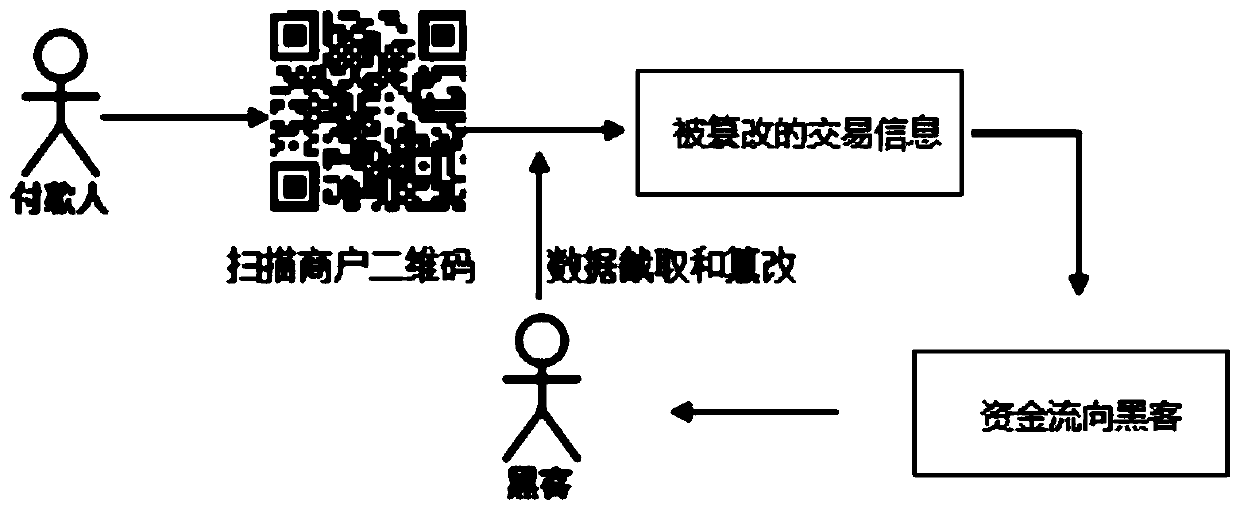
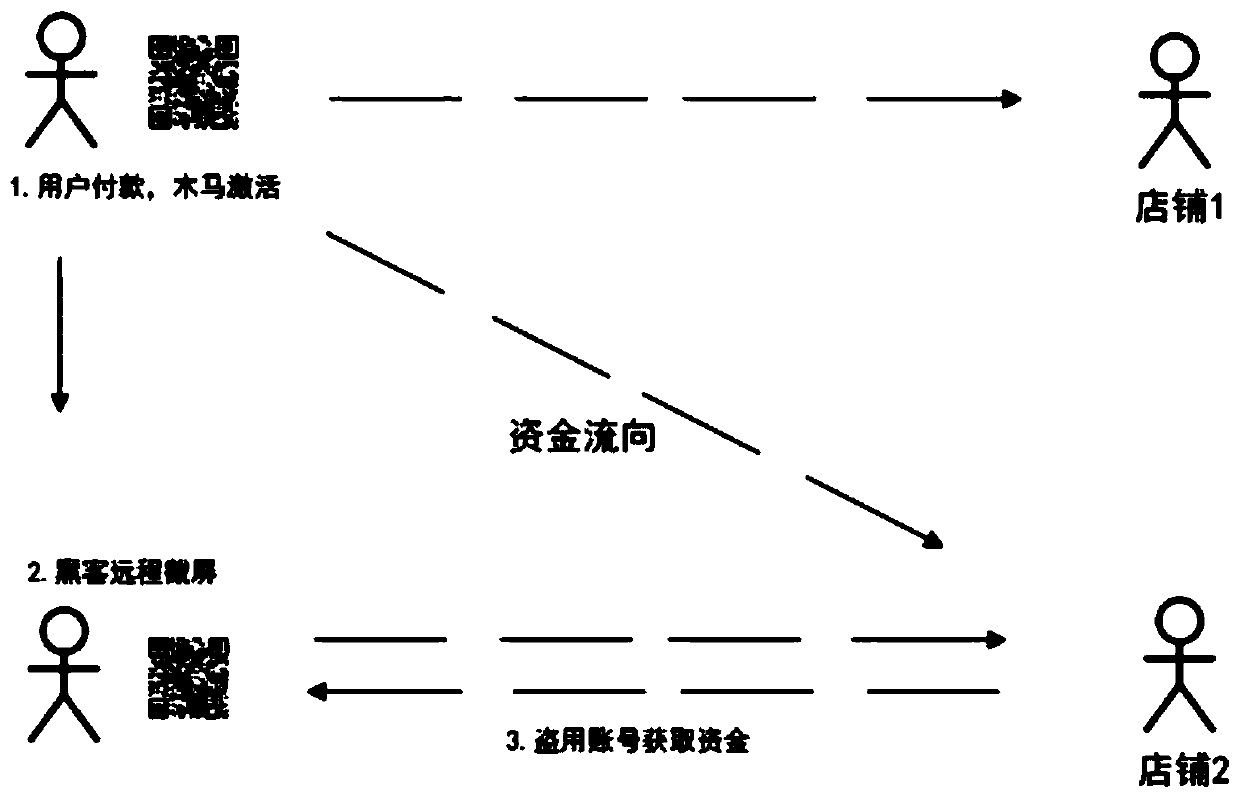
Commercial mobile operating system information protection method based on cloud encryption service
A mobile operating system and encryption service technology, applied in the field of commercial mobile operating system information protection, can solve the problems of application background server information fraud, APP application end injection and Trojan horse, network transmission information tampering and stealing, etc., to avoid being repackaged, The effect of convenient secondary development
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0054] Such as Figure 4 , 5 , a security solution for location services in the Android system
[0055] 1) Implementation of Android native location service and fraud principle
[0056] a) Location service implementation
[0057] Android positioning service integrates GPS positioning, mobile communication, navigation and other technologies to provide comprehensive application services related to spatial location. In recent years, location-based services have developed more rapidly, involving all aspects of business, medical care, work and life, and providing users with a series of services such as positioning, tracking and warning of sensitive areas.
[0058] b) Java framework development interface:
[0059] The Android platform supports APIs that provide location services, and the LocationManager and LocationProviders objects are mainly used in the development process.
[0060] -LocationManager:
[0061] It is used to obtain the current location, track the movement rout...
Embodiment 2
[0118] Embodiment 2: Safe Interactive Interface
[0119] There are various production and management systems in enterprise users. In the process of evolving to the mobile terminal, facing the security threats of the open network environment, there is no comprehensive solution. Through the secure interaction interface provided by the commercial mobile operating system information security protection method based on cloud encryption services, the APP can access its own information system through the secure interface, thereby realizing a one-stop mobile terminal security solution without spending huge sums of money to process mobile terminal information security interaction scheme. The enterprise-level security interaction interface provides a standardized information interface for enterprises, allowing the enterprise's mobile applications (APP) to realize safe and fraud-free information interaction through the security interaction interface.
[0120] The interaction process of ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com