Information protection method and device
An information protection and short message technology, applied in the field of information security, can solve problems such as re-encryption, abrupt private information, and difficulty in encryption algorithm key management, so as to ensure absolute security and reduce system overhead
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
no. 2 example
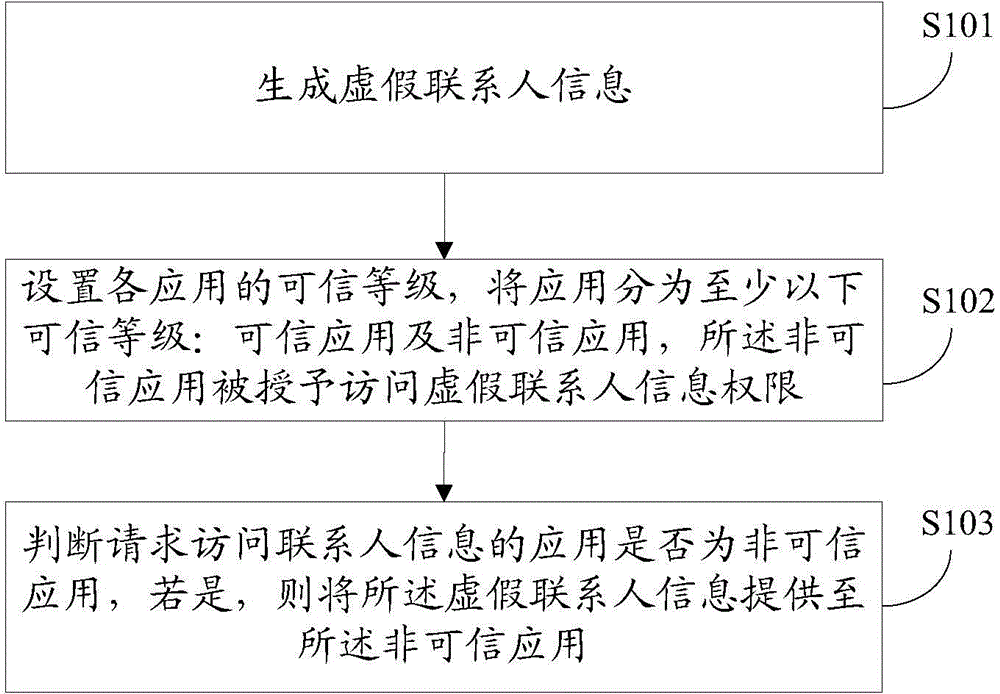
[0068] The second embodiment of the present invention is an information protection method. The method described in this embodiment is roughly the same as that in the first embodiment. The difference is that in step S101 of this embodiment, the trust level of each application set also includes: danger application, the dangerous application has not been granted any access permissions.
[0069] The method described in this embodiment also includes in step S103:
[0070] Determine whether the application requesting access to contact information is a dangerous application, and if so, refuse to provide any information for the dangerous application.
no. 3 example
[0071] The third embodiment of the present invention corresponds to the first embodiment or the second embodiment. This embodiment introduces an information protection device, such as Figure 4 shown, including the following components:
[0072] A generating module 100, configured to generate false contact information.
[0073] The setting module 200 is used to set the trust level of each application, and classify the applications into at least the following trust levels: trusted applications and untrusted applications, and the untrusted applications are granted the right to access false contact information.
[0074] The processing module 300 is configured to determine whether the application requesting to access the contact information is an untrusted application, and if so, provide the false contact information to the untrusted application.
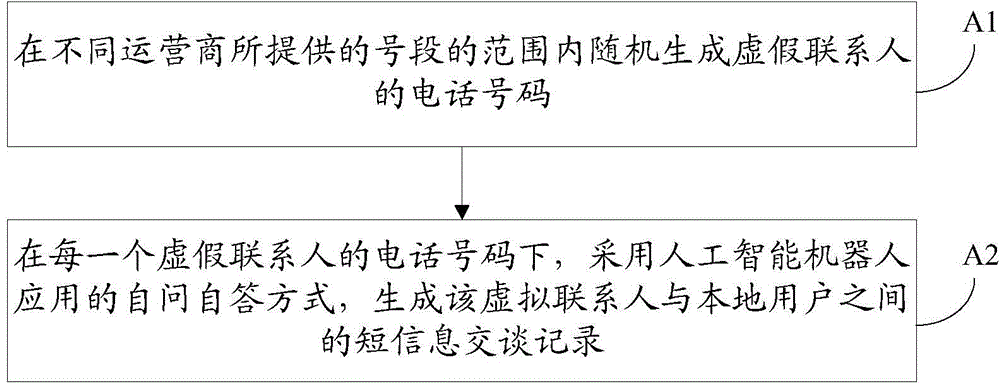
[0075] Specifically, taking the false contact information as the name of the false contact and the corresponding short message chat r...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com