Data access control method and system based on mimicry defense
A technology of data access control and data access, which is applied in the field of network security, can solve the problems that the security cannot be greatly improved, and the stability of the system is damaged, so as to improve robustness and security, improve stability and security, and scalability strong effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0053] A data access control method and system based on mimic defense in this scheme will be further described and explained below in conjunction with the accompanying drawings.
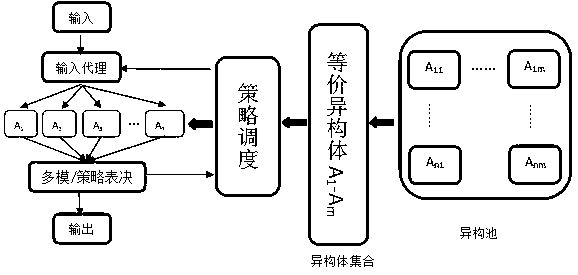
[0054] attached figure 1 It is a typical dynamic heterogeneous redundant structure diagram of the mimic defense system, as shown in the attached figure 1 As shown, the basic principle of mimic defense is: when there is a message input, it is transmitted to each heterogeneous executive in the heterogeneous pool through the input agent, and all heterogeneous executives process the message and transmit the result to the multi-mode arbitration module. If the processing results of heterogeneous executives are consistent, they will output. If they are not consistent, it can identify the abnormal output message of a certain heterogeneous executive, and then realize the security defense of the system.
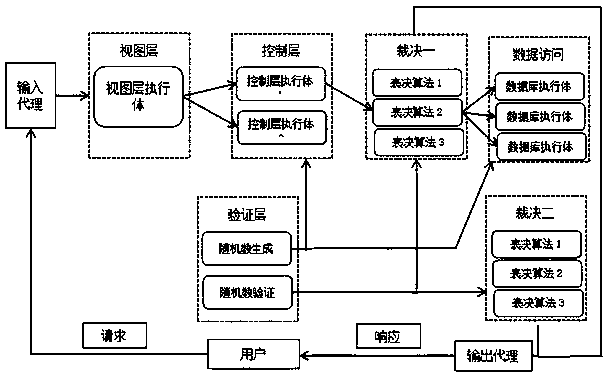
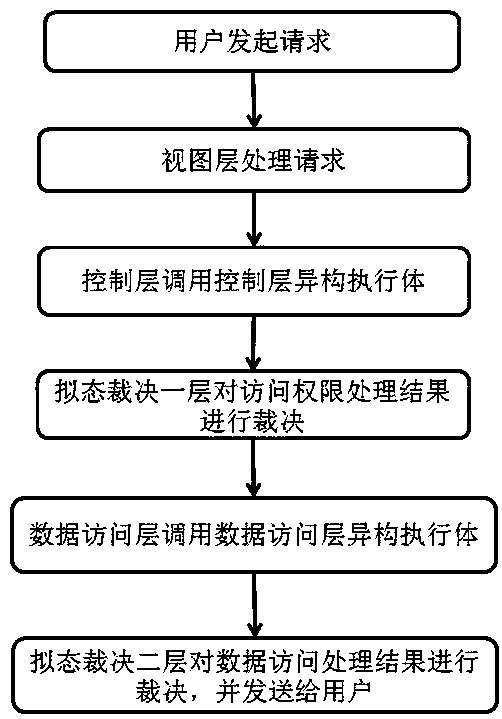
[0055] as attached figure 2 As shown, a data access control system based on mimicry defense includes: v...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com