Risk control method and device, electronic equipment and storage medium
A risk control and risk control technology, applied in the information field, can solve problems such as payment account leakage, electronic payment being stolen, etc., and achieve the effect of ensuring security
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
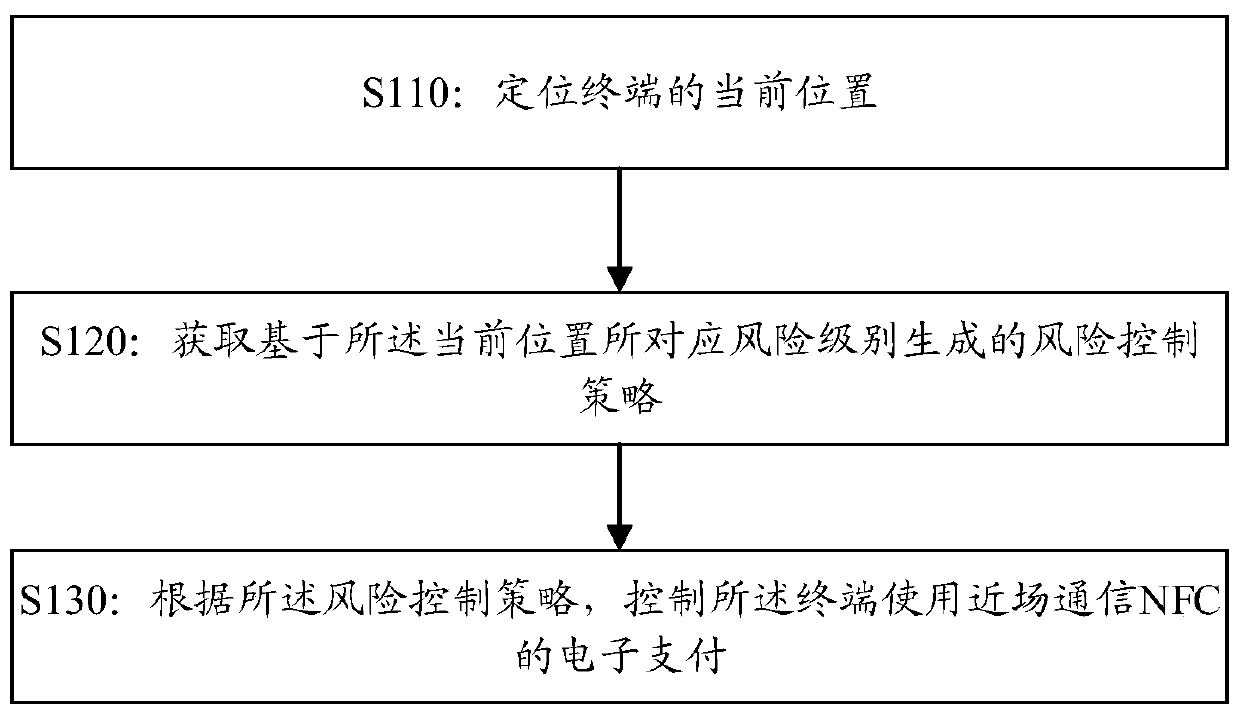
[0188] Figure 6 Shown is a terminal device that performs NFC-based electronic payment through a POS machine or a gate; the mobile terminal interacts with the POS machine or gate for NFC payment information, initiates payment and confirms the payment, and the POS machine and the gate complete the payment information interaction Afterwards, the POS machine or gate will trigger the payment platform (for example, the banking system or various online payment platforms) to make payment to the corresponding business platform, and complete the electronic payment process. Taking bus payment as an example, mobile terminals use mobile phones to make electronic payments based on NFC. After the POS machine or gate machine completes the payment, it will post the corresponding amount in the bus stored-value card to the bus financial system, or trigger Alipay or WeChat, etc. The third-party payment platform will post the corresponding amount to the bus financial system to complete the electr...
example 2
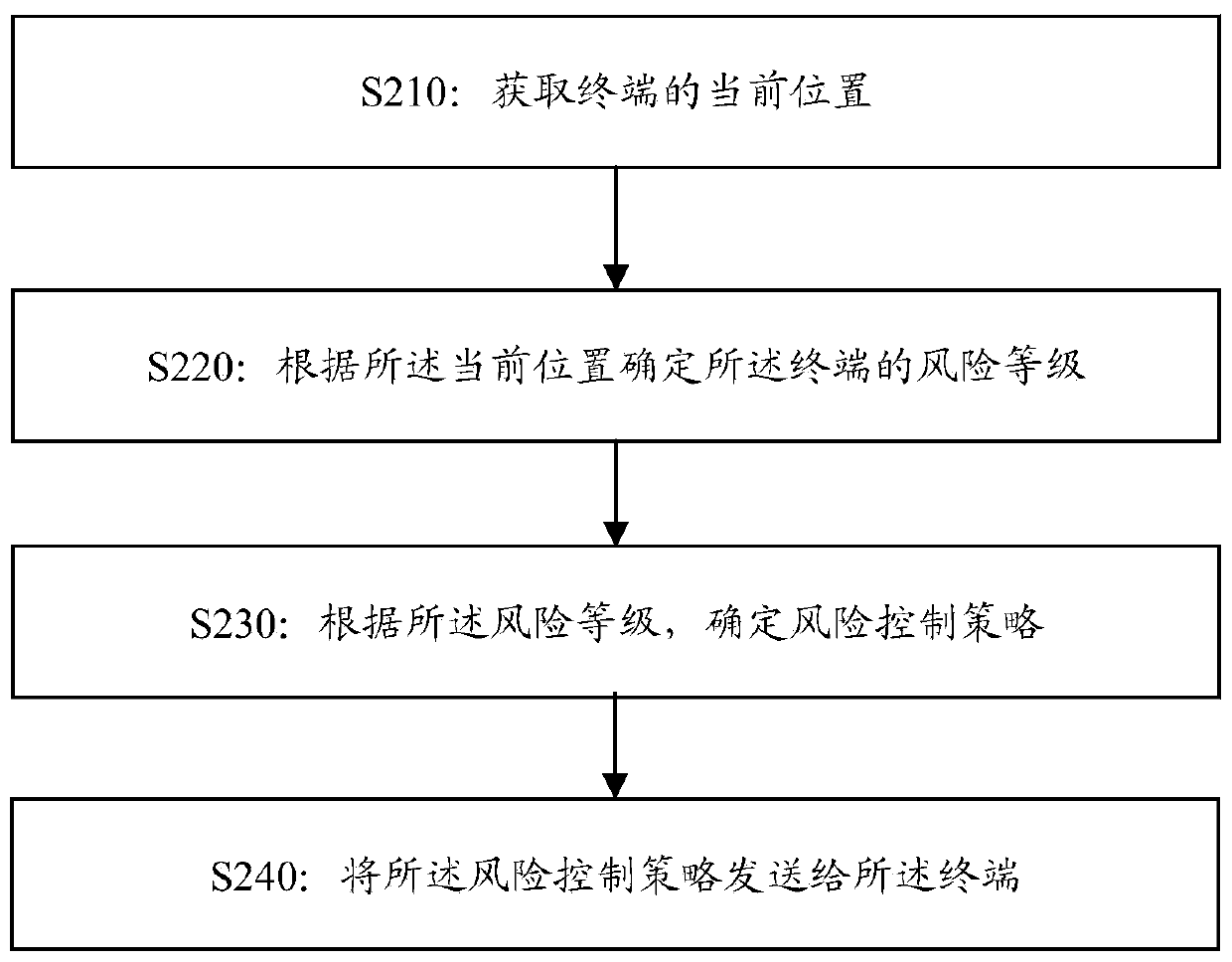
[0202] This example provides a risk control method, which can be applied to the risk control system provided in Example 1. Including but not limited to the following steps:
[0203] The location information module obtains and stores terminal location information in real time;
[0204] The main control module collects location information according to requirements;
[0205] The main control module processes the position information, and judges the positioning state S in the position information, if Mark the terminal as invalid for positioning, otherwise it is valid; for example, Count(S all ) times the positioning of the current position; through processing such as screening of outliers, it is determined that the effective positioning has Count(S invalid ), calculate Count(S invalid ) and Count(S all ), if the ratio is less than or equal to the effective ratio, it may be considered that the current positioning is invalid, and the next round of positioning needs to be init...
example 3
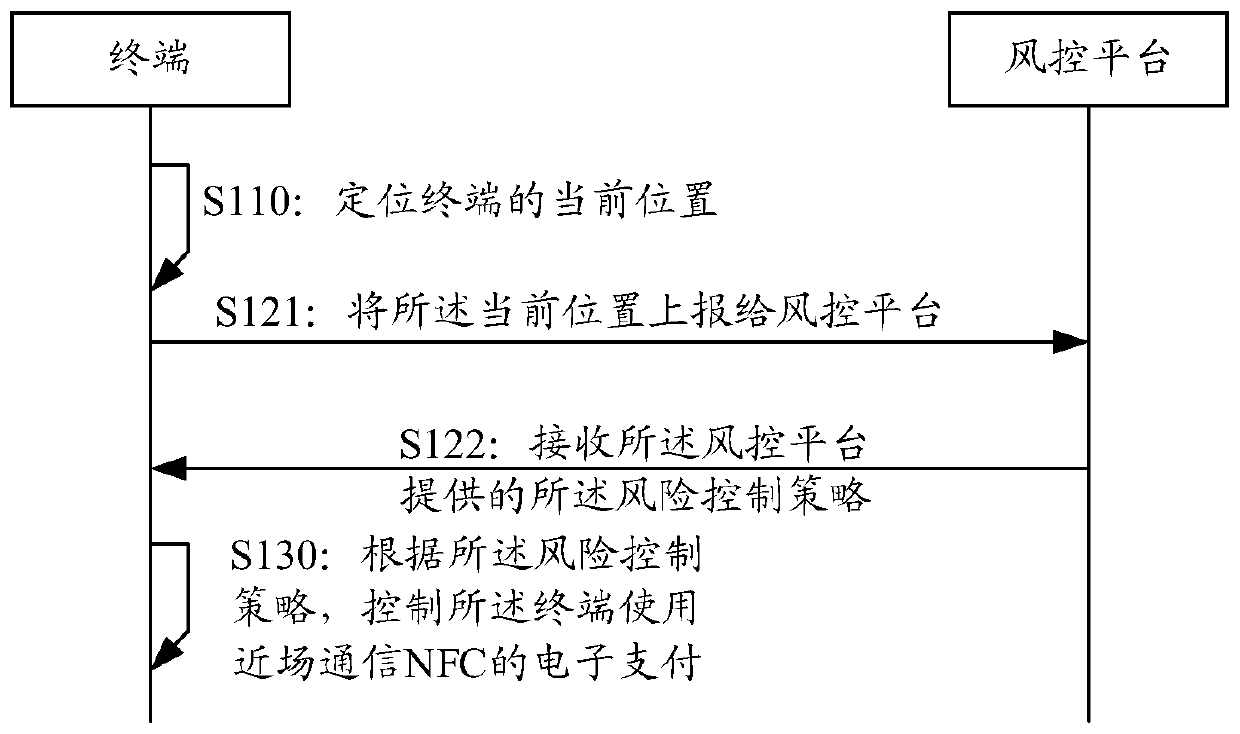
[0224] This example provides a method of risk control, such as Figure 8 shown, including:
[0225] 1: The location information module of the terminal, which can obtain the location information of the terminal in real time;
[0226] 2: The terminal uses the interaction between the main control module and the location information module to realize location information collection;
[0227] 3: The terminal performs preliminary processing of location information, for example, judging whether the current location information is valid, that is, judging whether the current location can be accurately indicated;
[0228] 4: The main control module of the terminal sends the effective location information to the risk control platform of the risk control platform;
[0229] 5: The risk control platform of the risk control platform calculates the location information and obtains the device fingerprint of the mobile phone;
[0230] 6: Terminal risk calculation (for example, determine the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com