Network system, attack detection method and device and electronic equipment
An attack detection and network system technology, applied in the field of network security, can solve problems such as network paralysis and high pressure of controller data processing, and achieve the effect of reducing the pressure of centralized processing, improving the strength of anti-attack, and reducing the possibility of being compromised
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
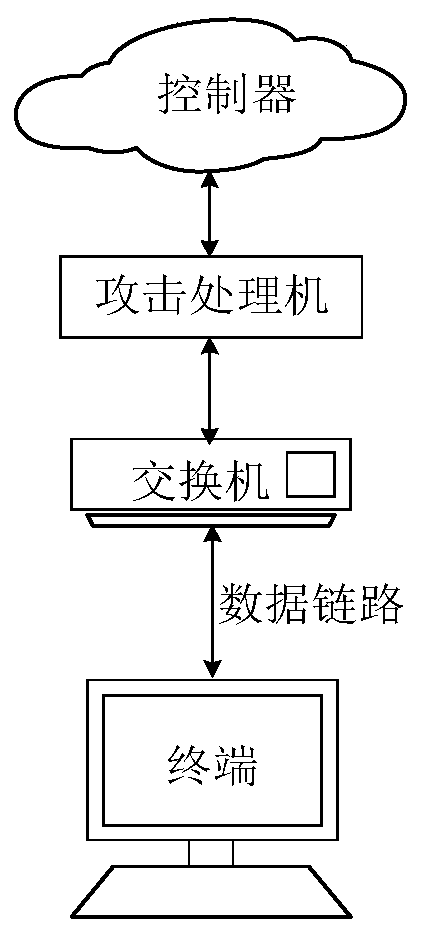
[0065] Such as image 3 As shown, it is a schematic structural diagram of a network system provided by Embodiment 1 of the present invention. The network system is suitable for an SDN network to deal with DDos attacks, and specifically involves a plurality of terminals 4 , a switch 1 , an attack processor 2 and a controller 3 .
[0066] Among them, the multiple terminals 4 may be mobile phones, computers, tablets and other smart devices capable of network data transmission; in addition, the terminals 4 also include normal business terminals and puppet terminals controlled by DDoS attack initiators. The terminal 4 may also be a sender / receiver / sender of abnormal traffic carried by the SDN network. The terminal 4 can send service flows to the SDN network or receive service flows sent by other devices from the network. Among them, the business traffic includes normal business access traffic and DDoS attack traffic sent after the terminal is compromised.
[0067] Optionally, the...
Embodiment 2
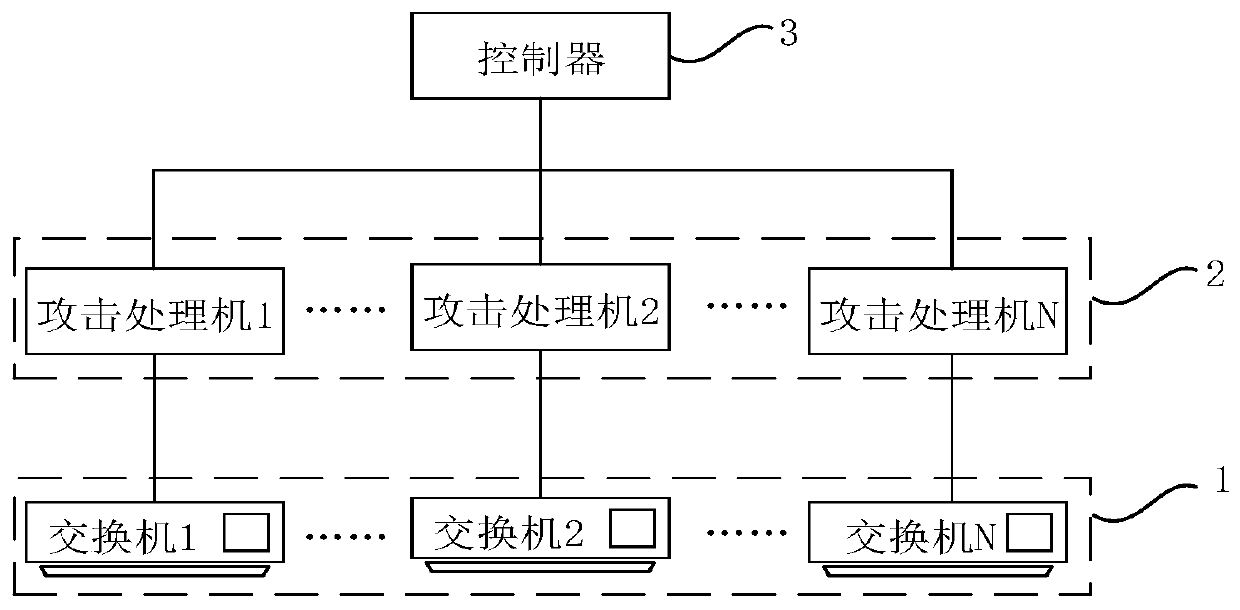
[0083] Such as Figure 5 Shown is a schematic diagram of a network system scenario provided by an embodiment of the present invention. This network is also applicable to the attack detection network. Compared with Embodiment 1, the difference is that first, multiple terminals are connected to a switch to form a local area network, wherein each local area network is configured with an attack processor. Secondly, multiple identical local area networks are set up, and the network system provided by this embodiment is obtained by connecting multiple local area networks with the controller, so as to realize the purpose of distributed detection of multiple terminals, thereby reducing the scope of attack , to ensure the normal operation of the network, and at the same time, because multiple switches are connected to the attack processor one by one, it can quickly respond to determine whether there is a network attack on the terminal, improve the anti-attack ability of the attack dete...
Embodiment 3
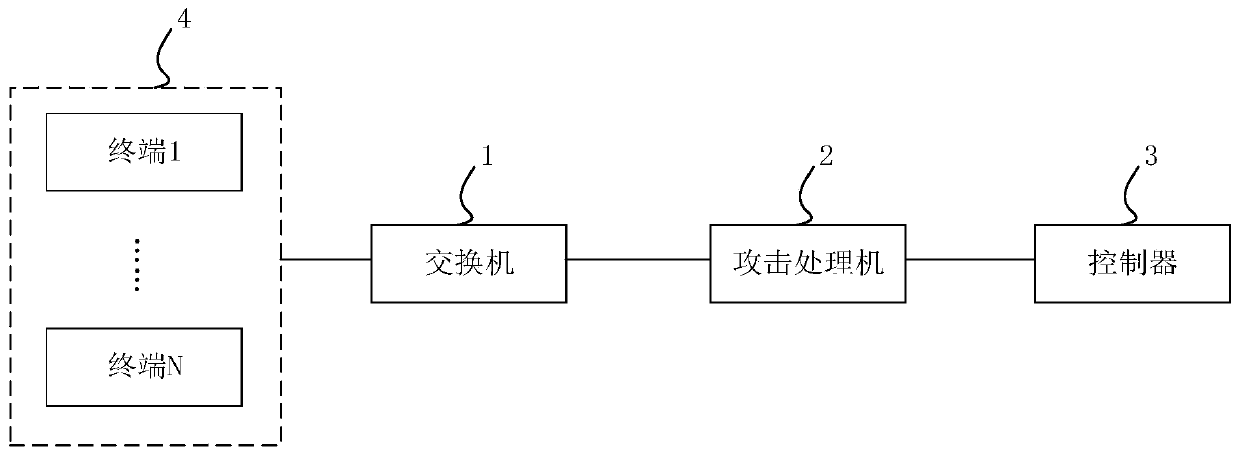
[0113] Such as Figure 11 As shown, it is a flow chart of an attack detection method provided by Embodiment 3 of the present invention. It involves the interaction process among terminals, switches, attack processors, and controllers. Taking the SDN network as an example, it is set up as the network system proposed in Embodiment 1, and the devices implementing the attack detection method include: OpenFlow switches, SDN controllers, attack processors and terminals (computer hosts). The specific steps of its attack detection method refer to Figure 11 Shown:
[0114] S40, the attack processor receives the message sent from the OpenFlow switch: an attack processor is inserted between the traditional OpenFlow switch and the SDN controller, and the attack processor is transparent to the switch / controller, that is, the connection between the switch and the controller The address of the interactive message between them will not reflect the existence of the attacking processor. Th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com