Identity authentication method based on power distribution
A technology of identity authentication and electric power, applied in electrical components, transmission systems, information technology support systems, etc., can solve problems such as inconvenient operation, complex dynamic password implementation, and easy cracking, and achieve the effect of improving the security level
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
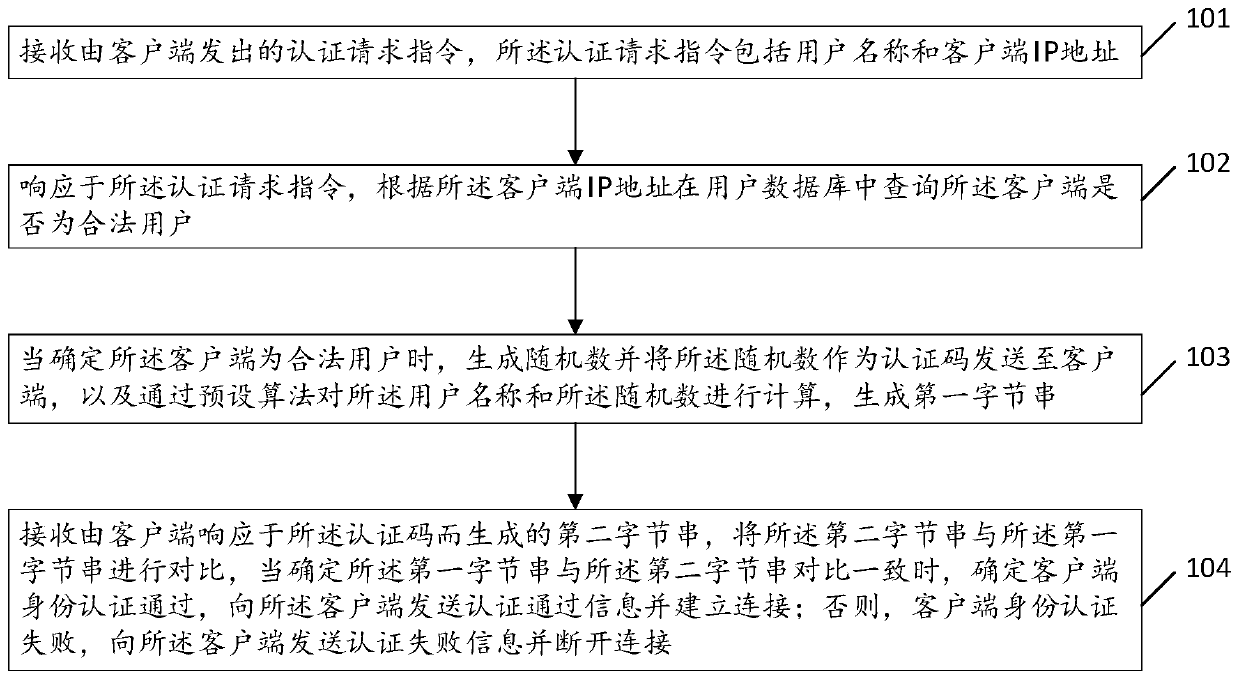
[0030] Please refer to figure 1 , is a flow diagram of an embodiment of an identity authentication method based on power distribution provided by the present invention, the method includes steps 101 to 104, and is executed by the authentication server, and each step is specifically as follows:
[0031] Step 101, receiving an authentication request instruction sent by a client, where the authentication request instruction includes a user name and an IP address of the client.
[0032] Step 102, in response to the authentication request instruction, query whether the client is a legitimate user in the user database according to the client IP address; in this embodiment, when it is determined that the client is an illegal user, and The client disconnects.
[0033] Step 103, when it is determined that the client is a legitimate user, generate a random number and send the random number to the client as an authentication code, and calculate the user name and the random number throug...
Embodiment 2
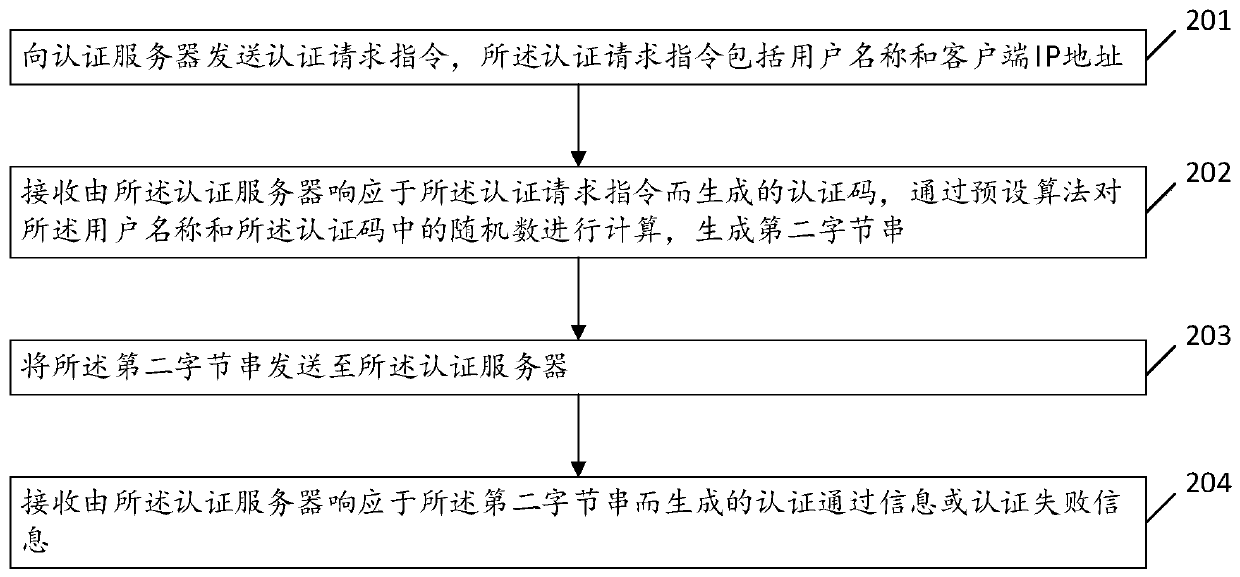
[0038] Please refer to figure 2 , is a flow diagram of another embodiment of the identity authentication method based on power distribution provided by the present invention, the method includes steps 201 to 204, executed by the client, and each step is specifically as follows:
[0039] Step 201, sending an authentication request instruction to an authentication server, where the authentication request instruction includes a user name and a client IP address.
[0040] Step 202, receiving the authentication code generated by the authentication server in response to the authentication request instruction, calculating the user name and the random number in the authentication code through a preset algorithm, and generating a second byte string; In this embodiment, the preset algorithm includes a one-way Hash function or a digital signature. In this embodiment, the one-way Hash function is the MD5 algorithm.
[0041] Step 203, sending the second byte string to the authentication...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com