Malicious software classification method based on PE head visualization
A malware and classification method technology, applied in computer parts, instruments, biological neural network models, etc., can solve problems such as time-consuming, poor practicability, and proliferation of malware attacks, and achieve fast classification speed and high classification accuracy. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0023] The present invention will be further described below in conjunction with the accompanying drawings.
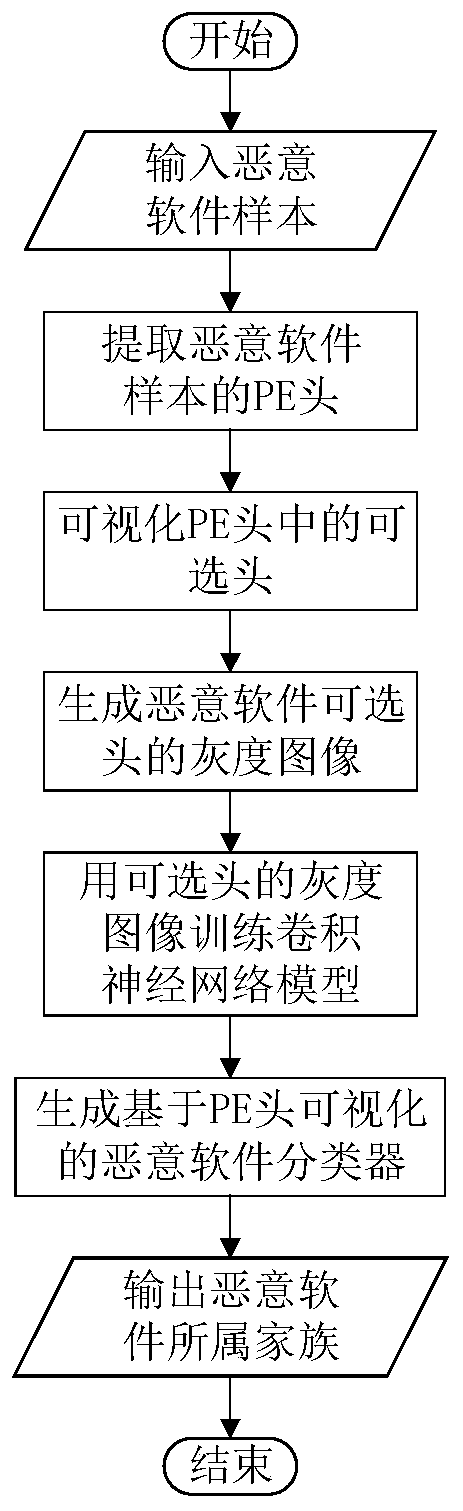
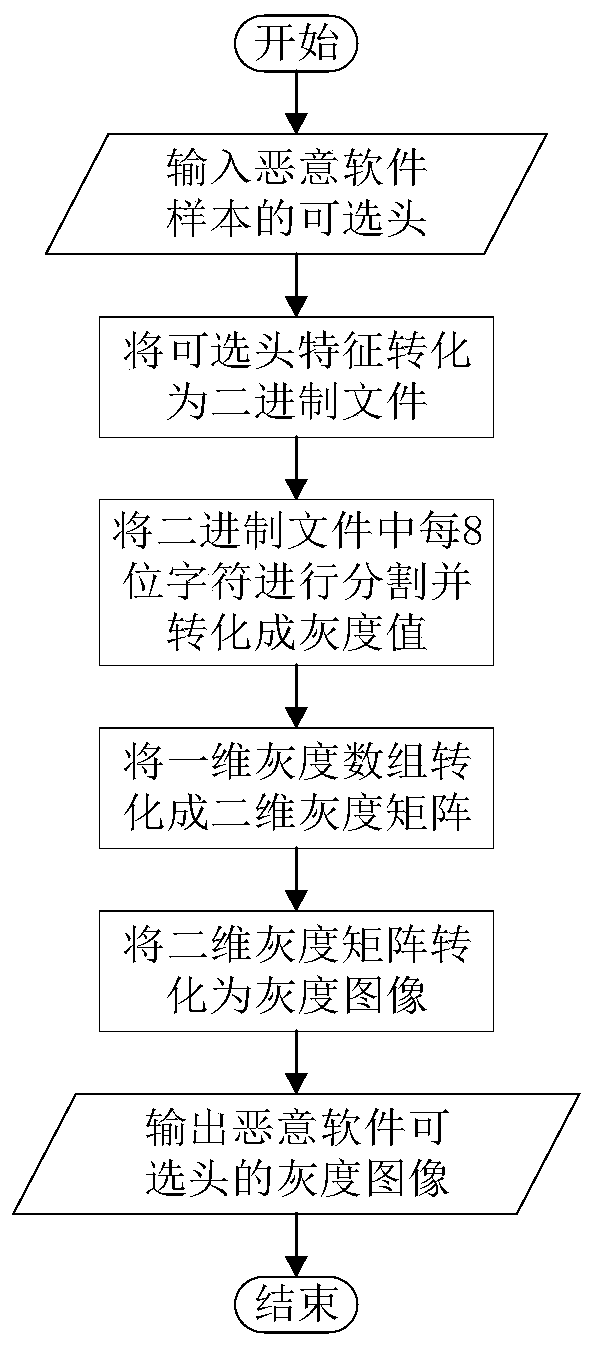
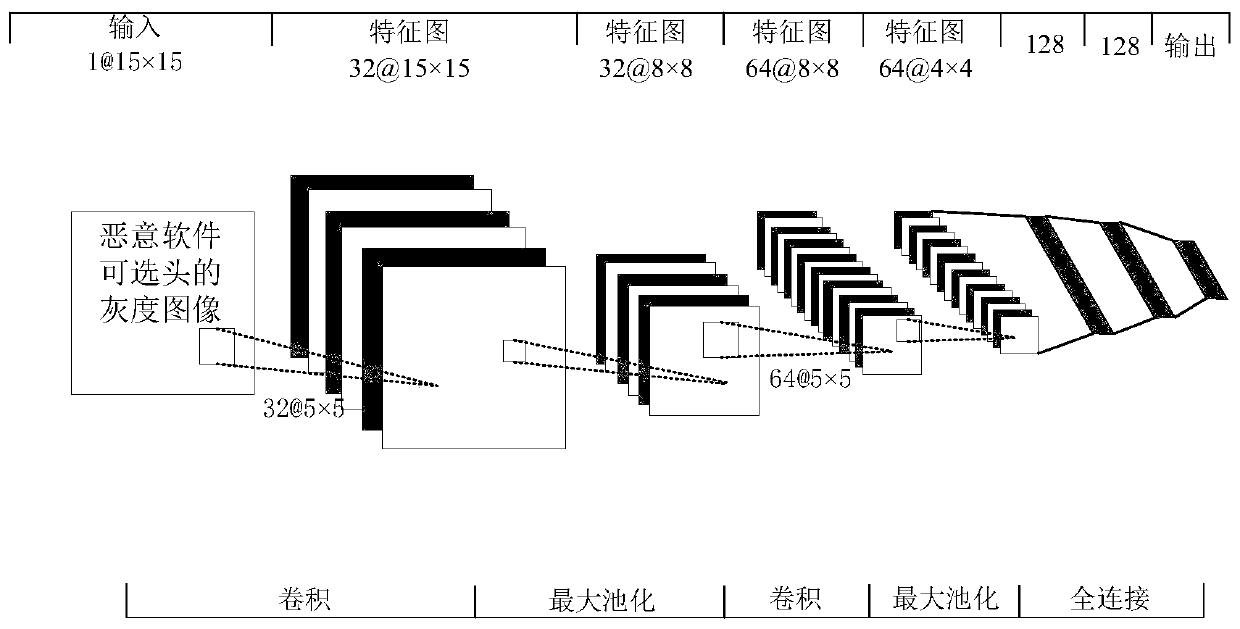
[0024] The invention provides a malicious software classification method based on PE header visualization. Extract features of recognizable DOS headers, DOS stubs, pNT headers, optional headers, and section tables from PE headers of malware, convert optional header features into binary files, and visualize them to generate malware images And train the convolutional neural network model to obtain an effective convolutional neural network classifier based on PE header visualization to identify malware families. The purpose of the present invention is to provide a method based on identifying and classifying malicious software, which has higher classification accuracy and faster classification speed.
[0025] A malware classification method based on PE header visualization, including four aspects.
[0026] (1) From the PE header of the malware, the features of the identi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com