Operator data security sharing method
A technology for data security and operators, applied in secure communication devices, digital transmission systems, encryption devices with shift registers/memory, etc., can solve problems such as loss, terminal hardware loss, Trojan horse virus theft, etc., and achieve fine-grained permissions , The effect of facilitating targeted management
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
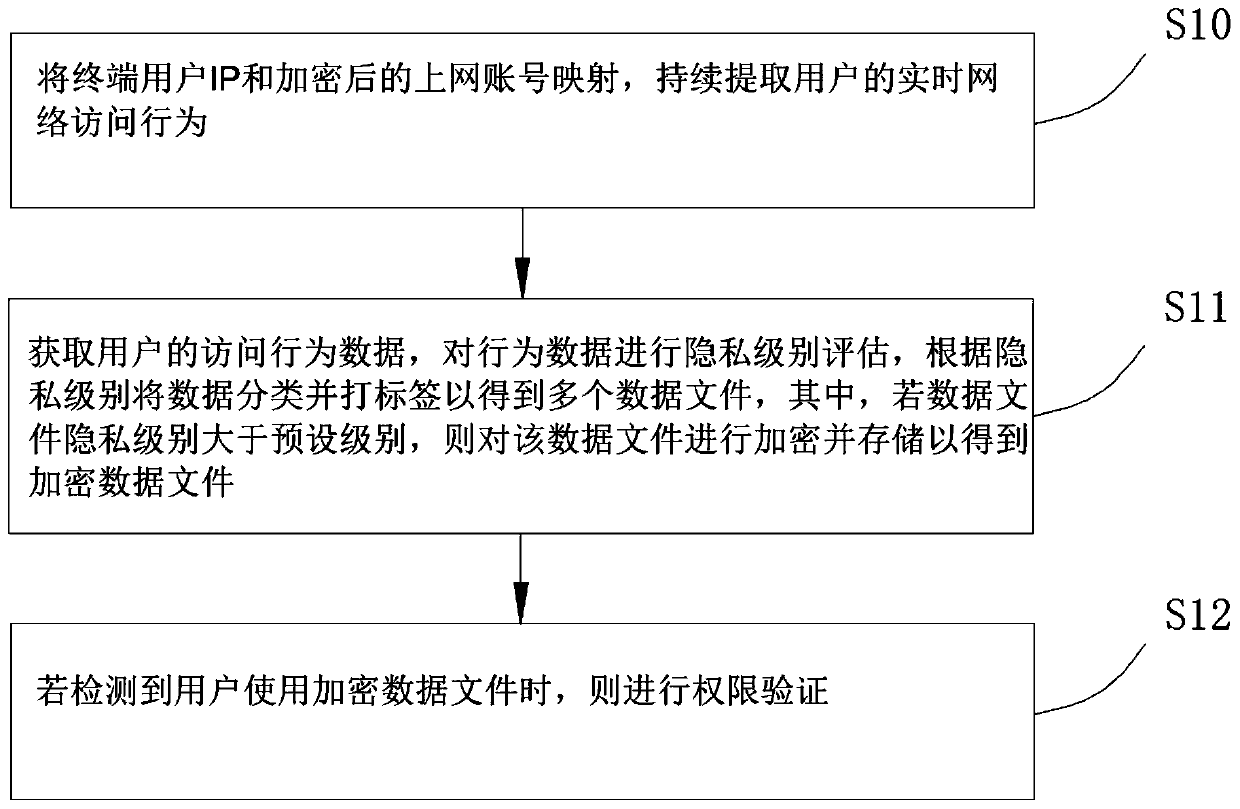
[0037] Please refer to figure 1 , the present embodiment provides a method for safely sharing operator data, including the following steps:
[0038] S10: Map the end user IP with the encrypted online account, and continuously extract the user's real-time network access behavior;
[0039] S11: Obtain the user's access behavior data, evaluate the privacy level of the behavior data, classify and label the data according to the privacy level to obtain multiple data files, and if the privacy level of the data file is greater than the preset level, then the data file Encrypt and store to obtain encrypted data files;
[0040] S12: Perform permission verification if it is detected that the user uses the encrypted data file.
[0041] Design principle: After long-term research and practice, the inventor found that in the existing technology, in order to facilitate query and analysis, the operator needs to share the collected user data, which is not conducive to the protection of user ...
Embodiment 2
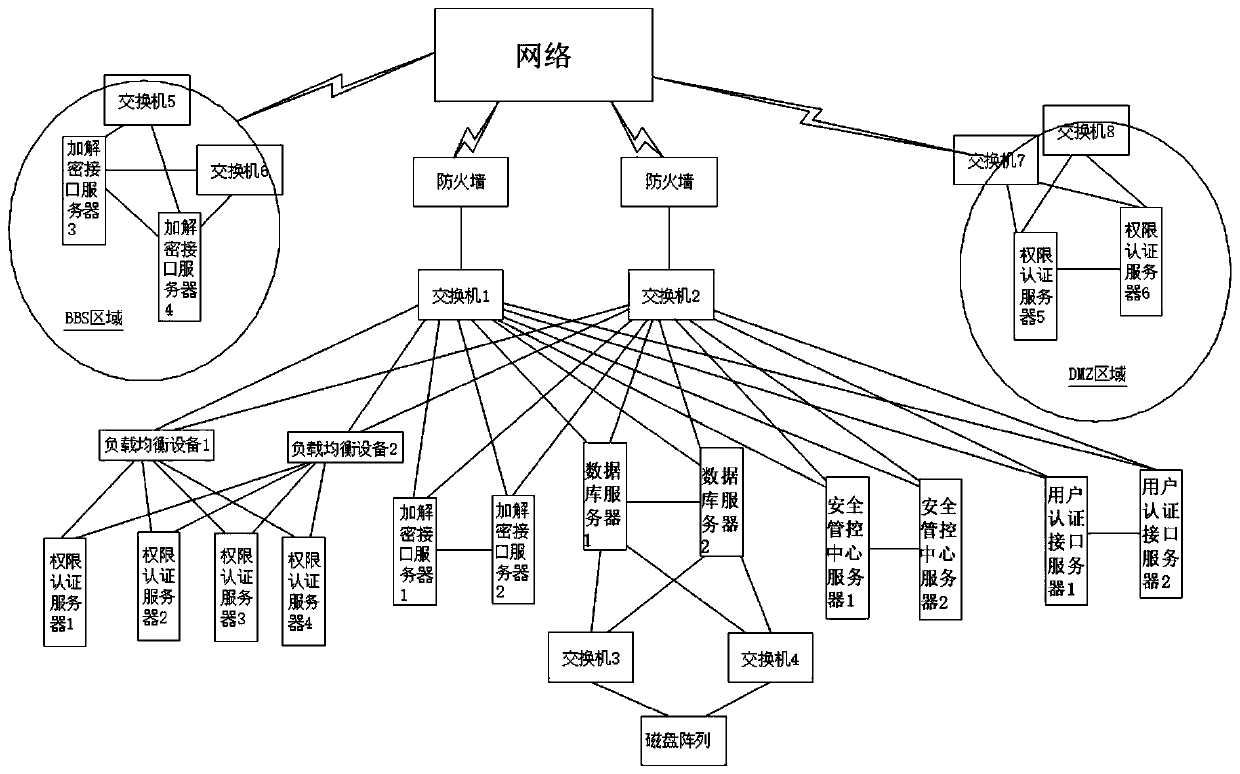
[0047] Please refer to figure 2 , the difference between this embodiment and Embodiment 1 is that a method for safely sharing operator data further includes setting: a security management and control center server, an authority authentication server, an encryption and decryption interface server, a user authentication interface server, and a database server; the security management and control center There are multiple servers, and the present embodiment is preferably provided with 2, which are respectively a security management and control center server 1 and a security management and control center server 2. Switch 1 and switch 2 are connected, and switch 1 and switch 2 are connected to the network through a firewall. The security management and control center server is used to manage encrypted data files, and the management includes hierarchical user rights management. The purpose of such setting is to improve the security management capability of the operator's core data ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com