Method and system for judging network access legality of local area network terminal equipment
A technology of terminal equipment and local area network, applied in the field of power information security, can solve the problems of neglecting the forgery of MAC addresses and lack of universality of terminal types, so as to improve the universality and matching accuracy, improve the vulnerability, and strengthen the The effect of reliability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
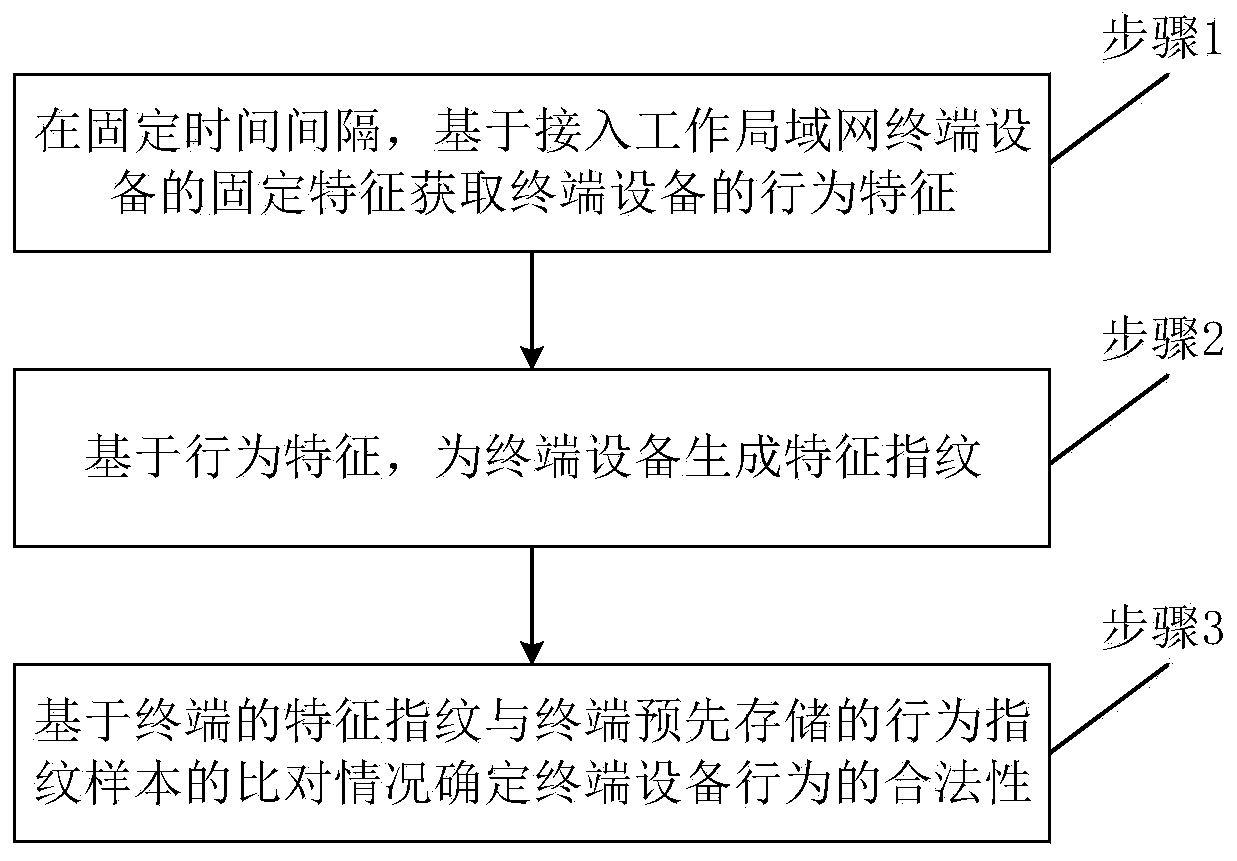
[0047] The flow chart of a method for judging the legitimacy of a network access feature fingerprint of a local area network terminal device provided by the present invention is as follows: figure 1 shown, including:
[0048] Step 1: Obtain the behavior characteristics of the terminal device based on the fixed characteristics of the terminal device connected to the working LAN at a fixed time interval;
[0049] Step 2: Generate characteristic fingerprints for terminal devices based on behavioral characteristics;
[0050] Step 3: Determine the legitimacy of the behavior of the terminal device based on the comparison between the characteristic fingerprint of the terminal and the behavioral fingerprint samples stored in the terminal in advance.
[0051]First of all, in terms of the selection of equipment features, this application lists the fixed features and dynamic behaviors included in the marketing site terminal equipment, and selects active, passive, or a combination of act...
Embodiment 2
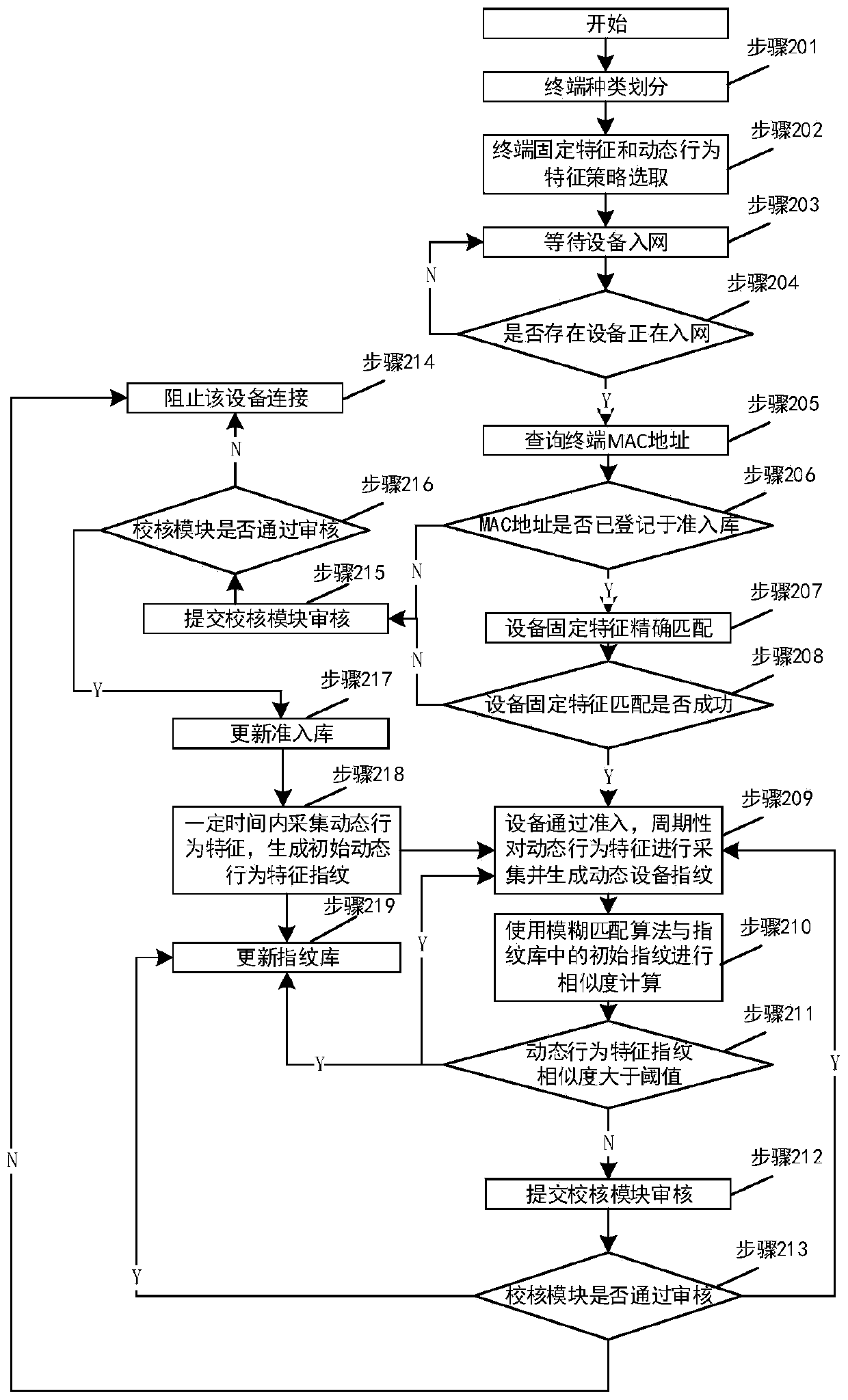
[0072] Attached below figure 2 , giving an embodiment of a method for judging the legality of network access feature fingerprints of a local area network terminal device.
[0073] After the legality determination method process of LAN terminal equipment network feature fingerprints starts, it includes:
[0074] Step 201: Classify terminal types.
[0075] Step 202: Strategy selection of terminal fixed features and dynamic behavior features.
[0076] That is, for various types of terminals in the terminal type list, appropriate terminal fixed features are selected for them.
[0077] Step 203: Waiting for the device to access the network.
[0078] The device in this embodiment is also a terminal.
[0079] Step 204: Determine whether there is any device that is connecting to the network: if yes, go to step 205; otherwise, go to step 203.
[0080] Step 205: Query the MAC address of the terminal.
[0081] Step 206: Determine whether the MAC address has been registered in the ...
Embodiment 3
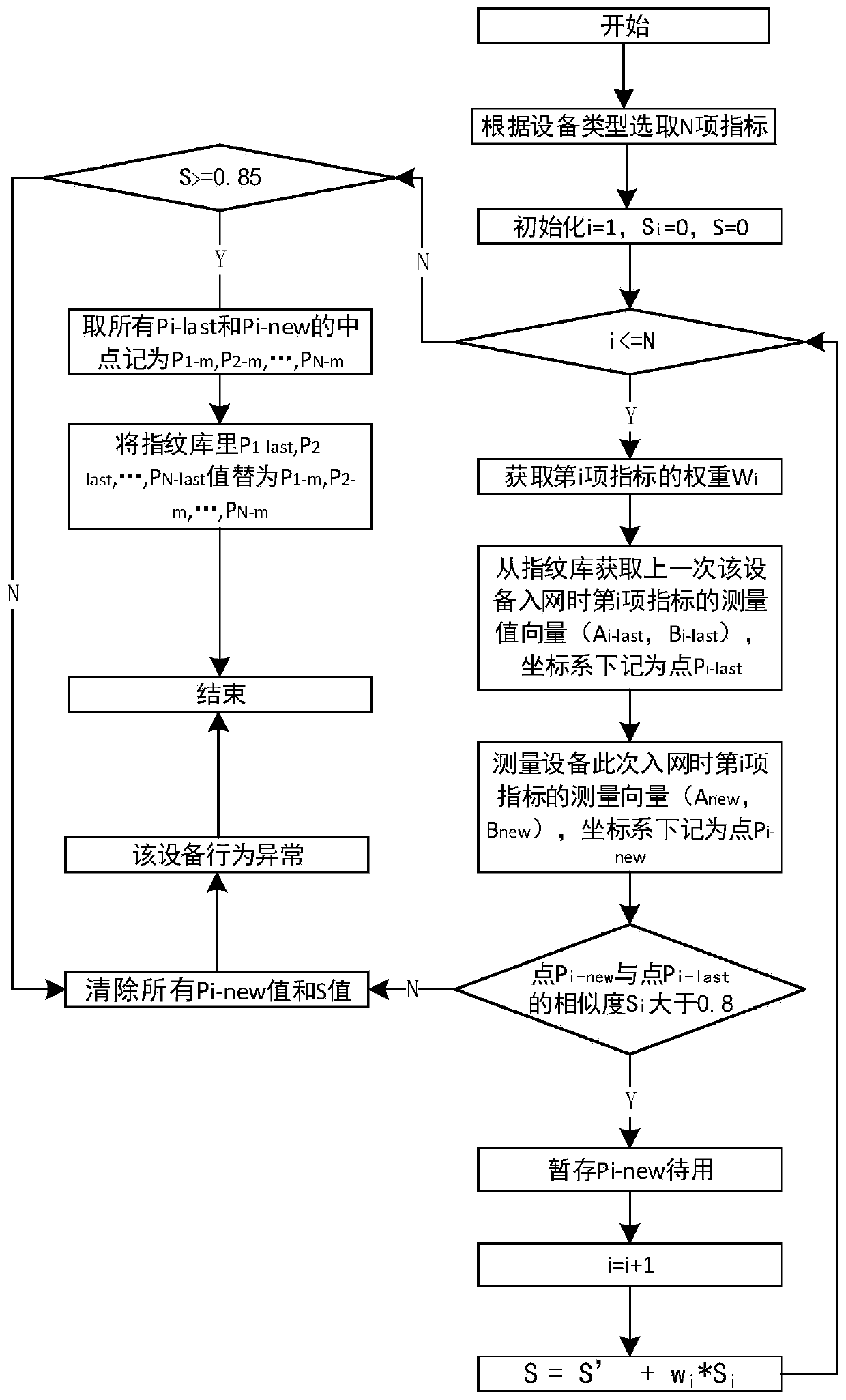
[0096] A specific embodiment of a method for judging the legality of network access feature fingerprints of a local area network terminal device is given below.
[0097] Step 301: Conduct a research on terminal types for a power marketing outlet, and find that the terminal types are divided into work computers, marketing payment terminals, printers, cameras, POS machines, and card punching devices.
[0098] Step 302: Bypass deploying the terminal admission system using this method at the core switch, and mirroring all data traffic passing through the core switch through the mirror port.
[0099] Step 303: Configure corresponding terminal fixed features and terminal dynamic behavior features for each type of terminal, for example: configure all terminal features as shown in Table 1 and Table 2 for computer terminals.
[0100] Step 304: Prepare two computers with identical models and identical operating systems as test machines. Computer A is connected to the local area network...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com