Intermediary physical isolation method and system applied to USB interface
A USB interface and physical isolation technology, applied in the field of electronic information security, can solve the problems of USB device HID masquerade attack and 0-day vulnerability attack that cannot be prevented, and achieve the effect of preventing and controlling information security problems and ensuring safe and stable operation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0036] The current USB protection measures include disabling the USB interface and using various firewalls and monitoring software to control the security of the USB interface. However, these two protection measures cannot effectively avoid potential information security risks while meeting work requirements.
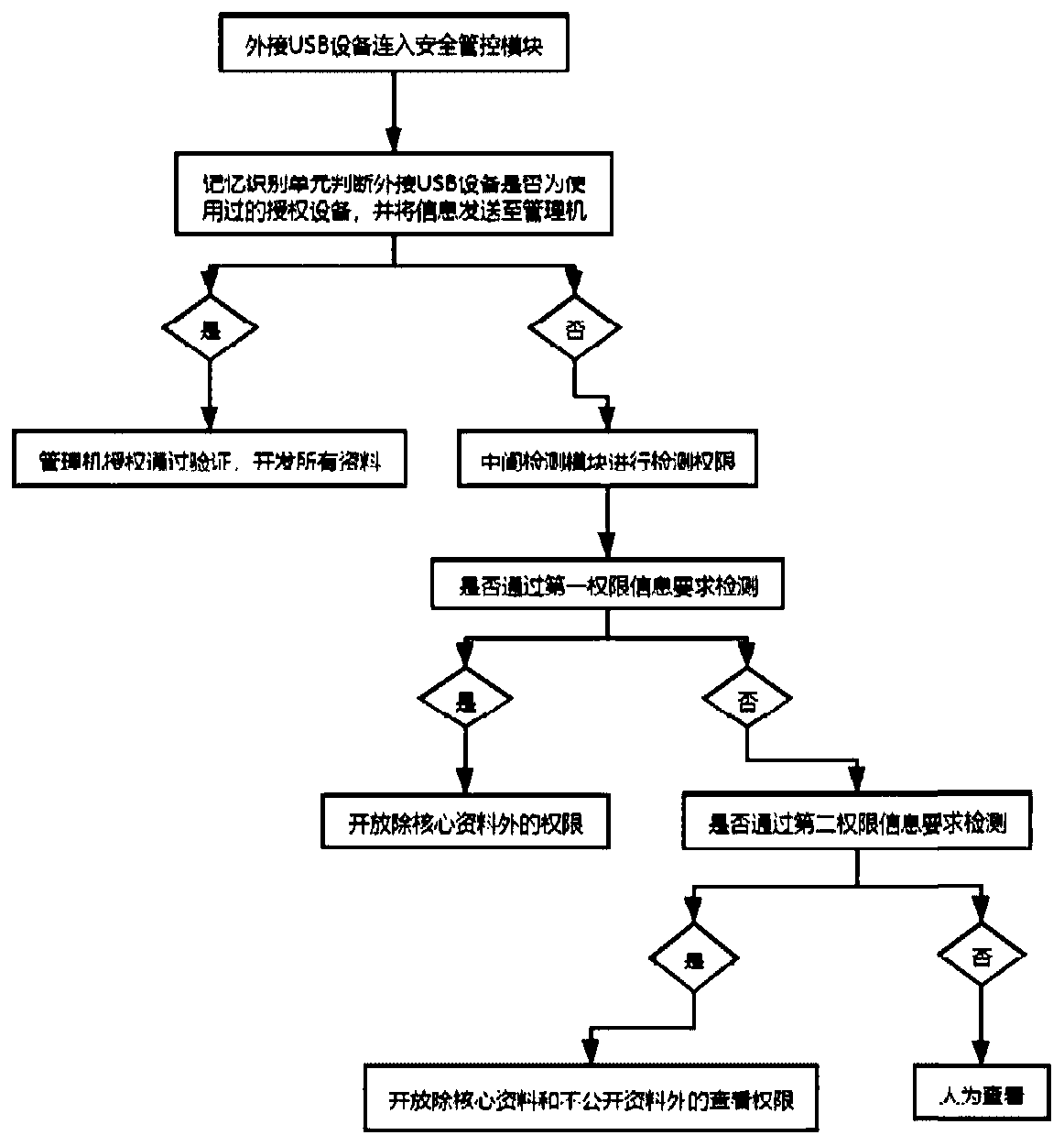
[0037] Therefore, please refer to figure 1 , image 3 , Figure 4 and Figure 8 , for the present invention proposes a kind of intermediary type physical isolation method applied to USB interface: a kind of intermediary type physical isolation method applied to USB interface, comprising:
[0038] The external USB device is connected to the security control module 100, and the memory identification unit judges whether the external USB device is a used authorized device, and sends the information to the management machine 200;
[0039] The management machine 200 receives the information and makes a verification judgment. If it is an authorized device, the management ma...
Embodiment 2
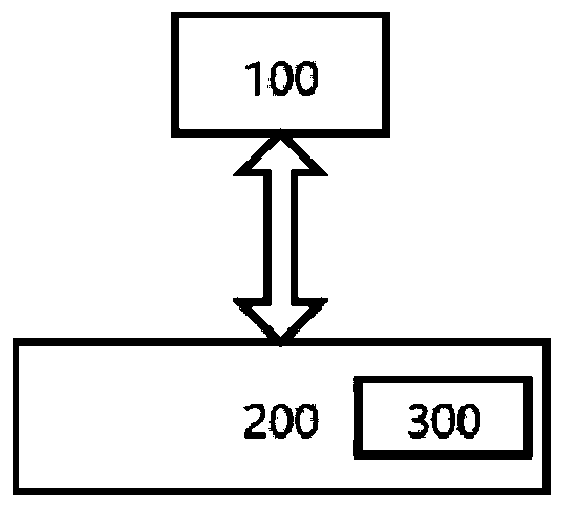
[0091] see figure 2 and Figure 5-9 , the first embodiment of the intermediary physical isolation system applied to the USB interface provided by the present invention: an intermediary physical isolation system applied to the USB interface, comprising:
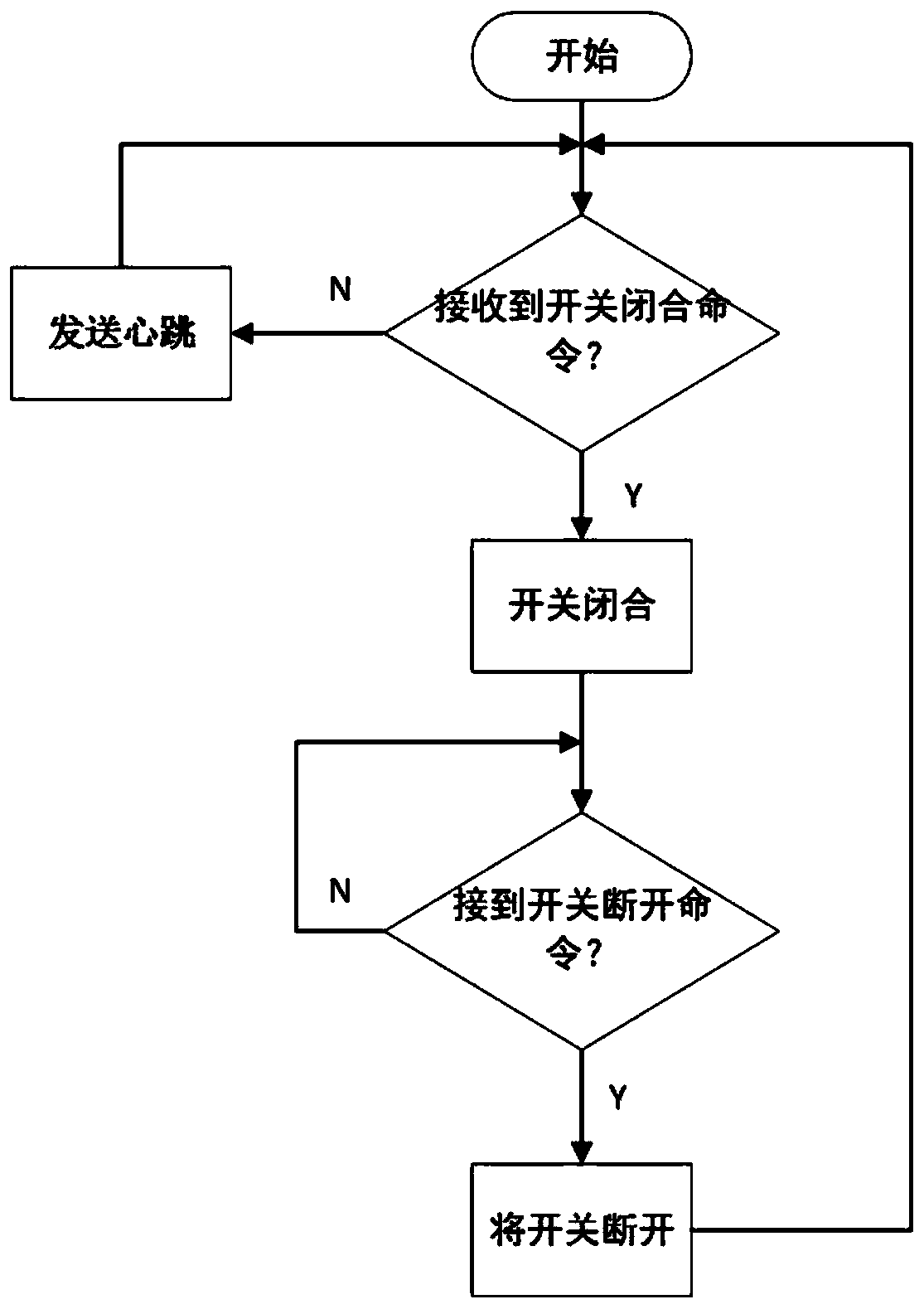
[0092] The safety management and control module 100 communicates with the management machine 200 wirelessly, and cuts off or connects the power cord of the USB interface according to the control instruction of the management machine 200;
[0093] The management machine 200 is used to manage all the security management and control modules 100, control the on-off of each USB interface according to user needs, provide the functions of authority management, interface display, real-time alarm and query history, and send a notification message when necessary to the user;
[0094] The intermediate detection module 300 is connected with the management machine 200 and the security management and control module 100, and is used to de...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com