4G communication encryption algorithm based on time
An encryption algorithm and time information technology, which is applied in wireless communication, multiplexing communication, time division multiplexing system, etc., to improve the efficiency and reliability of interaction, and prevent forged messages from interfering with the normal communication process.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
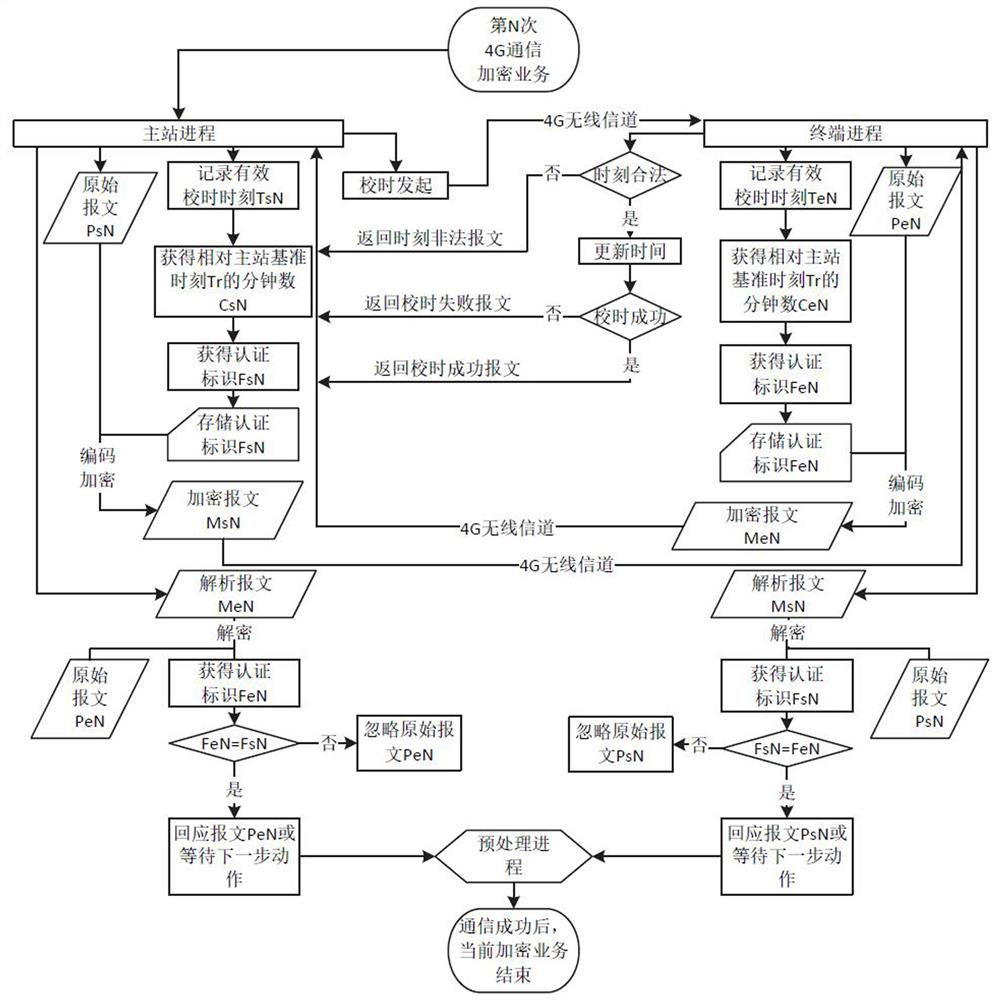
[0028] The technical scheme of the present invention is described in detail below in conjunction with accompanying drawing:
[0029] Such as figure 1 , a time-based 4G communication encryption algorithm, used for 4G network communication between the master station and the terminal, taking the master station sending ciphertext and then the terminal responding as an example, the steps are:
[0030] (1) Before the master station and the terminal exchange messages that need to be encrypted, the master station and the terminal first check the time. The specific steps are:
[0031] (1.1) The master station initiates a timing command;
[0032] (1.2) After the terminal receives the time adjustment command, it judges the legitimacy of the time adjustment according to the preset logic. If the time adjustment is legal, go to step (1.3), otherwise go to step (1.4);
[0033] (1.3) Terminal update time: If the update is successful, it will return a time-calibration success message, and th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com