Method for calculating vulnerability risks
A vulnerability and risk technology, applied in the field of computing vulnerability risk, can solve problems such as lack of professionalism and experience of assessors, non-standard and inconsistent risk assessment standards, and incomplete assessment results, so as to improve development specifications and requirements and improve development quality , the effect of avoiding economic loss and reputation risk
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
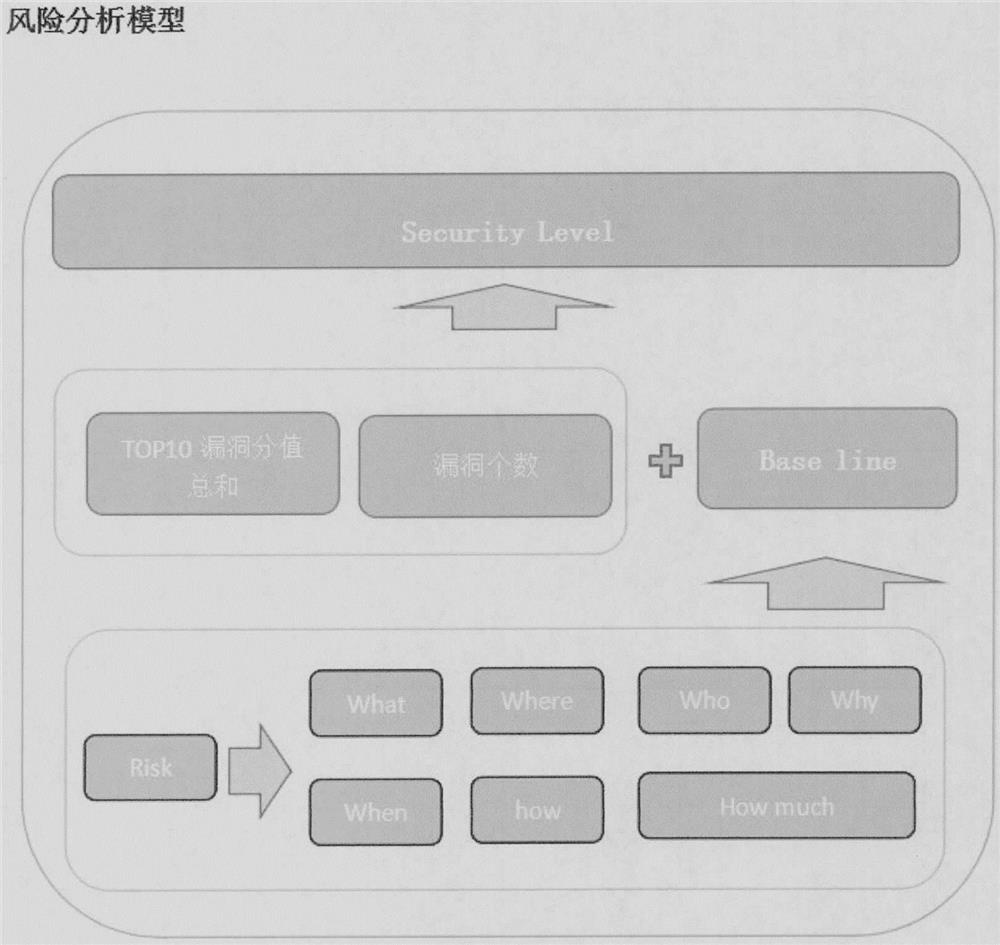
[0067] Please refer to the accompanying drawings of the specification. A method for calculating vulnerability risk in an embodiment of the present invention includes the following methods:
[0068] S1. Standardize the vulnerability level;
[0069] S2, the hazard level of vulnerabilities combined with the seven-ho analysis method to standardize the evaluation dimensions;
[0070] S3. Standardization of the baseline;
[0071] S4. Perform a matching analysis on the risk values between the standardization in S1, S2, and S3 and the enterprise systems, and draw a conclusion.
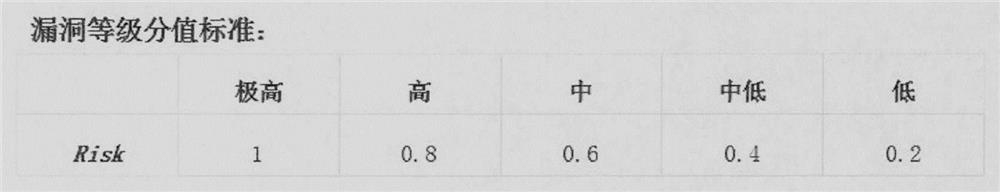
[0072] Further, the vulnerability levels in the S1 step are classified into extremely high-risk vulnerabilities, high-risk vulnerabilities, medium-risk vulnerabilities, medium-low-risk vulnerabilities, and low-risk vulnerabilities according to the vulnerability grade scoring standard.
[0073] Highly harmful leakage: mainly refers to the loopholes that directly cause damage to the target system of the enterprise, bring...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com