Decentralized identity management method in D2D scene in 5G environment
A decentralized, identity management technology, applied in the field of identity authentication, can solve problems such as privacy leakage, and achieve the effect of ensuring non-infringement
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
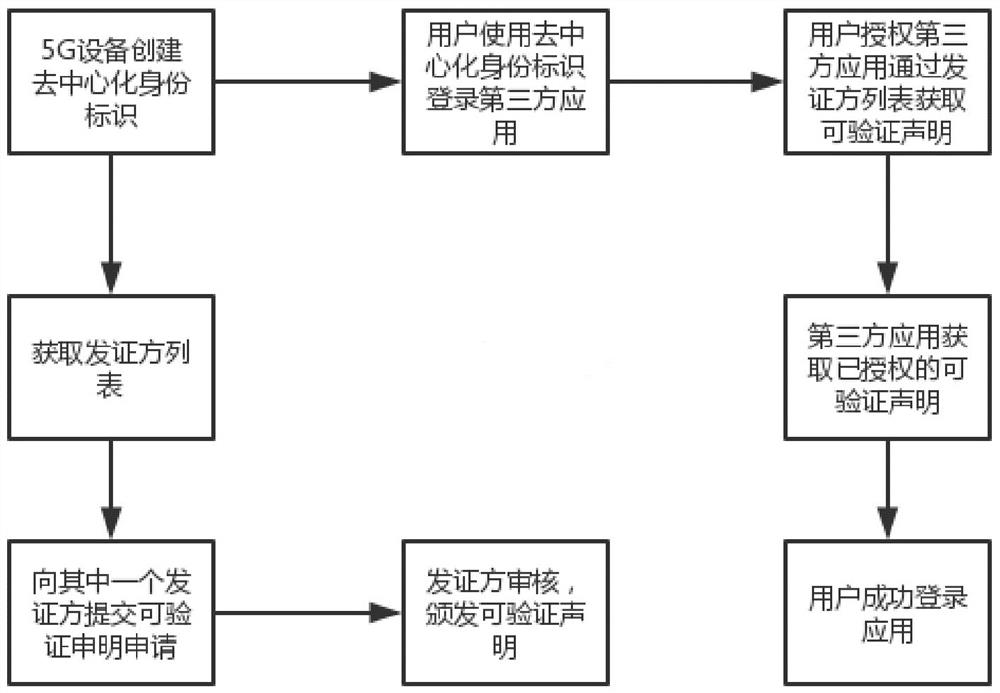
[0023] Such as figure 1 As shown, in this embodiment, a method for decentralized identity management in a 5G environment D2D scene includes the following steps:
[0024] S1: Users use the 5G device DID program to create their own DID;
[0025] S2: The user obtains the issuer list in the DID program;
[0026] S3: The user submits a verifiable statement application to a designated certificate issuer and provides relevant verification materials;
[0027] S4: After the certificate issuer has reviewed the materials, issue a verifiable statement to the user;
[0028] S5: The user uses DID to log in to the third-party application, and learns that the application requires the user to provide a verifiable statement;
[0029] S6: The user authorizes the third-party application to go to the identity center to obtain verifiable claims;
[0030] S7: the user successfully logs in to the third-party application.
[0031] In the 5G environment, 5G equipment is used to build a blockchain ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com