Android application maliciousness and malicious race detection model construction method and application
A technology for detecting models and building methods, applied in platform integrity maintenance, computer security devices, instruments, etc., can solve problems such as Android application code confusion and effective resistance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
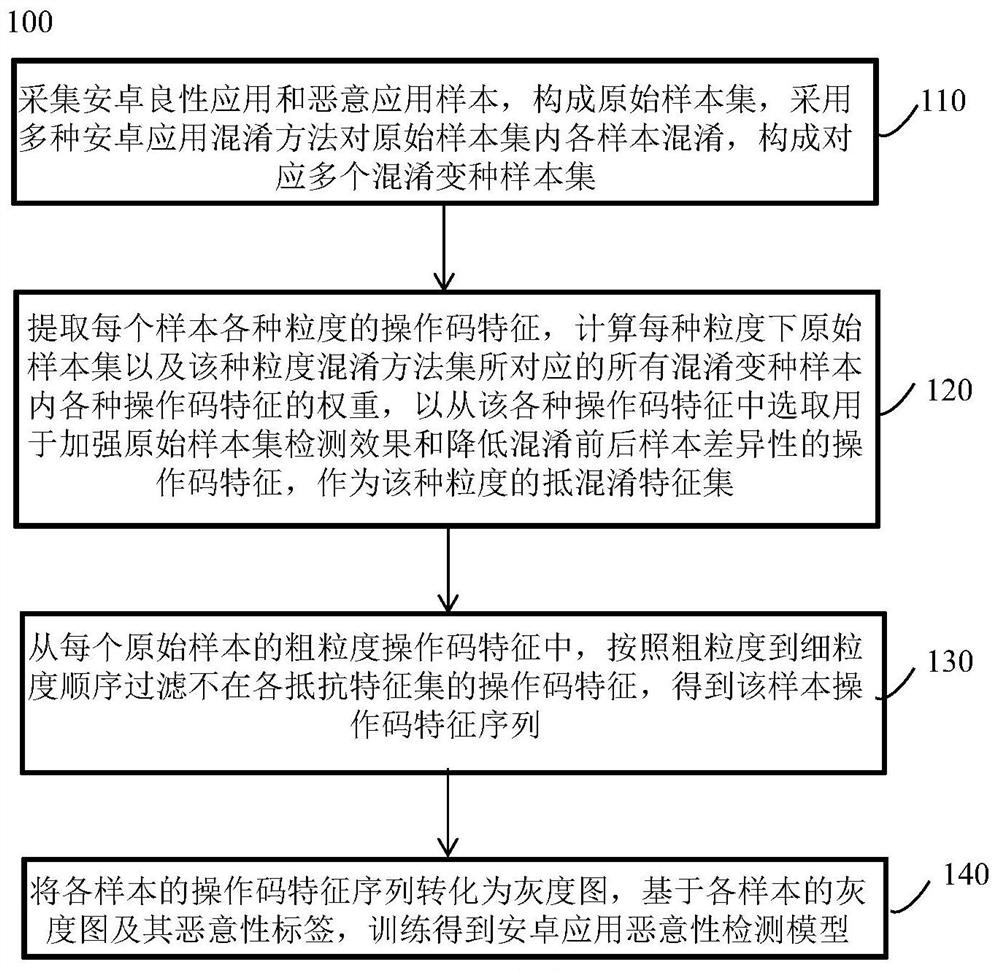
[0050] A construction method 100 of an Android application maliciousness detection model, such as figure 1 shown, including:
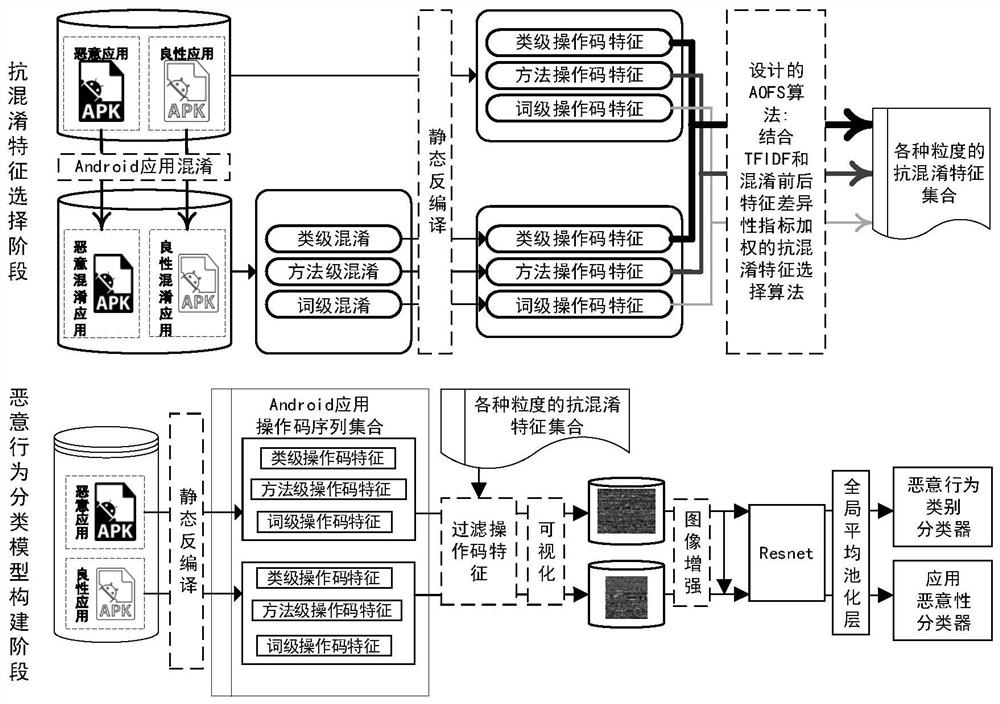
[0051] Step 110, collect Android benign application and malicious application samples to form an original sample set, and use multiple Android application obfuscation methods to confuse each sample in the original sample set to form a plurality of corresponding obfuscated variant sample sets;
[0052] Step 120, extracting the opcode features of various granularities of each sample, calculating the weights of various opcode features in the original sample set under each granularity and all obfuscated variant samples corresponding to the granularity obfuscation method set, to obtain from the Among the opcode features, the opcode features used to enhance the detection effect of the original sample set and reduce the difference between samples before and after confusion are selected as the anti-aliasing feature set of this granularity;
[0053] Step 130, ...
Embodiment 2
[0075] A method for detecting maliciousness of an Android application, comprising:
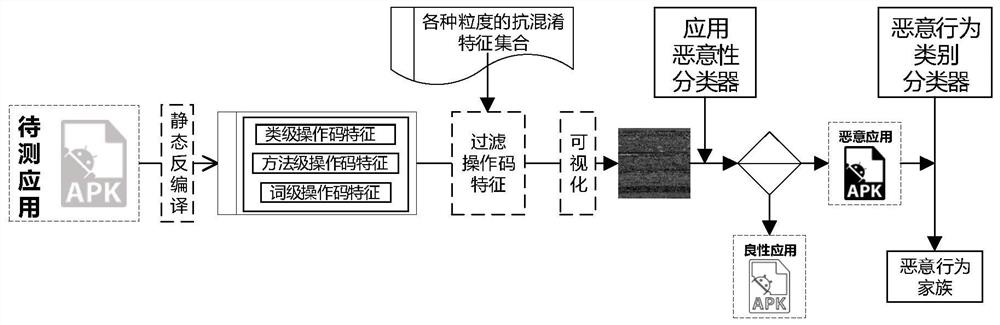
[0076] Decompile the Android application to be tested, extract the coarse-grained opcode features of the application, and filter the various codes that are not included in the construction method of an Android application malicious detection model described in the first embodiment above in order from coarse-grained to fine-grained. The opcode feature in the anti-aliasing feature set, the opcode feature sequence of the sample is obtained and converted into a grayscale image; the grayscale image is input into the construction of a malicious detection model for Android applications as described in the first embodiment The method constructs the maliciousness detection model of the Android application, and obtains the maliciousness of the Android application to be tested. The relevant technical solutions are the same as those in Embodiment 1, and will not be repeated here.
[0077] Decompile the A...
Embodiment 3
[0080] A method for constructing a malicious family detection model of an Android malicious application, based on the grayscale image of each malicious application sample in the original sample set and the corresponding malicious family label, trained to obtain a malicious family detection model for Android malicious applications. The relevant technical solutions are the same as those in Embodiment 1, and will not be repeated here.
[0081] Regarding the sample collection for the construction of the malicious family detection model of the Android malicious application, on the basis of the collection and construction of the original sample set A in the first embodiment, by marking the malicious family of the malicious application of the unmarked malicious family in the sample set A, you can Constitutes the malicious application label values used to train the Android malicious application malicious family detection model.
[0082] The operation code characteristic sequence of...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com