Cargo transport vehicle deployment system
A cargo transportation and vehicle technology, which is applied in the field of cargo transportation vehicle deployment system, can solve the problems of incapable vehicle scheduling demand analysis, and achieve the effect of improving the use experience.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
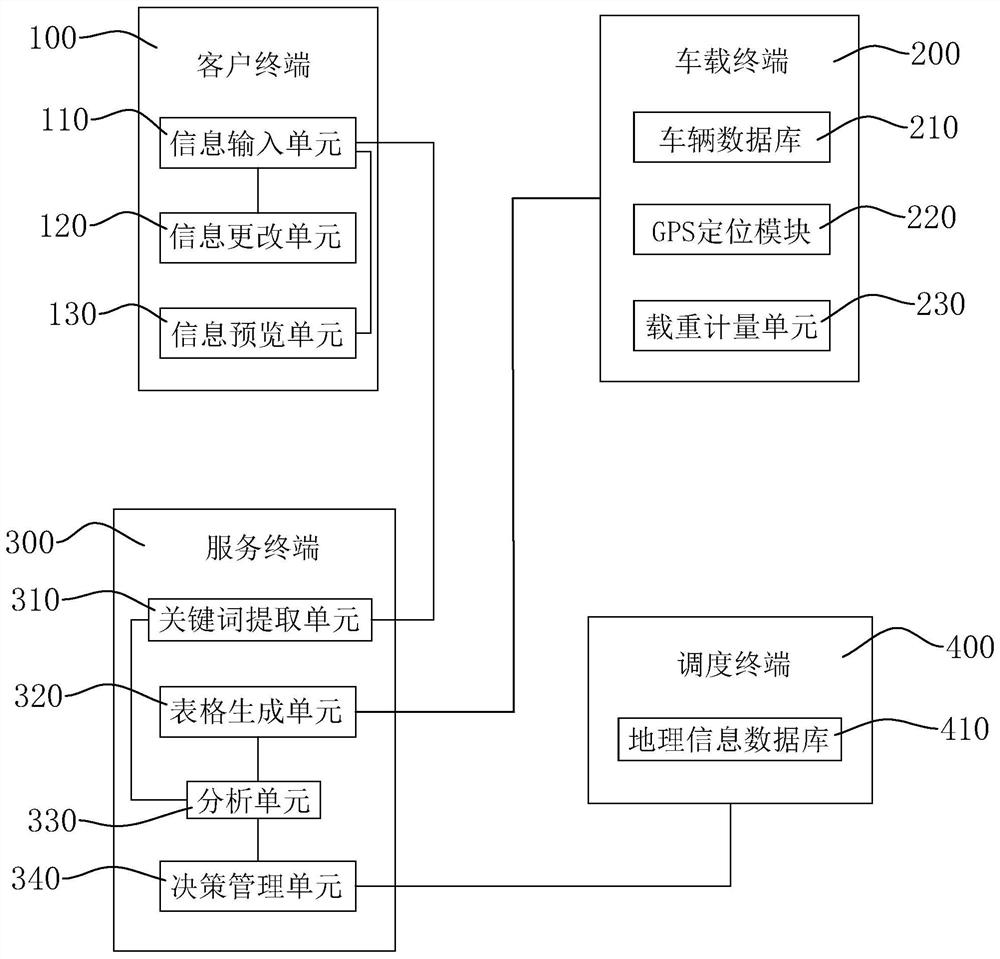
[0039] Please refer to figure 1 , is a cargo transportation vehicle deployment system disclosed in the present invention, as shown in the figure, including a client terminal 100, a vehicle terminal 200, a service terminal 300, and a dispatching terminal 400, and the client terminal 100 is connected to the service terminal 300 by communication, for connecting users The demand information of the vehicle is sent to the service terminal 300, and the vehicle-mounted terminal 200 communicates with the service terminal 300, and is used to send the operation information of the vehicle to the service terminal 300. The service terminal 300 generates a vehicle dispatching instruction according to the customer's demand information and the operation information of the vehicle. The dispatching terminal 400 communicates with the service terminal 300 and is used to receive the vehicle dispatching instruction from the service terminal 300 to complete the dispatching of the vehicles.
[0040] W...
Embodiment 2
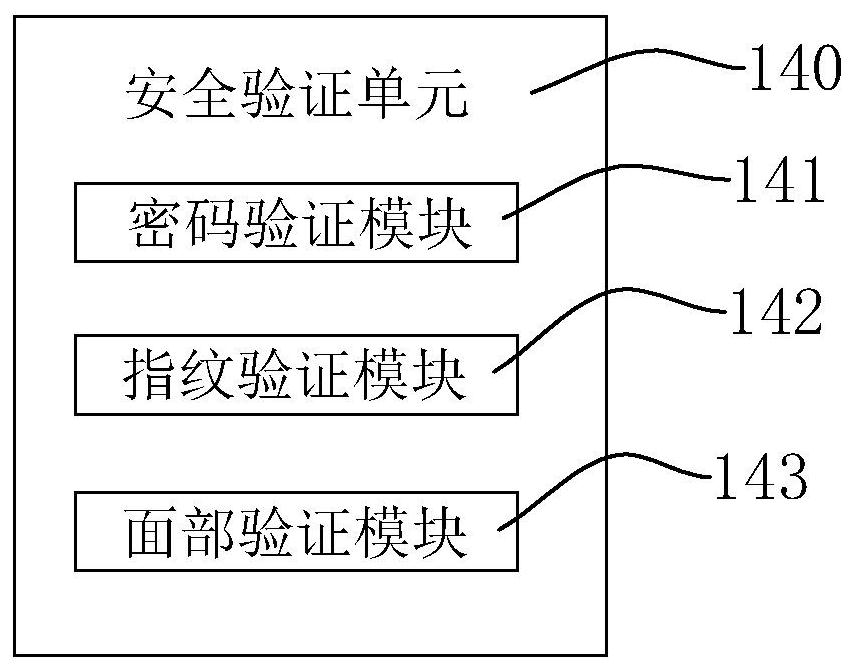
[0046] Please refer to figure 2 , is another embodiment of the present invention, as shown in the figure, the difference between this embodiment and the previous embodiment is that the client terminal 100 also includes a security verification unit 140, which is used to verify the identity information of the user, so as to prevent the client from The terminal 100 is stolen, causing losses to the user. Specifically, the security verification unit 140 includes a password verification module 141, a fingerprint verification module 142, and a face verification module 143. Of course, according to different usage requirements, one of the above three verification modules can be selected arbitrarily. At least one, preferably, in order to enhance the security of the client terminal 100, the password verification module 141, the fingerprint verification module 142 and the face verification module 143 are all put into use, that is, only all of the password verification, fingerprint verific...
Embodiment 3
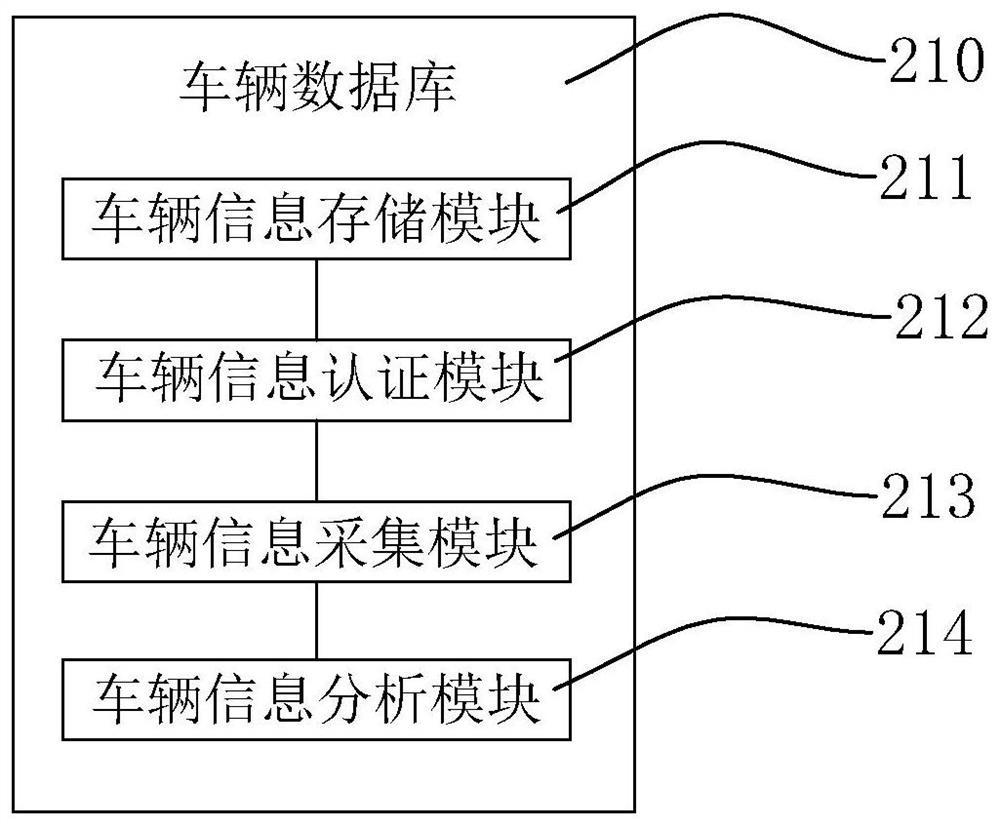
[0048] Please refer to image 3 , is another embodiment of the present invention, as shown in the figure, the difference between this embodiment and the previous embodiment is that the vehicle database 210 includes a vehicle information storage module 211, a vehicle information authentication module 212, and a vehicle information collection module 213 And the vehicle information analysis module 214, specifically, the vehicle information storage module 211 communicates with the vehicle information authentication module 212, the vehicle information authentication module 212 communicates with the vehicle information collection module 213, and the vehicle information collection module 213 communicates with the vehicle information analysis module 214 connection, more specifically, the vehicle information storage module 211 is used to store vehicle identity information, the vehicle information authentication module 212 is used to authenticate the vehicle and generate vehicle authenti...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com