Asset safety assessment method and system based on intelligence analysis
A security assessment and asset technology, applied in the field of network security, can solve the problems of high registration cost, inability to effectively evaluate the security status of digital assets, slow update speed, etc., and achieve the effect of convenient deployment and defense strategy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0034] The preferred embodiments of the present invention will be described in detail below in conjunction with the accompanying drawings, so that the advantages and features of the present invention can be more easily understood by those skilled in the art, so as to define the protection scope of the present invention more clearly.
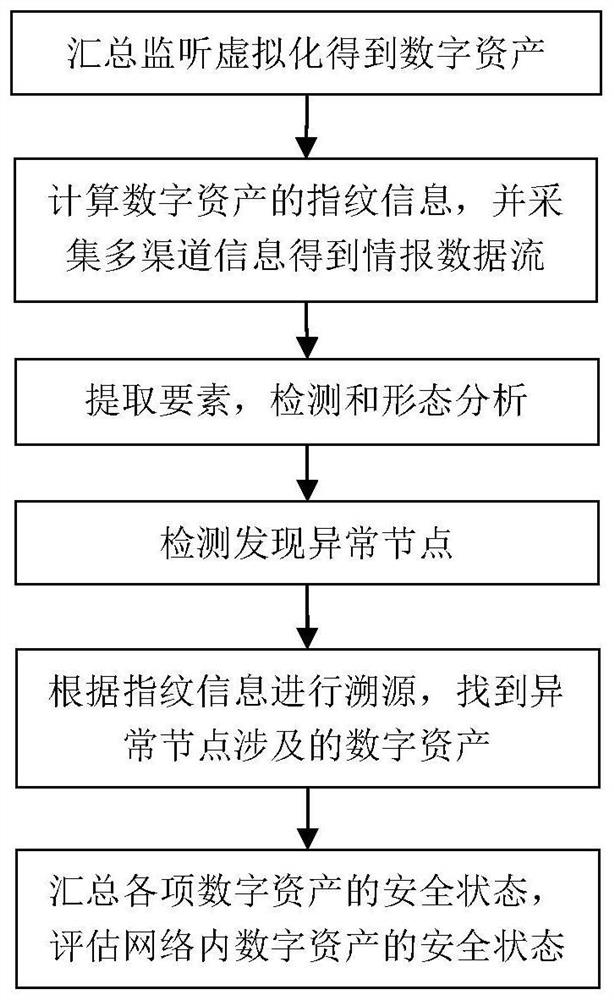
[0035] figure 1 A general flow chart of the asset security assessment method based on intelligence analysis provided by this application, the method includes:
[0036] The edge layer collects equipment asset data, including the files stored in each network node, the key stored in the database, the mapping relationship table stored in the database, the email address of the local area network, and the IP address of each network node. Tables, email addresses, and IP addresses are respectively virtualized into single second-class digital assets one by one, and file names, key abstracts, table names, email addresses, and IP addresses are respectively ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com